Office 365 security best practices – How to stay safe in 2025
Table of contents
IT professionals have been encouraging companies to move to the cloud for a decade. There were many reasons why companies delayed the implementation of cloud technologies, but one of the top concerns was about the security of data in the cloud. This is why we’ll examine the Office 365 security best practices and how you can keep your environment secure.
As you may know, IT professionals were pointing out that the cloud proved beneficial for the high availability of companies’ systems and data they hold, as well as overall business continuity in case of a catastrophic event.
The Covid-19 pandemic showed that the businesses that invested in cloud and collaboration technologies had a considerable advantage of enabling their employees to work from home during the pandemic and after.
1. Microsoft Secure Score
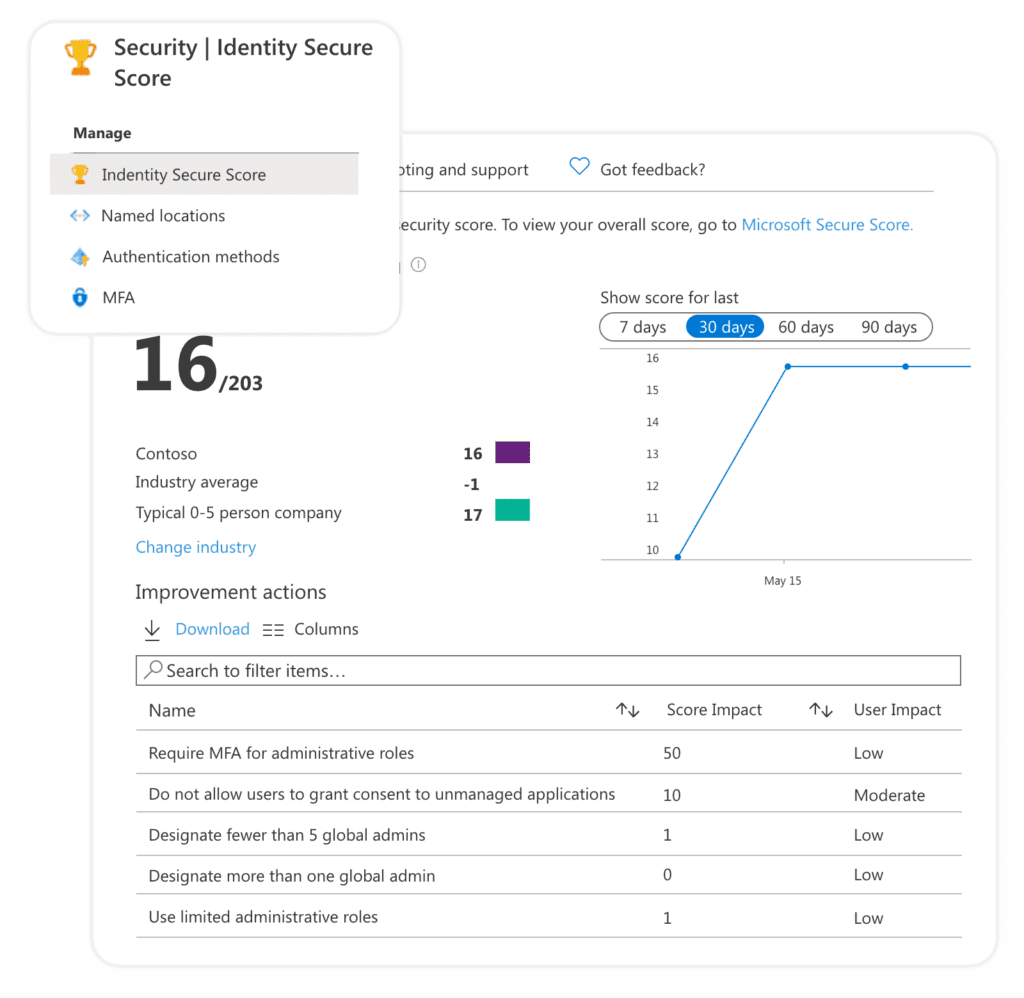
There are two flavors of security reporting in the Microsoft 365 platform. One is part of Office 365 security, and it is called the Microsoft Secure Score, and the other is part of Azure AD, and it is called the Identity Secure Score.
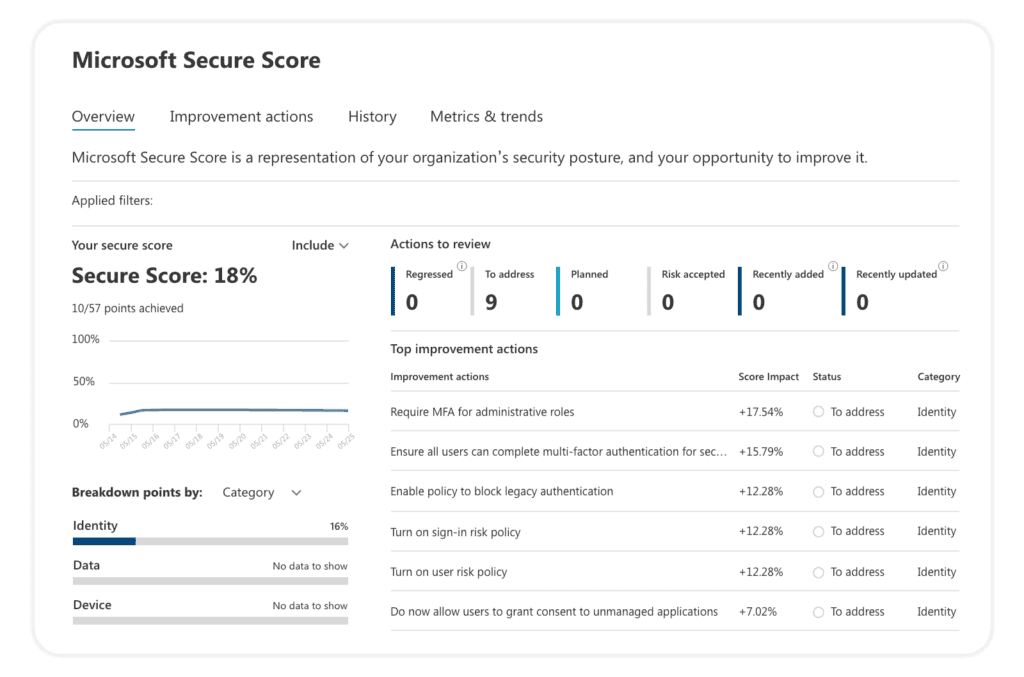
The Identity Secure Score is a new functionality designed to help customers assess if their security policies align with Microsoft’s recommended best practices. Think of it as a subset of the Security Score as it is part of the Azure Active Directory Admin Center. It is recommended you review these results periodically to improve your overall standing.
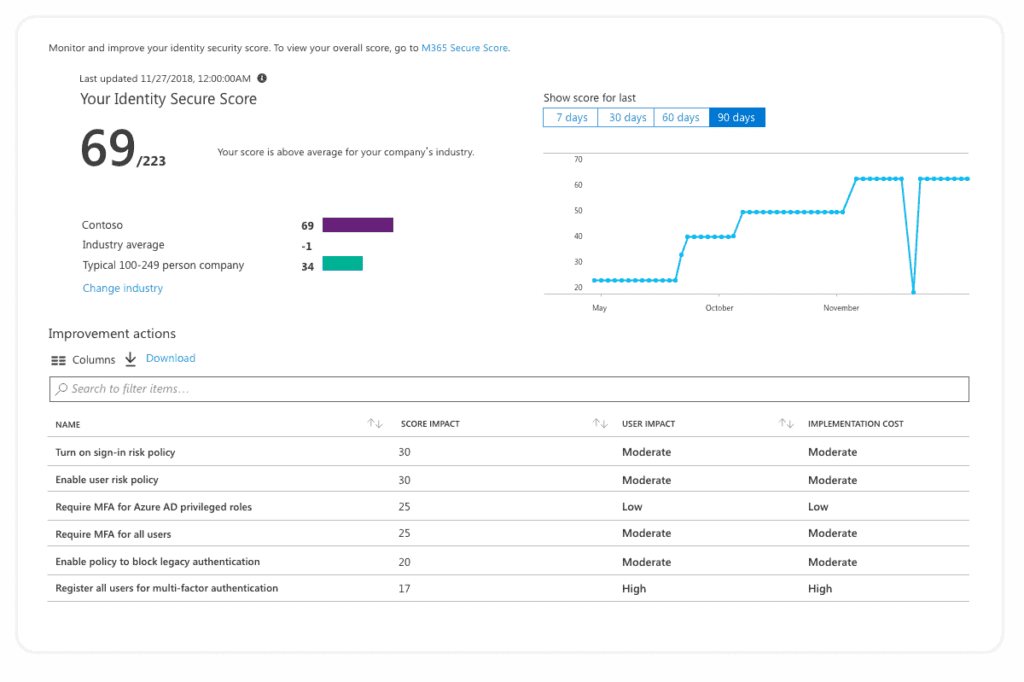
Both tools scan your environment and alert you of tenant configuration improvements you can do to follow the latest security best practices. These tools allow you to learn more about potential threats, how to mitigate them, and which features are there to help you. The tools continuously evolve based on Microsoft research and live system monitoring.
2. Office 365 security Audit Logs
Office 365 audit logs help you keep an eye on a continuous stream of events, operations, and user actions in your tenant. I sincerely advise you to enable auditing, as you never know when some critical situation might require it. To ensure you have enabled auditing, navigate to the Audit Log Search.
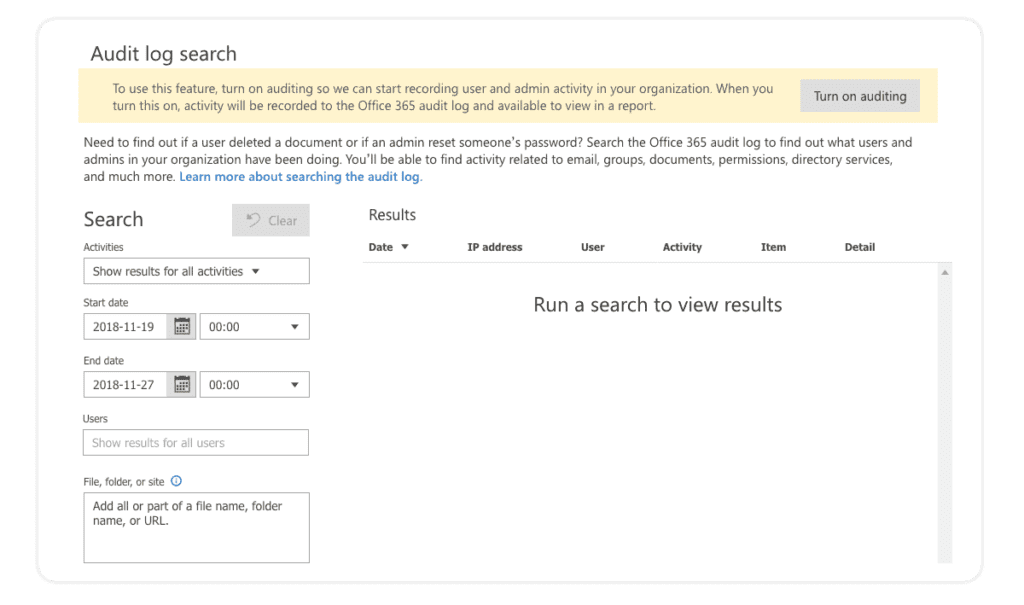
The audit log provides a comprehensive view of activities in various workloads like Exchange, SharePoint, Microsoft Teams, Groups, Azure AD, and DLP. The built-in search engine helps us find what we are looking for. More advanced users can use the Out-Of-The-Box PowerShell commands to query the log or query data from the APIs directly. If you need help getting around Office 365 audit logs, check out the Audit logs in Office 365 navigation guide, written by our Senior Software Developer Tomislav Kunaj.
One downside of the built-in approach is that retention of the log is rather short, only 90 days for Office 365 E3 licenses and 365 for E5 (in preview still). One way to extend it would be to use the API and store data in your storage or rely on one of the readily available Office 365 governance tools like Syskit Point. Syskit Point collects the most important Office 365 audit logs and displays every permission change, content update, or configuration change in a simple and manageable way. You can also adjust how long you want to keep your audit logs with Point’s custom retention policy.
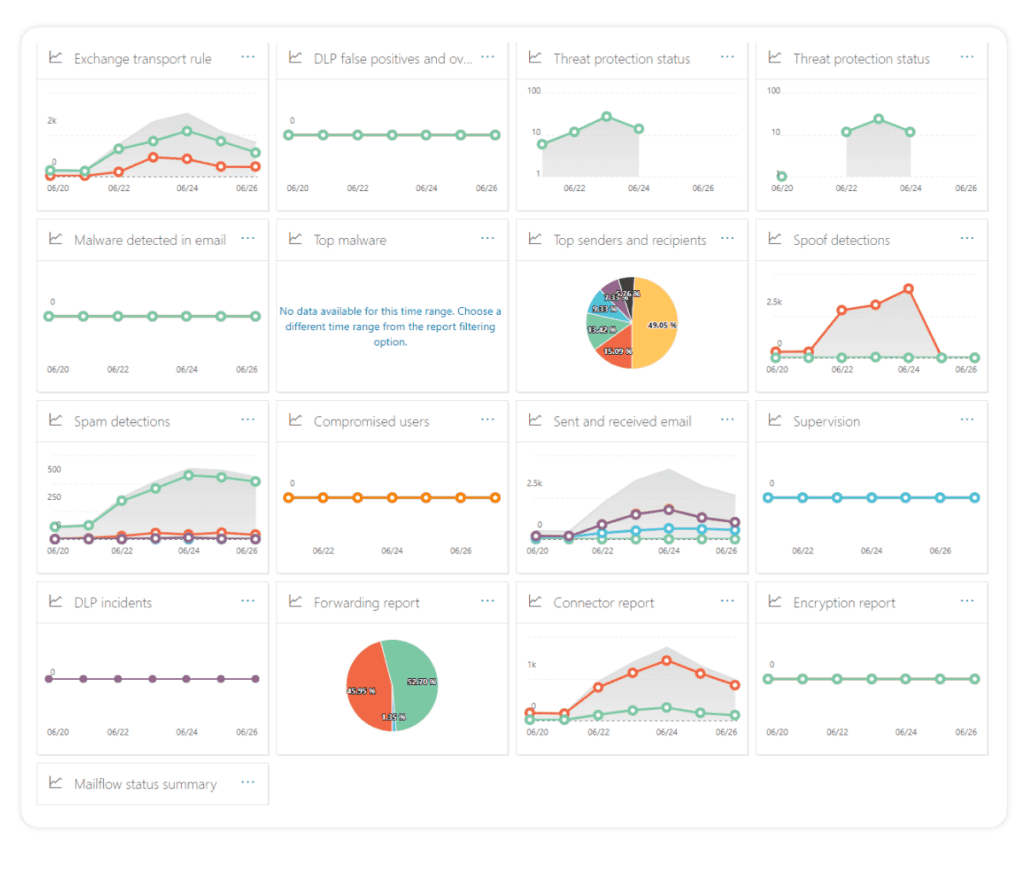
3. Security and Compliance Dashboard
The Security and Compliance Dashboard gives a quick overview of different events or threats within your environment. Most of the risks are from the Exchange workload, but the features also cover labels and DLP policies.
4. Microsoft 365 compliance center
With the Microsoft 365 compliance center, customers can scan their data to verify what kind of data is hosted within the system. Most often, this will include scanning for personally identifiable documentation across SharePoint, Exchange, and OneDrive workloads but also numerous other scans and compliance scores available as part of the Microsoft Compliance Score.
5. Multifactor authentication (MFA)
Multifactor authentication requires users to present two or more pieces of evidence (factors) when authenticating. Office 365 security has built-in support for MFA, and although it does require a little bit of manual work to enable it for each user, it is a must-have. Users can authenticate via mobile app, text messages, or calls. To further secure the login page, it is strongly recommended companies deploy custom branding for the login page.
6. Azure Conditional Access
You can further guard the access to the Office 365 tenant by implementing Azure AD Conditional Access functionality. It allows us to safeguard the tenant based on various conditions like location, IP address, and application usage. When combined with other AD user properties like department, it is easy to block users from, for example, the Marketing department to connect to Office 365 from a suspicious, non-company location.
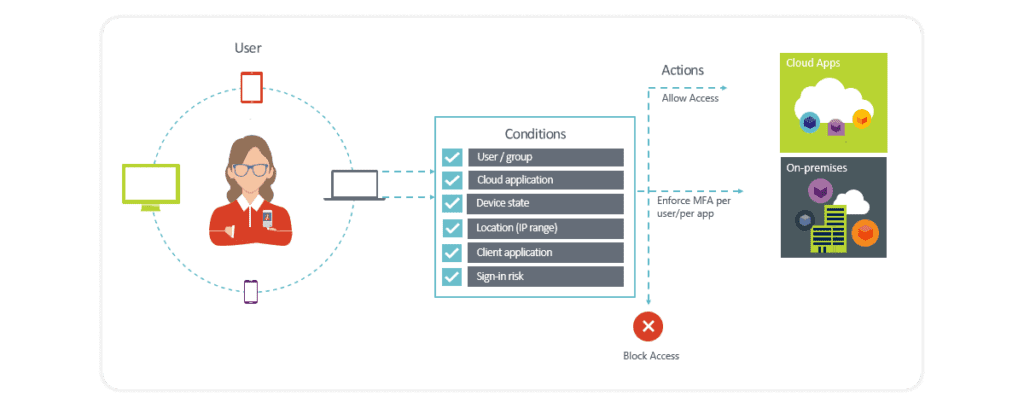
Azure Conditional Access is ideal to consider for organizations that have complex security requirements, as it offers several benefits. You can find out more about them in our blog post about using Azure Conditional Access.
7. Azure Information Protection
The most critical data in many Office 365 deployments is often stored in Microsoft Office documents. Azure Information Protection allows us to protect documents from being shared, and , as well as emails to be forwarded. In essence, it encrypts the document, and only authorized, hand-picked personnel can decrypt its contents.
The following file types are supported:
- Adobe Portable Document Format: .pdf
- Microsoft Project: .mpp, .mpt
- Microsoft Publisher: .pub
- Microsoft XPS: .xps .oxps
- Images: .jpg, .jpe, .jpeg, .jif, .jfif, .jfi. png, .tif, .tiff
- Autodesk Design Review 2013: .dwfx
- Adobe Photoshop: .psd
- Digital Negative: .dng
- Microsoft Office
8. Azure Identity Protection
The Azure Identity Protection is a premium Azure AD feature that helps detect potential risks connected with your Azure AD Users. It can help you detect various sign-in risks, which can be fine-tuned with the pre-built set of rules. On top of user-defined policies, this feature also analyses available data about typical user behavior. It helps detect unusual user behavior, allowing the administrator to block such users from accessing the system.
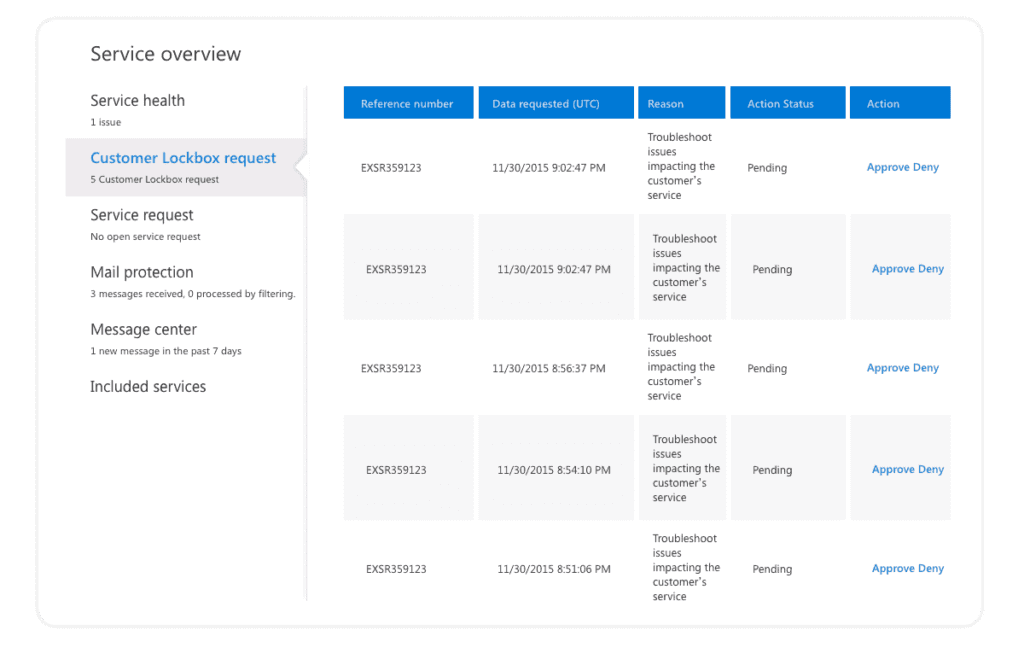
9. Customer Lockbox
Customer Lockbox allows Microsoft 365 admins to control when and if a Microsoft support engineer can access data in your tenancy. Say you have an issue with your Microsoft 365 service, and you open a support incident. In some cases, a support engineer might request access to data that causes problems (e.g., Microsoft 365 mailbox or a SharePoint Online Site). With Customer lockbox enabled, you can approve these requests, keep track, and define a timeframe to allow Microsoft support to access your data.
10. Cloud App Security
Securing various applications in the cloud presents a new challenge for IT. This is where the Cloud App Security Framework steps in, as it helps IT control numerous apps, logs, devices, and more. It helps control shadow IT, protects sensitive information in the cloud, and scans app logs for possible cyber threats and anomalies.
11. External Users and Guests
One of the essential capabilities of Office 365 is inviting external users to collaborate with you in SharePoint, OneDrive, and Teams. However, make sure you choose the appropriate sharing policies that would work for your organization. Not all end users are IT savvy enough, so you might want to limit external sharing. The best practice is to allow only people preapproved by IT, called Existing Guests, to participate in the collaboration. For more information, please check out our Microsoft Teams guest users access and management guide.
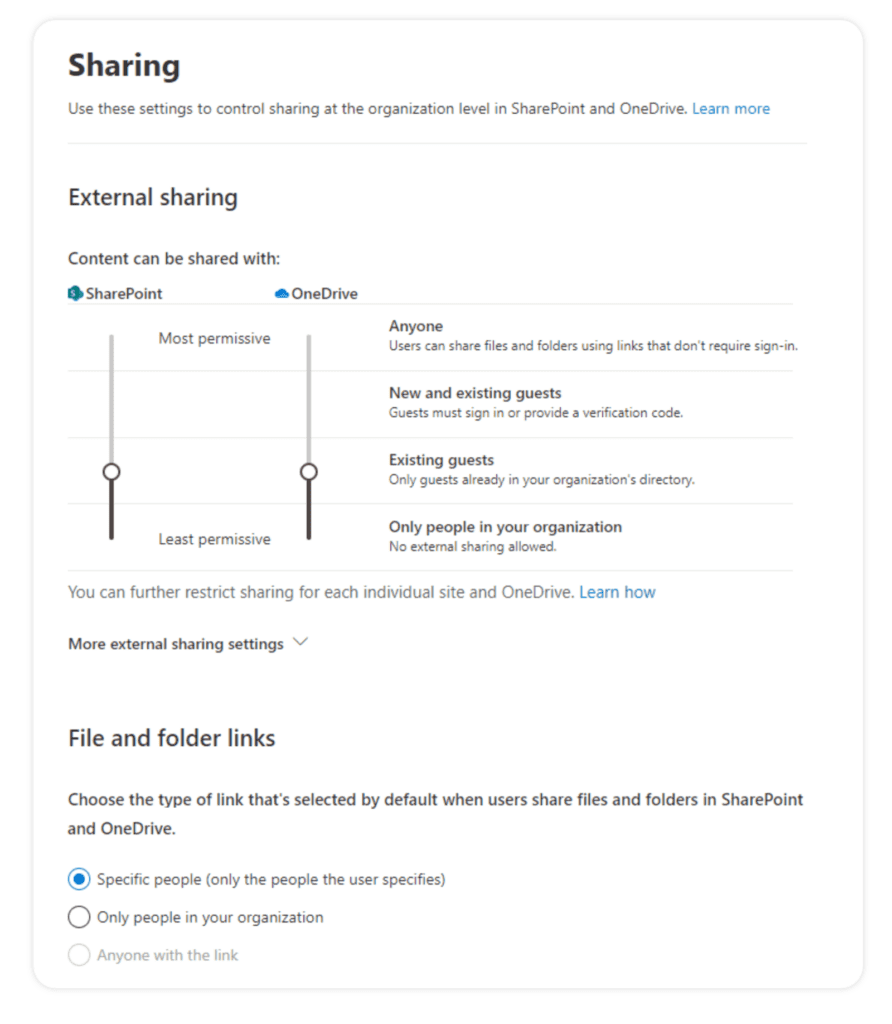
12. Sharing Links
On top of external sharing controls, it is crucial to configure the types of sharing links your users can generate by default. The best practice would be to stick to the option “Specific people (only the people the user specifies).” With this option selected, even if a user forwards a link to someone else in your organization, this user would not be able to open the document.
To dive deeper into how external sharing affects security, check out our external sharing in Microsoft 365 webinar, where Microsoft MVP Andy Huneycutt will show you the ins and outs of external sharing.
13. Access Reviews
In our previous blog post, we talked about Office 365 Access Governance where we discussed the Azure AD feature called Access Reviews.
Office 365 administrators can use Access Reviews to manage memberships and access rights – ensuring streamlined user onboarding and offboarding. You can also use it for periodical reviews of users with privileged access.
Syskit Point will automate your access review and include all important stakeholders in the process. Admins can schedule automated requests for teams, groups, and site owners to review their services’ access regularly. With this, collaborative governance approach, owners are becoming responsible for governing their own resources.
In the cloud, the critical component for the security of business assets is the integrity of your users, especially those who have privileged access to your resources. Multiple accounts and different roles could be considered privileged in complex environments such as Office 365 and Azure. It is of paramount importance to limit their number as soon as possible. Below, I listed a couple of steps that you should do to keep your Office 365 security ironclad!
Office 365 security best practices checklist
- Turn on Azure AD Privileged Identity Management – this allows you to get notifications on each privileged role change.
- Identify users in the following roles: Global administrator, Privileged role administrator, Exchange Online administrator, and SharePoint Online administrator.
- Make sure you have at least two emergency users or “break-in” accounts in case of AD sync failure. Consider turning MFA off for these accounts in the event of MFA service failure.
- Turn on MFA on all other privileged accounts.
- Make sure you have reviewed and configured external sharing for SharePoint, OneDrive, and Teams.
- Make the checking of the Security Score and Identity Secure Score part of your regular IT monthly checkups. Make sure to mark tasks to move these tasks into an appropriate status, e.g., Planning, Done, etc.
- Make sure auditing is enabled today!
- Should you need longer retention of Office 365 audit logs, consider 3rd party tool options.
- Every user connecting to Office 365 should have MFA enforced.
- Deploy a custom, branded login page for Office 365.
Phase two for excellent Office 365 security
- Conduct an inventory of services, owners, and admins.
- Identify Microsoft accounts in administrative roles that you need to switch to work or school accounts.
- Ensure separate user accounts and mail forwarding for global administrator accounts.
- Make sure you change the passwords of administrative accounts.
- Turn on password hash synchronization.
- Require multifactor authentication (MFA) for users in all privileged roles and exposed users.
- Configure Identity Protection.
- Obtain your Office 365 Secure Score.
- Review the Office 365 security and compliance guidance.
- Establish the owners of the incident/emergency response plan.
- Secure on-premises privileged administrative accounts.
- Complete an inventory of subscriptions.
- Remove Microsoft accounts from admin roles.
- Monitor Azure activity.
- Configure conditional access policies.
That’s it from me. I hope you will find my tips useful. If you want to learn more – read our Microsoft 365 security guide in PDF.

