Trusted by










Why Syskit Point?
Syskit Point takes the guesswork out of administering cloud collaboration and managing Microsoft 365. It helps you avoid costly breaches, hefty fines, arduous regulatory compliance, and unnecessary expenditures caused by data leaks, exposed sensitive information, and excessive storage consumption.
Our platform gives you a centralized solution for all these situations, keeping your business secure, compliant, and cost-optimized.
Do you have a clear picture of what’s happening in your Microsoft 365 estate?
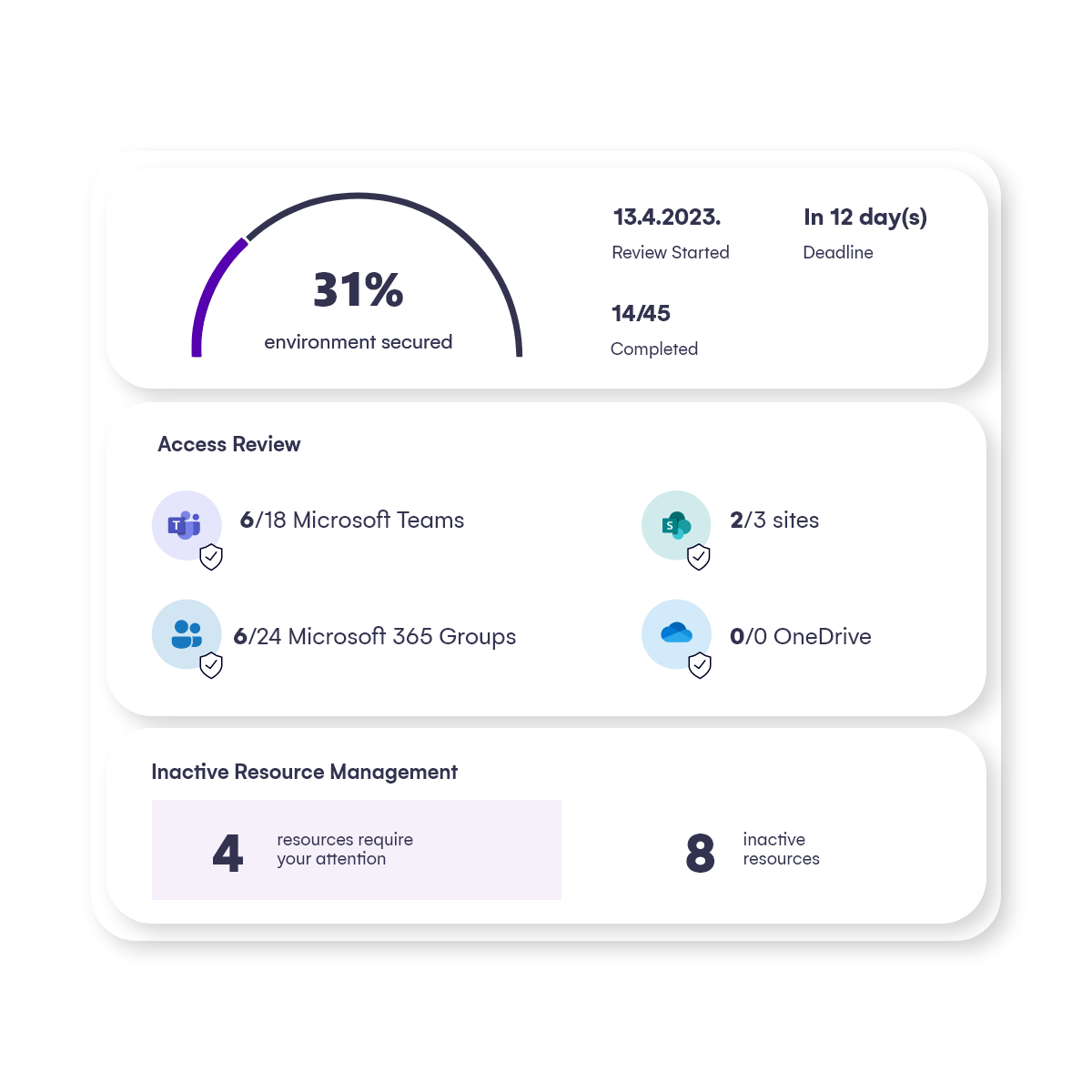
Full visibility and security across M365
Syskit Point is a scalable, no-code platform that increases your tenant’s compliance and security posture. It provides the visibility you need to mitigate risks and improves the efficiency of your processes.
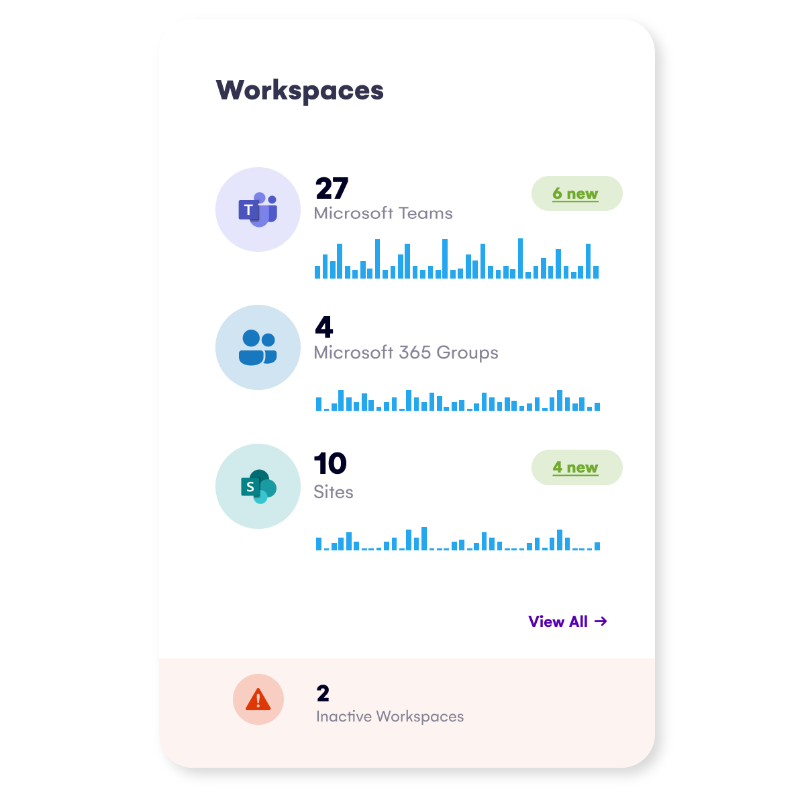
- A centralized inventory, with complete access control and information sharing awareness across Microsoft Teams, Groups, SharePoint Sites, OneDrives, and Power Platform helps you make the right decisions and manage your tenants efficiently.
- Whether you need detailed reports, real-time access management actions, activity auditing, or optimizing storage usage, Syskit Point has you covered.
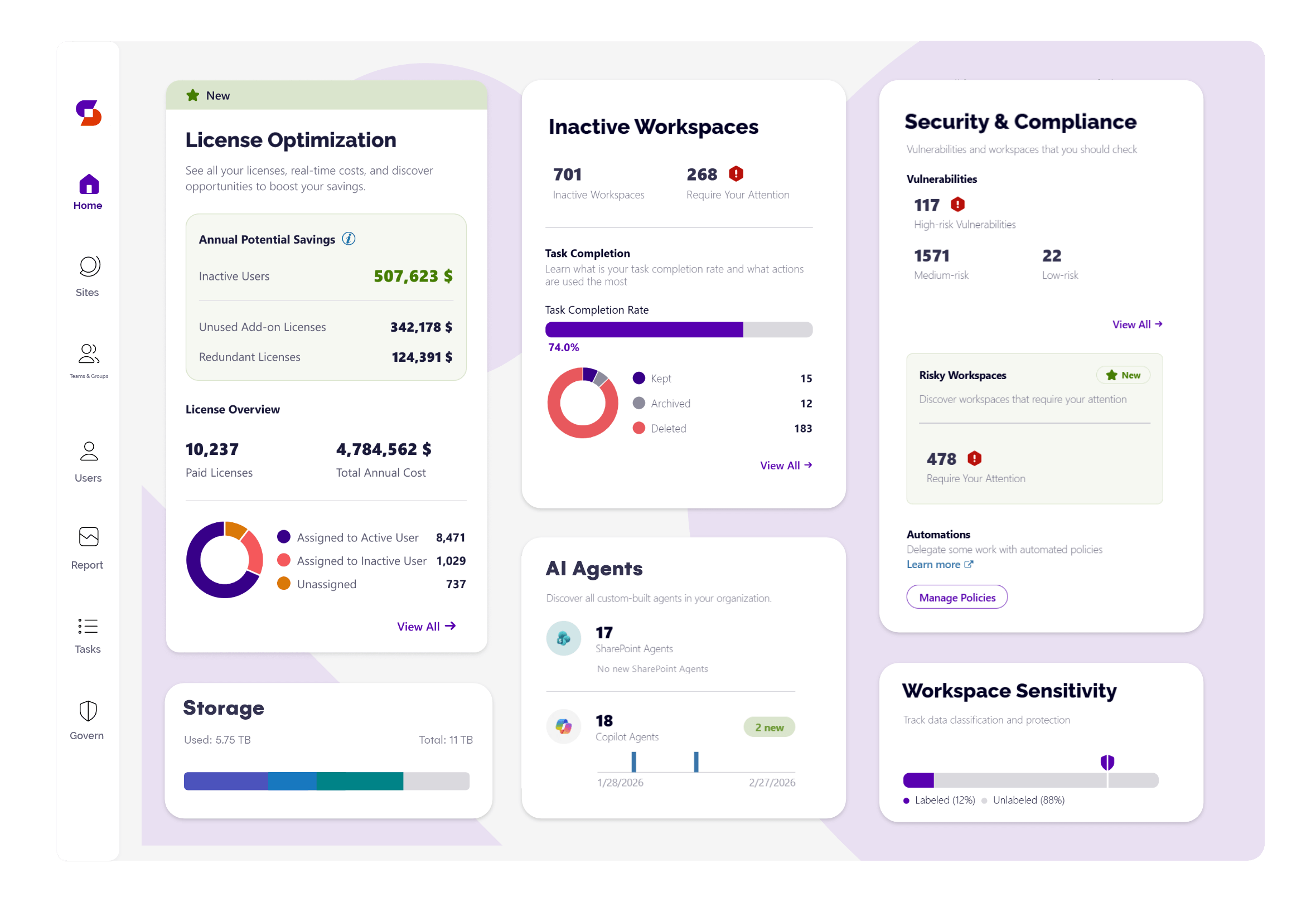
Straightforward M365 governance and automations
Syskit Point makes it easy to enforce governance policies and gain complete control over a workspace’s entire lifecycle: creation, lifetime maintenance, and disposal.
With it, you can manage sprawl, avoid oversharing and data leaks, and ensure Copilot’s results are appropriate, accurate, and compliant if you plan to roll it out.
- Combine rules and conditions and automatically apply policies to workspaces, regardless of how and when they were created.
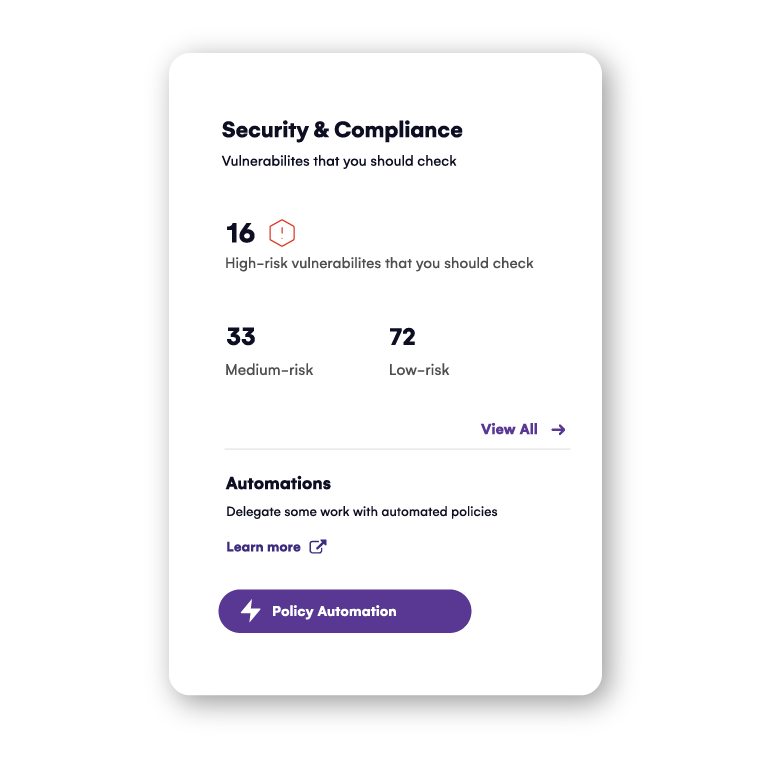
- The central dashboard shows the most critical vulnerabilities you need to address with immediate actions and automations.
- Set up automated tasks and access reviews for owners to regularly manage and clean up their workspaces and resources.
Enterprise level security
Your Microsoft 365 environment is our priority. This is why we undergo continuous audits and hold ourselves to the highest standards, such as:
- SOC2 Type 2
- ISO/IEC 27001