Microsoft 365 security guide
Table of contents
It’s little surprise that Microsoft 365 security is important since it is a top target for attackers. Its user base includes over 400 million seats, and over 320 million monthly active Teams users. In turn, this sees vast volumes of valuable and sensitive data being created, shared, and used on cloud-based platforms.
The number of endpoints and attack surfaces has increased exponentially – making it harder to detect attacks that affect different workloads in an enterprise. Let’s take an example of a phishing attempt taking place via email. It’s a simple attack where a recipient clicks a malicious URL in an email and, by doing so, unlocks corporate data stored in the cloud. Data theft occurs while further attacks and payloads proliferate throughout the network. These distributed scenarios mean IT heads are tasked with securing data and infrastructure like never before.
Microsoft 365 Security challenges
There are many types of sensitive data that need securing. Bank account numbers, classified business reports, Personally Identifiable Information (PII) – both personal and business-related. All are commonly stored inside Microsoft Teams, Office applications, Groups, OneDrive, or SharePoint.
Microsoft is aware of these challenges, highlighting that, “Many organizations use a patchwork of manual activity and disconnected systems.” Unfortunately, these gaps are where vulnerabilities can appear, and where attackers often focus on. After all, a Microsoft 365 security strategy for data is only as strong as its weakest link.
Faced with Microsoft 365 security threats, The World Economic Forum has identified cybercrime as one of the “key threats of the next decade”, placing it alongside weapons of mass destruction and climate change. Meanwhile, Accenture (pdf) has found a 31% increase in cyber security attacks between 2020 and 2021, while phishing attacks reportedly doubled in 2020.
It’s worth noting that there is some good news regarding these well-documented risks. Microsoft’s Digital Defense Report states, “Basic security hygiene still protects against 98% of attacks.”. At the same time, Gartner notes a growing movement toward security technology convergence, which “will lower total cost of ownership and improve operational efficiency in the long term, leading to better overall security.”
In such a fast-moving landscape, data in Microsoft 365 will always remain a high-value target. Fortunately, there are many methods for ensuring its security. But before we show them to you, let’s define what we mean by data security when it comes to Microsoft 365 in the first place.

Microsoft 365 security of data – the basics
Data security is a process of protecting digital data and information from theft, unwanted access, or unauthorized modifications. This protection occurs throughout the entire data life cycle, at every potential and actual endpoint. That means everything from hardware, storage devices, and software to admin controls and organizational policies and procedures.
Of course, preventing unwanted access to files from outside and inside your organization has always been a top priority in data security. Your business will already have defined Microsoft 365 security protocols for data protection.
However, the speed of changing industry trends is correlated with the speed of attackers searching for new ways to exploit the system. And the latest advances in AI and machine learning have enabled attacks to be launched at an unprecedented scale.
Rule-based and policy-based detection are no longer enough, particularly now that user identities are often spread across cloud infrastructure.
The human involvement element further complicates data security. Specifically, data breaches can often happen because of an employee error, not because of malicious intentions. As Bret Arsenault, Microsoft CISO and VP says, “sometimes intention is different than outcome”.
Organizations saw a relatively fast switch to cloud-based work in the new work-from-home era. But it can take time for people to get used to adopting security measures beyond the traditional HQ’s perimeter, adapting for home networks or mobile devices. For example, remembering to avoid saving sensitive data on desktops, not using Shadow IT, and following best practices when leaving the company.
The result is a mix of traditional and cloud environments and workplaces. Such complexity and diversity are why having a unified view of networks is so important. Let’s look at what’s involved in achieving this visibility for data security in Microsoft 365.

Key elements and processes of data protection in Microsoft 365
User identification via password is mandatory in Microsoft 365 and presents a foundation for data protection policy. The password itself also must meet certain requirements like defined length and types of characters used. All these requirements ensure high-security standards, but modern threats mean additional login security protocols are highly recommended.
Microsoft 365 encryption
All data stored on Microsoft 365 uses multiple encryption methods, protocols, and ciphers. These include BitLocker, Azure Storage Service Encryption, Distributed Key Manager (DKM), and Microsoft 365 service encryption. The solutions work end-to-end, encrypting data at rest and in transit and apply across multiple services including:
- Exchange Online
Mailbox content, emails, and attachments, calendar entries - SharePoint
Content stored on SharePoint sites and within files - Virtual networks
Cloud services, such as encryption traffic between Azure VMs and users
Identity protection
Microsoft analyzes trillions of signals daily, from sources as diverse as Azure Active Directory all the way to Xbox gaming sessions. These are fed to support and protect users, with logging and behavior reports combined with suspicious activity records. Multiple risk types are then detected, including anonymous or malware-linked IPs, leaked credentials, and brute force/password spray behaviors.
You can export reports for additional data processing or in-depth investigation with a Security Information and Event Management (SIEM) tool. Automatic remediation can also be triggered, such as password reset or blocking access until an Admin can review the activity.
Identity-driven policies
Conditional access for Azure uses if/then processes to maintain access controls. For example, if a user wants to view data, they must first complete a specific form of authentication. Policies can be targeted at group or user level for granular analysis at scale.
The conditions are based on various real-time signals. These can be configured regarding organization policy enforcements and may include application type, user location, and/or device used. This approach helps balance freedom and responsibility, giving workers flexibility while maintaining organizational security.
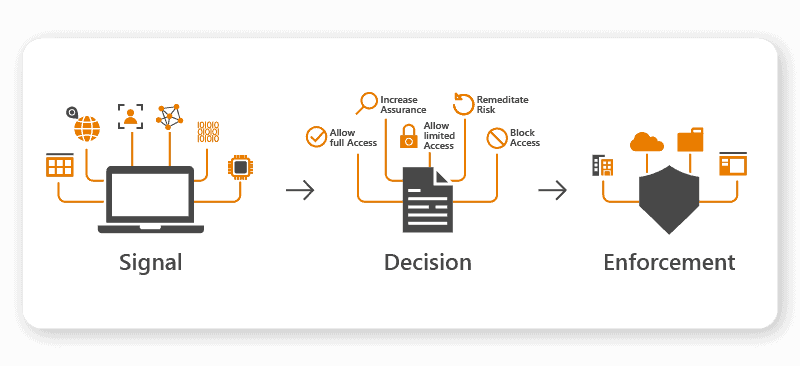
Data loss prevention
Through Microsoft Data Loss Prevention (DLP), you can implement policies that automatically identify, monitor, and protect sensitive data items. Sensitivity is detected using the deep content analysis methodology, which includes matching data to keywords, with machine learning algorithms deployed to manage large volumes.
DLP can generate different responses depending on the configuration if a user tries to do a prohibited action. These include showing a pop-up that warns the user, blocking a user from completing an attempted action, notifying the administrator. These can all be recorded in the Microsoft Audit Log, with alerts sent to the DLP alert management dashboard.

Microsoft 365 security threats
Regarding data in the Microsoft 365 environment, we can split those threats into two main categories: External threats and insider risks.
External threats in M365
External threats are all threats that can be sourced outside your Microsoft 365 environment. Attackers will try to find vulnerabilities and weak points to enter your infrastructure and access valuable and sensitive data.
One of the most common external threats is credential theft. Credentials theft is a process in which attackers steal login information and enter your system to access protected data.
Phishing emails, harmful third-party software, password leakage from other parties are examples of credential theft.
The work-from-home trend contributed to a dramatic rise in this threat vector, particularly through spoof websites. Scammers created over 700 fake Netflix and Disney+ signup pages alone to steal personal data from users.
Sites like these that request credit card information may also request crucial personal identification such as social security numbers or install malware to harvest end-user credentials.
Ransomware is also gaining popularity among attackers. In 2021, the FBI recorded a 62% year-on-year increase in ransomware complaints. From an organizational view, ransomware goes way beyond affecting individual users – entire operations are at risk. Either from actual infection or having to be shut down as a precautionary measure or as part of a disaster recovery procedure.
There’s also the risk of the double extortion ransomware model where threat actors ask for two ransoms:
They demand you pay them a ransom to restore all your locked files.
Then they ask you to pay another ransom to stop them from publishing the stolen files online.
Even if the organization pays, there’s no guarantee the attackers will return access to files. A Sophos report found only 4% of companies that paid got all their data back, with 61% of data restored on average. And if that doesn’t sound bad enough, research also indicates that 80% of victims who paid ransoms in ransomware attacks get attacked again within 30 days.
Insider threats in M365
Insider risks are continuous threats within your system from existing users within the organization. Specifically, they are the users who knowingly or unknowingly endanger your system’s data security. There are complexities in managing this risk because of the need to factor in workers’ privacy and human rights.
You can minimize insider risks with correct user permissions configuration and security settings inside Microsoft 365 and SharePoint. These permissions allow you to control specific users or groups’ access to selected data and define what they can do with it.
Machine learning isn’t used only by malicious individuals. It’s also possible to harness machine learning for managing insider risk – without requiring a data science team or resources. That’s possible due to Microsoft’s policy templates (found in Purview Insider Risk Management, available with certain versions of Microsoft 365). The templates enable users to identify patterns and risks they may miss using manual methods. For example, helping identify when a departing employee is merely downloading work for their portfolio, compared to stealing confidential data.
The templates cover three areas: Departing Employee Data Theft, Data Leaks, and Offensive Language in Email.

How to improve your Microsoft 365 security
Stakeholder buy-in
There’s no point investing in solutions if there’s no internal business drive for cultural and behavioral change. That comes from the very top. For large and distributed organizations, it’s essential to identify a group of stakeholders operating at C-level.
These senior executives should be from across the business. For example, you need buy-in from HR, Legal, and Compliance alongside the Information Technology departments – leaders who can influence and guide the entire shift. Once a steering group is established, you can consider adopting some of the methods and technologies outlined below.
Sensitive information types (SITs)
These pattern-based classifiers detect sensitive information within Microsoft 365. For example, names, addresses, and medical conditions. You can then define specific actions to support Microsoft 365 security, such as forcing email encryption when people communicate inside and outside your networks.
You can use SITS to support your compliance with regulations such as GDPR, CCPA, and HIPAA. Although, this should always be accompanied by guidance from your relevant legal teams or qualified third-party advisors.
Multi-factor (MFA) or two-factor (2FA) authentication
Multi-factor authentication acts as an additional layer of security. Mobile app authenticators can be used with MFA to confirm Microsoft 365 user identities, letting them log into the system only after using the correct password. MFA can also be applied when a user uses a new or unknown device.
All Microsoft 365 or Office 365 plans that include Microsoft Teams support MFA. You can start by rolling this out to administrator-level roles and then to all users. For more advanced and granular login security, consider using Conditional Access. You can customize login permissions and denials, such as when a user tries to log in with legacy protocols.
Insider risk management
Microsoft Purview Insider Risk Management is a solution available with Microsoft 365 E5 Compliance.
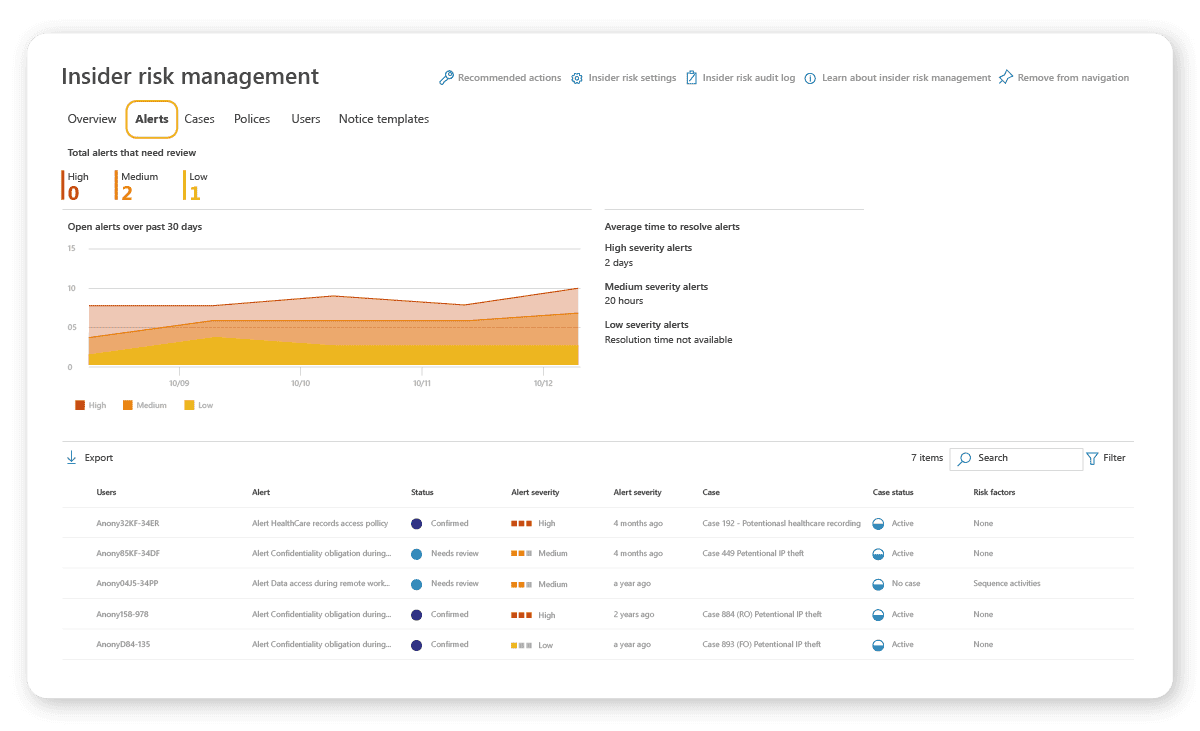
The solution means you can quickly identify, triage, and tackle risk indicators and other potentially malicious activities and threat actors. Among its many features, you can:
- Define risks to identify & detect
You can customize this Microsoft 365 security aspect to match your exact requirements and use cases.
- Turn on auditing
Your organization’s user and admin activities are recorded in the Microsoft 365 audit log. Any potential risks are flagged for investigation.
- Conduct analytics scanning
You can scan for potential insider risks – before you have to configure insider risk policies. This helps you scope out what’s required before committing any resources.
Adopting a Zero Trust approach
Modern Zero Trust policies are becoming the de facto first line of cyber defense for many organizations.
Forrester defines the strategy as “an information security model that denies access to applications and data by default.
Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices.”
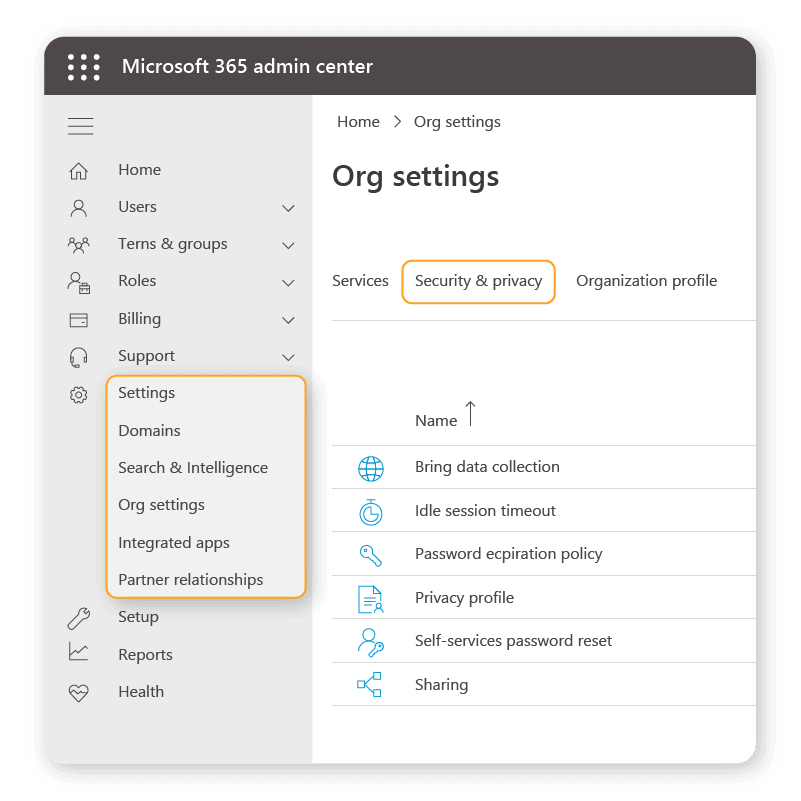
As part of this approach, administrator accounts should consider adopting a “least privilege” principle. The principle aligns with the Zero Trust strategy, where users have the absolute minimum level of access to do their job. Part of this should involve reviewing your organization’s default sharing settings for SharePoint and OneDrive. Here’s a quick example of how to make a quick improvement:
- Go to the Microsoft 365 admin center
- Click Org settings > Security & privacy > Sharing
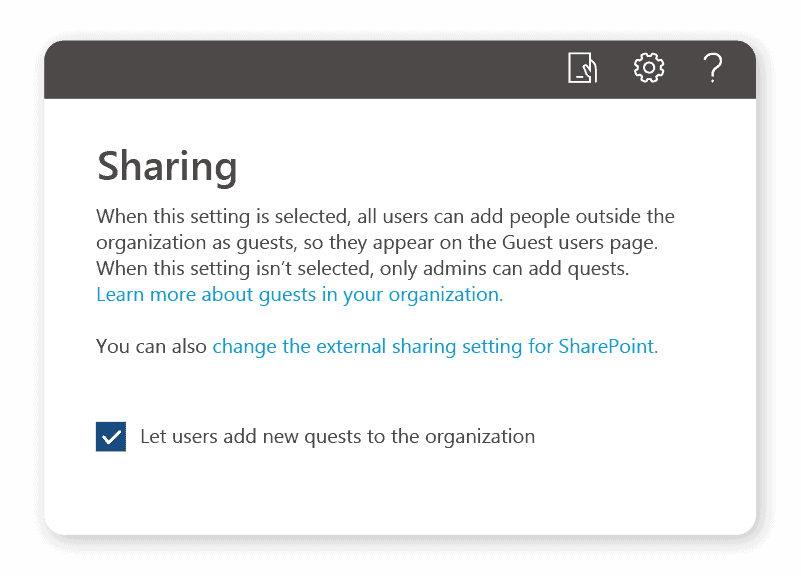
3. Untick the “Let users add new guests to the organization” box:
Microsoft 365 Defender
Microsoft 365 Defender coordinates, integrates, and unifies data security for protection against sophisticated threats. It performs by bringing in signals from different workloads across Microsoft 365, evaluating current security postures for detection, prevention, investigation, and response.
With the Microsoft 365 Defender, security teams can understand the potential impact across endpoints, identities, emails, and applications.
Microsoft Defender also offers simulation training where admins can run simulated phishing and social engineering attacks. With threat vectors evolving and attack surfaces expanding, this form of training has never been more essential.
Microsoft 365 permissions & policies
Make sure to adjust security and permissions settings in SharePoint. Rather than employees sharing data via email, you can enforce that they use SharePoint links instead. This way, you get the advantage of knowing who’s clicking the links. The kicker is that you can set expiry dates, so the data only remains accessible for limited periods.
Retention policies can also help you manage your organization’s information and data security within Teams. These can also be used to support governance when retaining data. For example, the HIPAA requires retaining certain data types for a minimum of six years.
Azure frameworks
Organizations using Azure are encouraged to apply the Microsoft Azure Well-Architected Framework, which consists of five pillars of architectural excellence. Security is among the five, with data sovereignty and encryption as the key elements. Microsoft’s recommendations include:
Data location
Making sure your data is in the correct geopolitical zone when using Azure data services. This ensures you meet data residency and compliance requirements where you operate.
Data classification frameworks
Organizations should ensure data is classified according to risk. This would typically involve 3–5 sensitivity labels, ranging from publicly available to highly confidential. The more regulated your industry, the more labels you tend to need.
The labels protect data by enforcing encryption or content marking to restrict actions to certain authorized users. The framework is usually applied across the business to minimize potential changes or edits to data.
Of course, building more provisioning workflows helps you understand what’s happening in your environment too.
End results of data security
All of this probably seems like a lot of elements to factor in. And yes, some will require investment – in terms of time as well as budget. However, there are many direct and indirect pay-offs when ensuring data security in Microsoft 365.
One of the benefits is that you will future-proof your business for what’s coming in terms of regulation. GDPR is EU-based, but there are signs the rest of the world is catching up and enacting their versions. For example, in the US, there’s the California Consumer Privacy Act. Japan has the Act on the Protection of Personal Information (APPI). Qatar, Bahrain, and Israel have strict data protection and privacy regulations.
There’s also the longer-term impact to consider. After all, the immediate costs of paying ransoms are fairly easy to quantify. The less tangible losses could have devastating long-term impacts like loss of customers, business partners, and regulators’ trust.
In conclusion, you should not take Microsoft 365 security casually, and we hope the advice listed above helps you stay safe.


