Common oversharing scenarios in Microsoft 365
As we mentioned in previous sections, oversharing in Microsoft 365 is not usually done on purpose; it’s a byproduct of collaboration and a lack of correct settings. In this section of the governance handbook, we will look at specific collaboration tasks that cause oversharing and how users can avoid these common oversharing scenarios.
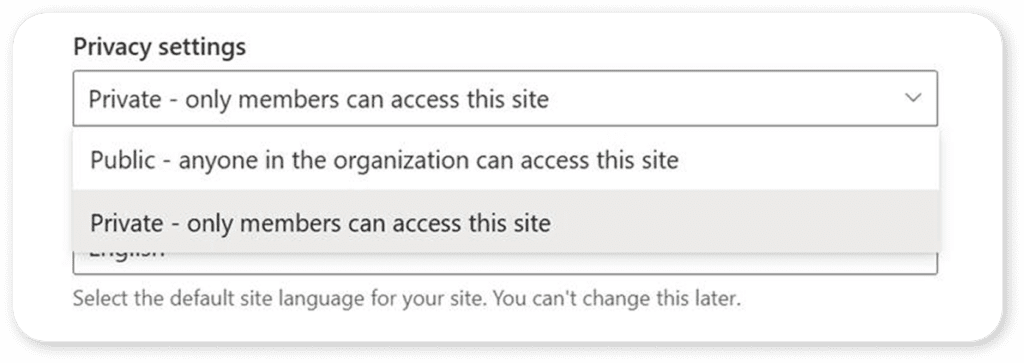
Site privacy set to public
A huge cause of oversharing in organizations is simply the wrong site or group-level settings. If the site is set to public, everyone has access to it, and it will show up in their search results. And, of course, Copilot can show that information to everyone.
Your reaction to this first item might be a chuckle because it’s so simple, but you would be surprised how many sites and groups are misconfigured inside each tenant.
The default sharing option is everyone
A bold but true statement: All users are lazy, including us at Syskit. When you want to share a file, you probably just click the Copy link, and you do not spend the time for each link to choose the right audience and permissions. Users will always take the easiest path to achieve a business need (sharing a file in this case), and if our default links are “Anyone with Edit permissions” or even “People in my organization”, you will have a lot of overshared content.
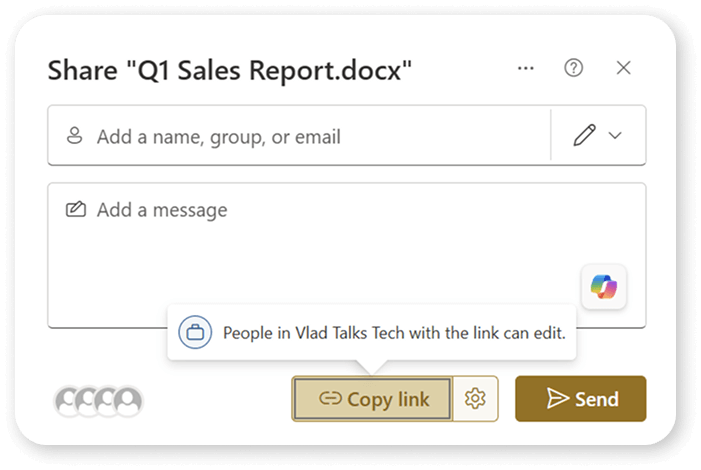
Instead, your default permissions should be as restrictive as possible, so either “People which already have access” or “Specific People”. Even if you allow anonymous on your site, we want your user to consciously decide to make the link more permissive instead of having it as the default option.
Use of “everyone except external users” domain group
Most Microsoft 365 tenants include a security group called “Everyone Except External Users”, or EEUU for short, which contains all your internal users. Too many users often use this group to share content because it’s easy; it’s a single group, and everyone who needs access has it. While it works, and yes, it’s faster than adding 10-15 people individually, you just created an oversharing problem, as hundreds, if not thousands, of people who didn’t need access now have it.
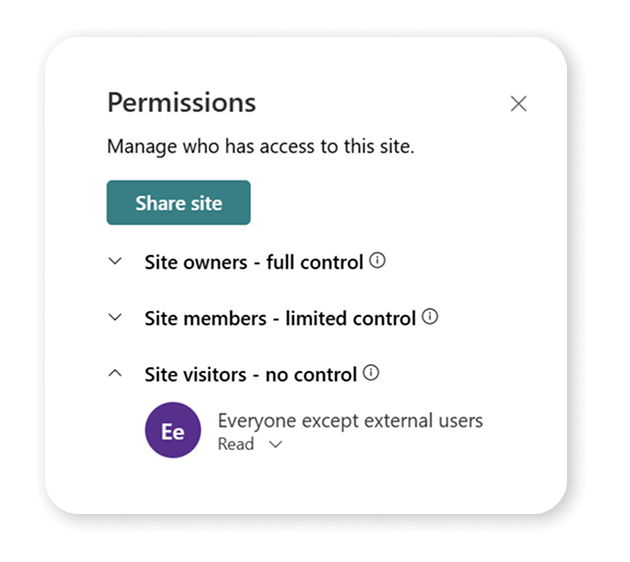
Over the years, this became such a big problem that Microsoft disabled this group by default for new tenants. If you still want to use it, an admin needs to use PowerShell to make it available. This also applies to any custom group that your IT admins might have created, like “All Company” or similar.
Broken permissions at the site and folder levels
When asked, most site owners try to keep sites accessible only to people who need them. However, when they check permissions, they only check site-level permissions or group-level permissions. Unfortunately, every time someone shares just a file with more permissions than the site has, they break permission inheritance, which means the artifact (folder, item, or document) now has its own permission, separate from the site.
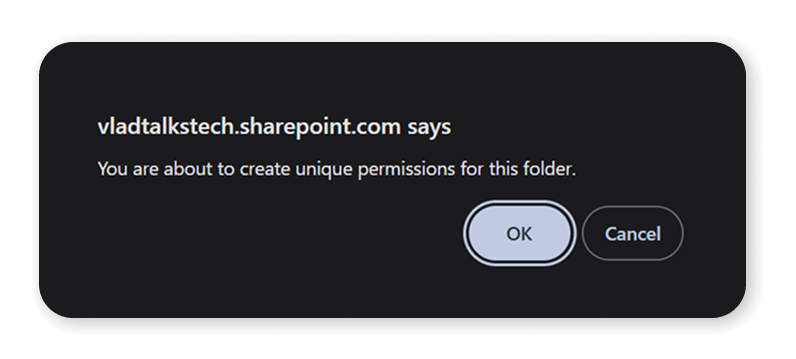
Unless the site owner goes into each broken permission in their site, which most owners rarely do, those will fly under the radar and oversharing will persist for a long time.
Uncontrolled external sharing
While many administrators might say external sharing is bad from the start, we at Syskit usually disagree. We would much rather have users share content externally from SharePoint, where we know who has access to what, and we can have a strong audit log to know who accessed what and when.
The big problem with external sharing is when there are no guardrails on who can share what externally and where. By default, if you have external sharing on for the organization, users can share with any domain, and you might have accidents where someone shares content with the wrong external user.
Let us ask you a question: Out of all the external users who still have access to any content in your tenant, what is the chance that some of those users don’t even work at those companies anymore? What if your external company recycles e-mail addresses when John Smith leaves, but John Stallone joins, and they both get the john.s@company.com e-mail address?
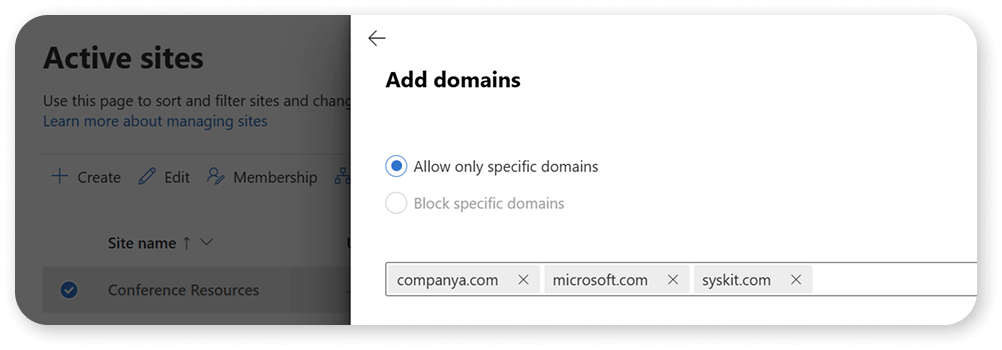
Microsoft 365 offers many options, such as setting allowed domains for each site or deciding which users are allowed to share externally. Unfortunately, most companies do not use them.
Oversharing in Microsoft Teams
A final cause of oversharing we will cover in this section of the handbook is Microsoft Teams. Most organizations use standard and private channels to collaborate in Microsoft Teams. And no one can blame those organizations since standard channels and private channels were there first, but one of the limitations is that you cannot add someone to a private channel or only to a standard channel. First of all, you need to add them to the whole team.
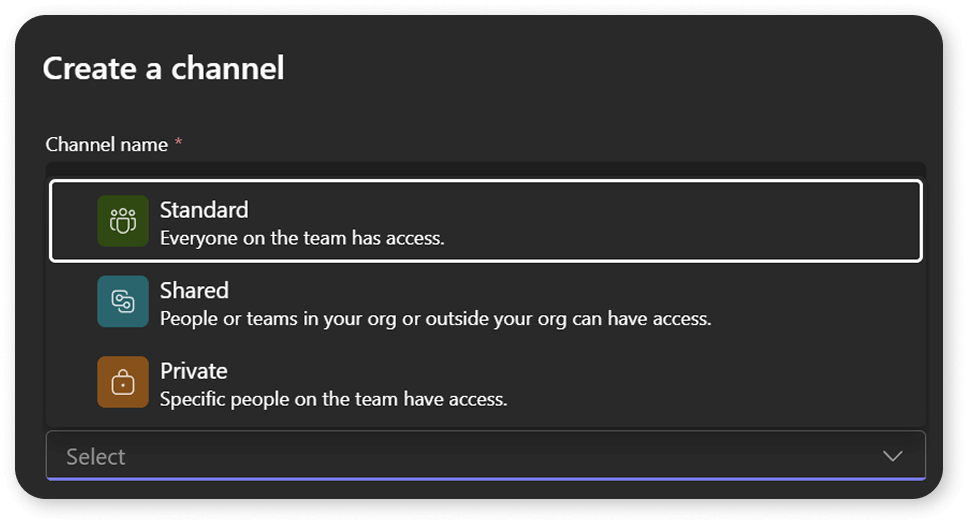
The best solution would be shared channels, as they allow you to share the channel with the whole team, but if needed, you can add someone only to the channel, ultimately reducing oversharing. We know a lot of administrators are disabling shared channels due to the external sharing capabilities. However, did you know that you can enable shared channels for internal sharing only?
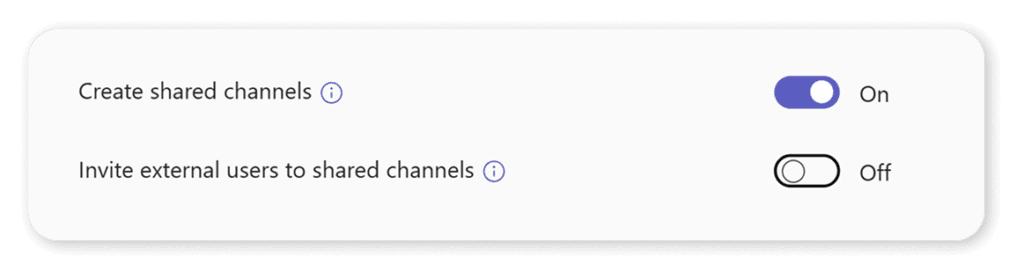
This can be a great way to start using them, reducing information duplication and oversharing with a single tool.
Oversharing scenarios in Microsoft 365
In this section of the handbook, we examined the most common causes of oversharing, most of which are simply byproducts of collaboration. Oversharing will creep into your tenant one site or team at a time if not configured and monitored properly.
The good news is that we can reduce oversharing at the source simply by configuring our admin centers. We’ll cover this in the next section of our guide.