Microsoft Teams security hacks
Table of contents
At the beginning of 2020, many people started to work from home amid the COVID-19 pandemic. It was apparent there was going to be an enormous usage growth of remote-work tools. While the world fought the virus, System administrators had to make sure their IT infrastructure was safe from other types of viruses – the virtual ones.
As many companies increasingly began to use communication and collaboration tools, many security analysts started researching the security aspects of these tools. Some very popular apps were found to have inadequate data privacy and security measures, so companies began to do their research to see how to keep their data private and secure while using collaboration apps.
Microsoft Teams overview
Although relatively new, Microsoft Teams is already a mature application that spans existing Microsoft technologies, such as SharePoint Online and Exchange Online, allowing end-users to utilize many features from a single application.
Microsoft claims it incorporates industry-standard security technologies in the Teams architecture, along with encryption mechanisms for secure communication. Nevertheless, I would like to point out a few recommendations on what to look out for and how to strengthen the security of your Teams’ environment.
Control guest and anonymous users in Teams
Guest users are people outside your organization that you invite by sending an invitation to their business or consumer email address. Once the invitation is accepted, credentials are stored in your Azure Active Directory. Guest users can be given nearly all the Teams permissions as a native team member, so they can chat, call, meet, and collaborate on files using Office 365 apps.
While allowing guest access might be convenient in many cases, some companies have strict policies on accessing company data from the outside, so they may want to disable guest access in Teams. This is actually a tenant-wide setting that is disabled by default.
On the other hand, if you are confident to allow guest access, Teams administrator can easily enable the “Allow guest access in Microsoft Teams” option from the Teams admin center.
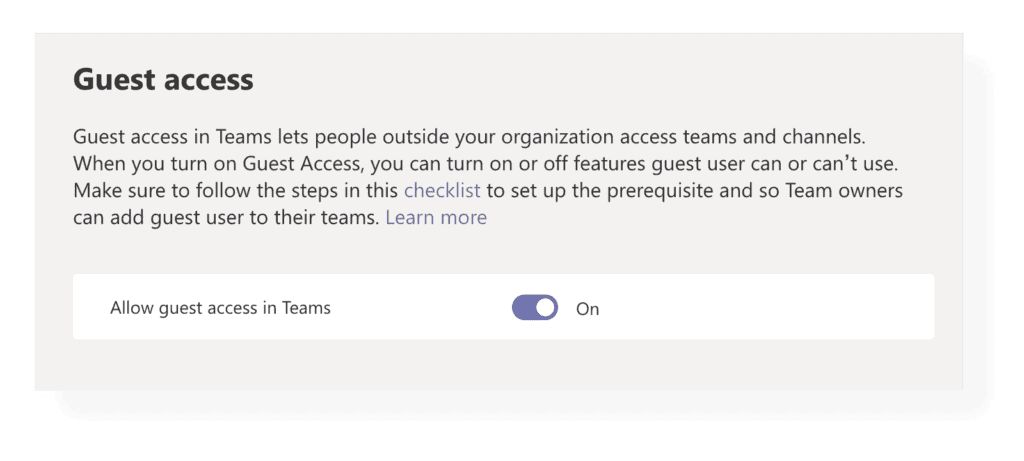
Note that for guest access to be fully operational, you should also configure security settings on several levels. This checklist provided by Microsoft might come in handy to turn on and manage guest access in Teams and all the other necessary levels.
Anonymous users, on the other hand, don’t have credentials stored in your Azure Active Directory, so you have no insight into who they are. If you don’t want anonymous people to be able to join a Teams meeting, you can disable the “Anonymous users can join a meeting” option from the Teams Admin center.
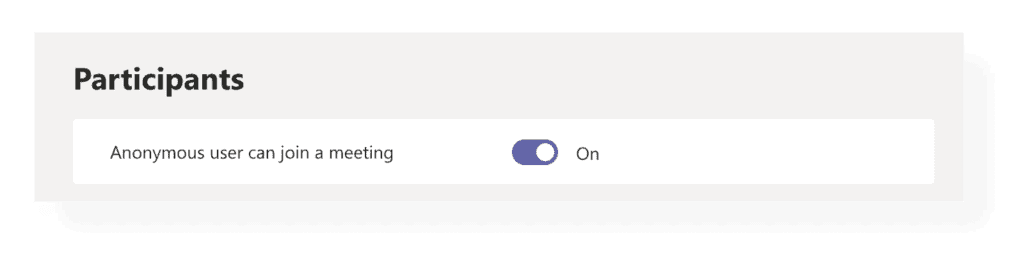
Change participant settings in Teams meetings
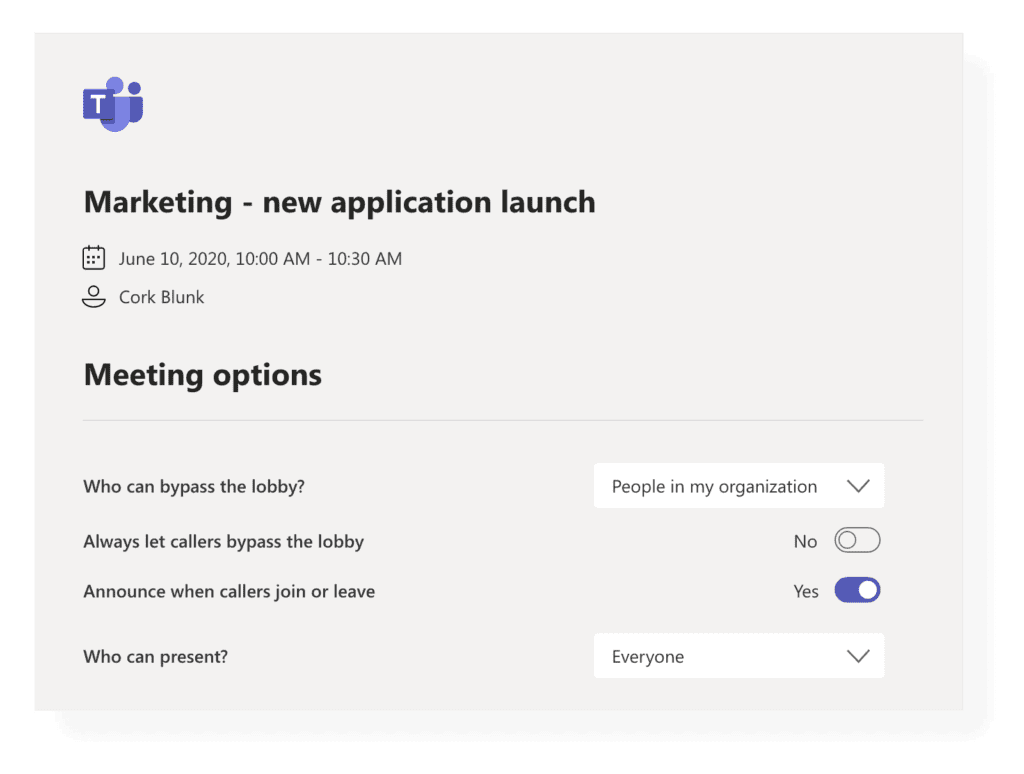
Each Teams meeting has several meeting options. The meeting organizer can choose who can bypass the lobby and who should wait for someone to let them in. You can also set Callers to automatically bypass the lobby, and you can get notified when they join or leave a meeting. As for presenting, you can individually select who in the meeting can present.
Enforce multi-factor authentication
Multi-factor authentication (MFA) drastically improves the security of user logins to Office 365. When enabled, a user must enter their username and password on the login page. However, they must also verify their identity with another authentication factor by receiving a phone call, text message, or an app notification on their smartphone. You must be a global admin to set up MFA.
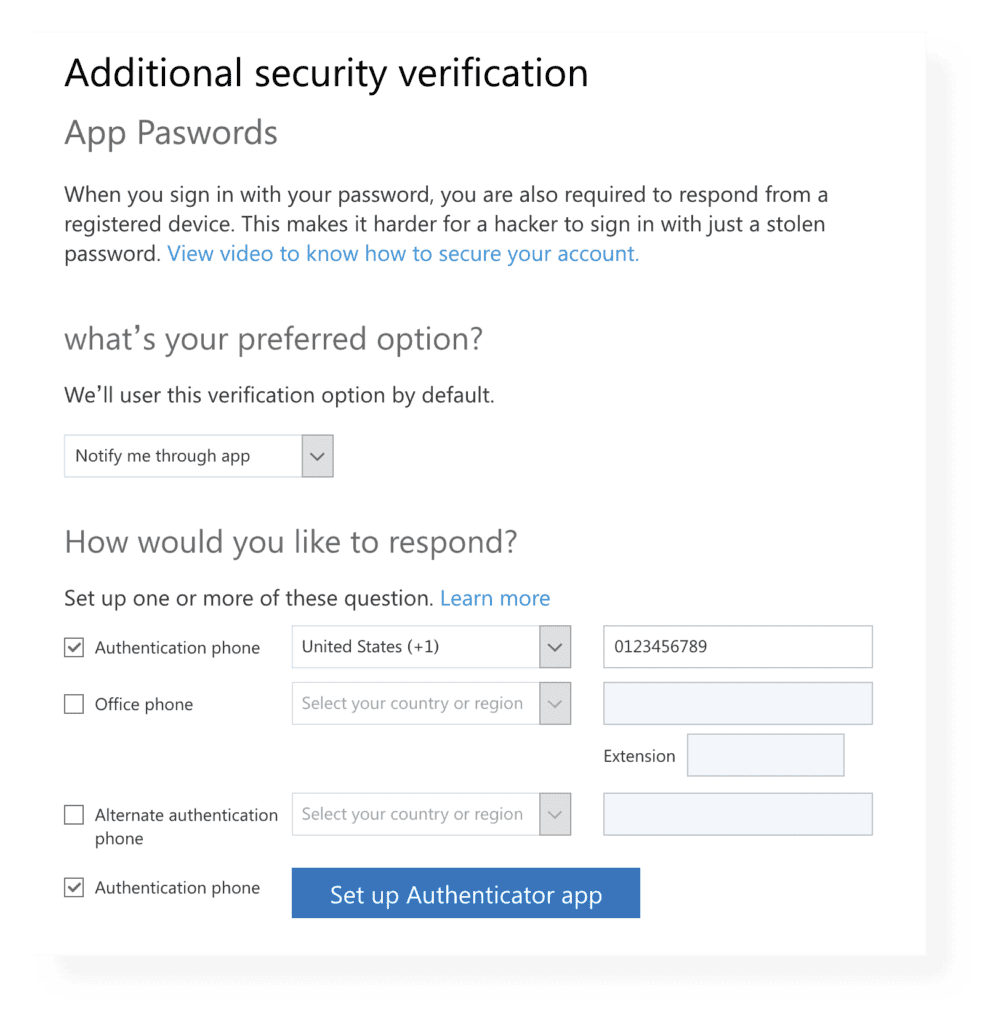
As a best practice, all privileged user accounts in your tenant should have MFA enabled, but enabling it for all other users is more than welcome. You can configure MFA on the guest users too. If needed, you can utilize the security group membership in Azure AD for a subset of users and apply the MFA specifically to this group using Conditional Access Policies.
Advanced threat protection
The Advanced Threat Protection (ATP) subscription comprises of many useful features that can be used to protect your organization against malicious threats better. By default, ATP scans for malicious files in SharePoint Online, OneDrive for Business and Teams, and automatically locks them down. You can also utilize ATP Safe Links and ATP Safe Attachments for even stronger protection.
ATP Safe Links helps you identify malicious URLs, while ATP Safe Attachments checks for malicious email attachments. These safety features span throughout Teams activities, such as sharing the files or URL links in your chats or channels.
Other security options in Azure AD
If you’ve ever used Teams before, you probably know that there are several ways to access calls or chats, such as from a desktop client app, mobile app, web browser, or IP phone. You can even access Teams from systems such as Mac OS, iOS, and Android. By default, there are no restrictions on where you can access Teams.
All these options that Microsoft Teams provides require proper security management of the data circulating through Teams. As with many other Microsoft cloud apps, such as Exchange Online, SharePoint Online and OneDrive for Business, you can take advantage of Azure AD Conditional Access, to set conditions that must be met for users to use Teams.
Some of the Teams usage conditions include security management by device, platform, and location, defining sign-in risk acceptance. If you have a Microsoft Intune license, you can, for example, restrict the use of Teams-certified IP phones by the minimum Android version. If you’re not enrolled in Intune, you can manage the Teams app on various devices from the Mobile Application Management (MAM) feature.
Microsoft Teams also supports standard Office 365 or Microsoft 365 compliance features, such as the following:
- Data Loss Prevention (DLP) - protect sensitive information in documents and other forms of data. Recently, DLP can be applied to Teams chats and channel messages, including private channel messages.
- Information Barriers - restrict communication between groups or even specific people within your organization. When in place, information barriers prevent users from finding, selecting, chatting, or calling other users in Teams, restricted by the policy. These policies also apply to guest users.
- Communication compliance - Search teams’ communications for offensive language, sensitive data, and information related to internal and regulatory standards.
- Retention policies – manage chat, channel, and files retention instead of keeping them indefinitely.
- eDiscovery and Legal Hold – search, analyze and preserve Teams chats, files, meetings, and call summaries for legal purposes.
- Auditing and Reporting – search through event logs for specific activities of your users and admins and set alerts on specific events.
There are many other options for securing data and establishing effective information management in Teams, so check the official Microsoft documentation and regularly follow news and feature updates.
In the end, I would like to point out that Microsoft has implemented the auto-update feature for the Teams app on Windows and Linux, so you don’t have to worry about updating each client. Conversely, the mobile Teams apps need to be updated manually, so make sure the Teams apps on your users’ mobile devices are updated regularly.
Conclusion
In this blog post, I have outlined many security features that you can use to protect your corporate and sensitive data circulating through Microsoft Teams. Many of these features require specific Office 365 or Microsoft 365 licenses, so make sure you have the appropriate permission to implement the features you want.
You should, however, know that no system configuration by itself can guarantee complete security. You will always need to turn on some of the security enforcements we mentioned in the post to govern the security risks better. Lastly, you will need to train users on how to use those security tools properly to minimize potential security issues.
I hope you will find this security overview useful and handy for protecting your Microsoft Teams environment.


