Microsoft Defender ATP – sweeps security threats away
Table of contents
Enterprise organizations need enterprise-level anti-malware defenses, as sophisticated and advanced threats target businesses with deep pockets and the ability to pay large ransoms for valuable data and files. Hacking is a business for many threat actors, and many state sponsored attacks target critical infrastructure and government entities.
The most effective and vulnerable targets are your users who are unable to detect threats, but you can reduce risks by using integrated Microsoft Defender ATP on endpoint devices and across your network.
Microsoft Defender is generally used on Windows servers and devices, and it’s been ported to macOS, Linux, Android, and iOS.
Defender ATP is an enterprise anti-malware solution that gives organizations full visibility of all devices connected to the environment, and administrators can leverage analytics and advanced capabilities to protect against threats that target endpoints.
How advanced threats target and compromise your enterprise
As better cybersecurity defenses are deployed in the enterprise, threats also evolve to bypass these defenses. It’s not uncommon for enterprise organizations to have advanced monitoring and threat defenses at the network perimeter, but an even bigger risk to the environment is users. For this reason, attackers have changed their focus from servers and network equipment to end-users and their devices.
Two advanced threats are commonly used to take advantage of users: phishing and ransomware. Both attacks have proven to be effective against enterprise defenses and threat monitoring, and they’ve caused considerable downtime and cost organizations millions in reputation damage and data corruption. Both attacks take advantage of human error, which is one of the top risks to any organization and continue to be a major concern globally.
Ransomware: Costly hijacking of your data
Ransomware often starts with phishing. With the global pandemic forcing users to work from home, phishing attacks spiked dramatically in 2020 and continues to increase in 2021. From August 2020 to January 2021, phishing attacks quadrupled and high-privilege are the main target. Targeting specific high-privileged users could give an attacker access to critical files stored across the network, and this means ransomware also has access to these files should the user execute it. It’s not always a high-privileged user, as some attacks are successful after a standard user falls victim to phishing.
A threat actor’s goal in a ransomware attack is to trick users into downloading and executing malware. The malware could be an executable attachment (e.g., exe file) or a seemingly innocuous Microsoft document with a macro that downloads the ransomware executable file. Links to attacker-controlled websites convincing users to download ransomware are also an issue, and in some cases credential theft is an added goal.
Monetary impact from a ransomware attack can be seen in any one of the recent cyber incidents involving the malware. For example, the Broward County Public Schools district was a target of the Conti ransomware in March 2021. The attackers exfiltrated 26,000 files and demanded $40 million for the files and private keys to decrypt the school district’s data. The school tried to negotiate with attackers to reduce the ransom to $500,000 but was met with release of sensitive data to the public.
Ransomware is a unique and effective threat that cannot be remediated with standard antivirus removal tools. The encryption used in ransomware is cryptographically secure, so the only way to recover files and data is with backups. But, ransomware also searches the network for backup files and encrypts those as well, leaving the organization crippled should it successfully find them. It blocks productivity and creates revenue-impacting downtime stopping employees from doing their job. If the organization refuses to pay the ransom, the attacker might threaten to blackmail the business by publicly exposing sensitive data or intellectual property.
Phishing: A common attack vector with high-damage potential
It only takes one user to fall victim to a phishing attack, and the ransomware can scan your network and encrypt files with an irreversible payload. Phishing is one of the most common vectors in cybersecurity attacks. It leads to privilege abuse, data theft, ransomware and many other attacks. In Verizon’s Data Breach Investigation Report, research showed that phishing was the vector used in 36% of attacks. Threat actors using malicious email use a variety of methods to convince users to run malware or divulge their network credentials.
Even more concerning is spear phishing, which targets specific users within an organization, usually ones with high-privilege accounts. Combined with ransomware, spear phishing can cripple an organization. In severe scenarios where the organization does not have good backups, ransomware forces companies to pay a ransom that could be hundreds of thousands of dollars.
Spear phishing is used in other malware attacks as well. It can be used to insert trojans and rootkit software on a targeted user device so that the attacker has remote control of the device. With remote control of the device, the attacker then can access network files and resources with the authenticated user account.
Defender endpoint anti-malware reduces risk
While phishing and ransomware are popular threats, they aren’t the only advanced methods attackers use to compromise a system. Verizon’s Data Breach Investigations Report lists various threat actions targeting the enterprise including denial-of-service (DoS), credential theft, misconfigurations, privilege abuse, malware injection, social engineering, and exploits on vulnerable software.
An enterprise needs more than basic antivirus protection to defend against the numerous threats that target end-user devices. Today’s modernized environment also allows users to bring their own devices to stay productive, and these devices add even more risk. Cloud applications such as Office 365 are also common where productivity and email are centralized and more convenient for IT staff, but it can be used as a vector in attacks.
McAfee Endpoint Security, Kaspersky Endpoint Security, Symantec Endpoint Protection, and Trend Micro Apex are all viable options for enterprise cybersecurity. They all have anti-malware capabilities, but Microsoft Defender has several more benefits and features integrated directly into Windows that can be leveraged without deploying additional third-party software. For some applications such as McAfee and Symantec, users complain of performance degradation and productivity interruptions. Enterprise-level security needs full support and protection from threats, but it should not interfere with user productivity and device usability.
Threat authors continuously create applications that bypass security, but Microsoft Defender is embedded into the Windows operating system so that it can properly block attacks without frustrating users with false positives and hijacked processes that interfere with productivity. Instead of using a simple antivirus program to block attacks, Microsoft Defender is a full cyber-threat defense application that includes many other features than other standard enterprise-level endpoint cybersecurity.
What Microsoft Defender ATP can do
Using the example of a ransomware attack, the primary vector is email with an attachment or link to a malicious website hosting malware. In a successful attack, users run malware on devices either directly or indirectly. Microsoft Defender detects malware before it accesses device memory and blocks it from execution. This is common in anti-malware protection, but Defender ATP does much more for an enterprise that gives more visibility to administrators responsible for monitoring all devices with access to the network environment.
A few other Defender ATP enterprise features include:
Discover misconfigurations and vulnerabilities
Administrators need a way to oversee endpoints and identify threats. Defender ATP has a central dashboard where administrators can view threat scores across the network for all devices, appliances, accounts and other controls.
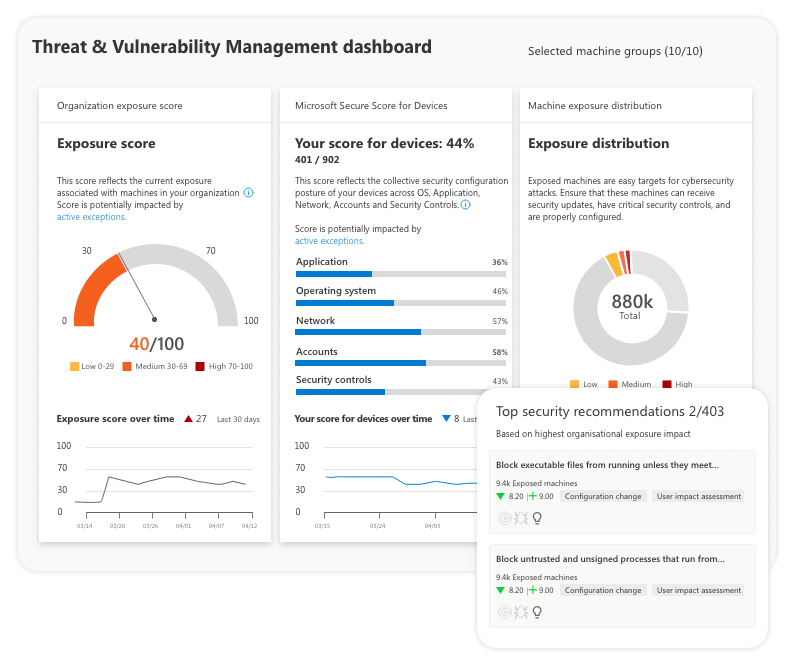
(image: Microsoft Docs)
Machine learning and big data analytics
Machine learning (ML) is the next generation in cybersecurity so that administrators can make decisions and get analytics to make predictions from advanced algorithms and heuristic information. Defender ATP uses big data and heuristics to discover threat patterns that could detect suspicious behavior and identify ongoing attacks.
Attack surface reduction and rules
A common best practice in cybersecurity is reducing your attack surface. An attack surface is a virtual area where all endpoints and network infrastructure increase the risk of threats. The more applications and endpoints added to your environment, the larger the attack surface grows. You can reduce your attack surface by limiting access to untrusted devices (e.g., a user’s personal laptop) and create rules that block devices that don’t meet security recommendations.
Simulate attack scenarios and run simulations
How do you know if your devices are defended if you can’t emulate a real-world scenario? The simulation and evaluation lab lets administrators penetration test the network for vulnerabilities as if the network experienced an ongoing real-world attack. Find vulnerabilities and get suggestions using the simulation lab.
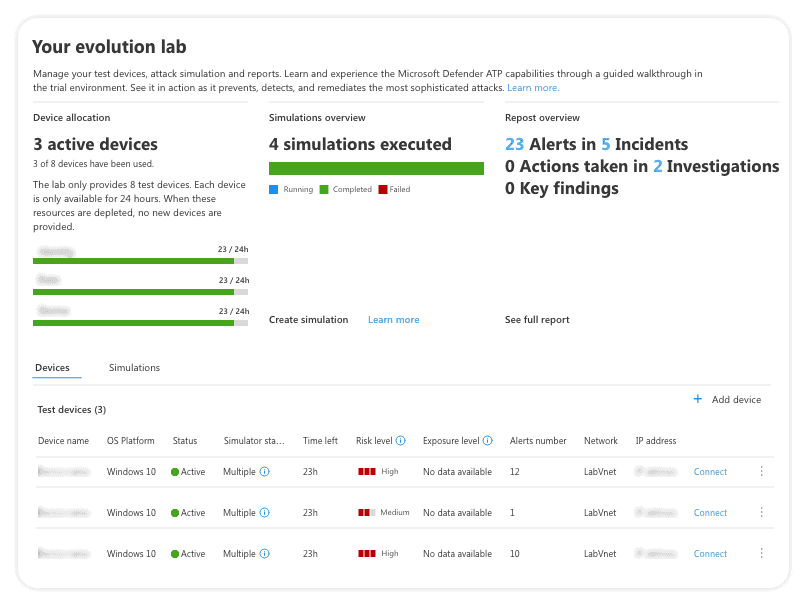
(image: Defender simulation results)
Endpoint detection and response features
In a large enterprise, you could have thousands of devices connecting to the network. These devices must be accounted for and detected so that administrators can run analytics and ensure that they meet security requirements. Defender ATP continuously monitors the network for new devices, collects behavioral data, and performs forensics to determine if the device poses any threat to the environment.
Automated investigation and remediation
Both Microsoft Defender and Azure have automated investigation and remediation (AIR) capabilities. This tool finds vulnerabilities and provides additional information about any devices that should be further updated or configured. Administrators can further review, mitigate, and remediate the issue before it causes more damage.
Exposure scores to help calculate exploit potential
The dashboard includes exposure scores so that administrators unfamiliar with risk and vulnerabilities can evaluate their exploit potential being cybersecurity experts. It’s a convenient way for administrators to know when action must be taken to better secure the network. The exposure score provides administrators with a convenient way to gauge network security.
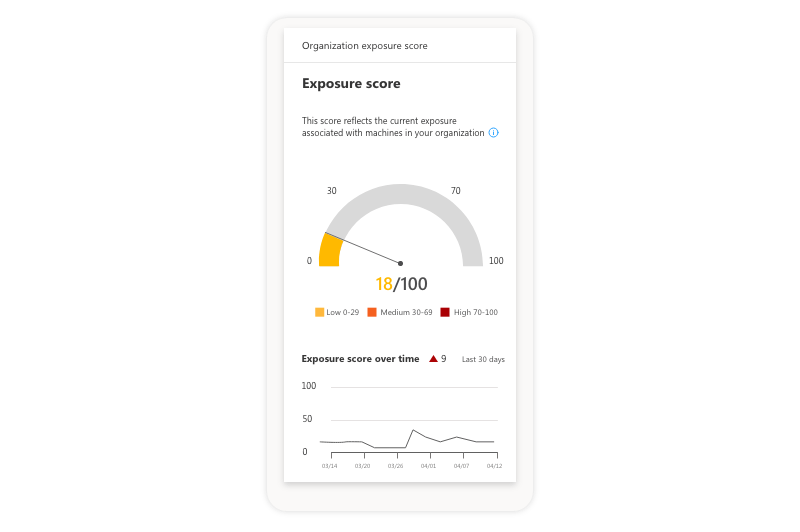
(image: Exposure score)
How to configure cybersecurity for your organization – Download security guide
Installing Microsoft Defender ATP is the first step in securing your network. The next step is to properly configure it. Misconfigurations in cybersecurity tools and appliances are also an issue for organizations, especially when administrators are unfamiliar with the ways hackers compromise devices. You can learn more about Defender and configuring your Office 365, Azure AD, and SharePoint environments in our security guide eBook.
Microsoft 365 security management with Syskit Point
If you’re interested in improving your Microsoft 365 security in a broader sense, let us introduce you to our security tool – Syskit Point!
For Example, it can alert you via email whenever a sensitive file is accessed, or a guest user edits a file. Moreover, you can audit user activities, suspicious logins, as well as report on access and changes in permissions and settings. With these features, you can proactively secure your tenant and sleep tight at night.


