Why is oversharing a risk?
We now know what oversharing is, but, in reality, does it really matter? What is the real impact of Alex having access to a few extra files he shouldn’t?
In this section of our Oversharing guide, we will talk about why oversharing is a risk and give some concrete examples from the field on why oversharing can be a risk to your organization.
Security concerns
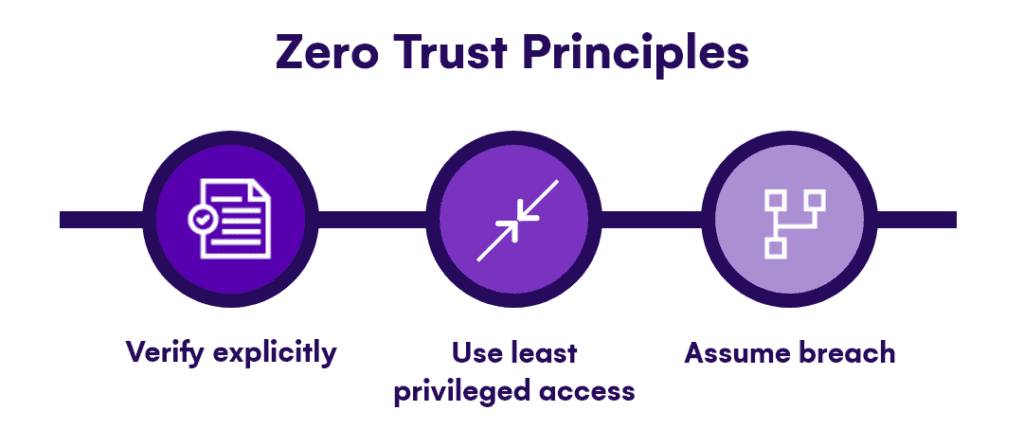
When talking IT security we often refer to “Zero Trust Architecture“, and without going into all the details, one of the three principles of zero trust is use least privilege access, or you might have also heard it called “Just Enough Access” to do your job. But how does this apply to our oversharing scenario in Microsoft 365?
Since you are reading this guide, we assume you are at least interested in security, but we are certain you know a colleague (or even two!) who would instantly fall for a properly crafted phishing email. You know who that person is.
Now imagine that instead of the test phishing email sent by your organization, this time it’s real, and a malicious user has taken control of their account. How much data would they have access to?
If you implemented the principle of just enough access, they only have access to the 1 or 2 projects they work on: your Intranet, and a few other sites. However, if you never removed that person from any past projects they worked on in the 6 years they’ve been at the company, your potential data leak grows from 1 or 2 projects to maybe even 30. Even worse, what if you automatically share everything with “Everyone Except External users”?
Security professionals often say there are two types of companies:
- Those who got hacked.
- Those who don’t know they got hacked yet.
Whether you choose to believe this or not, eventually, one of your users will fall victim to a phishing attempt, an open device left at a coffee shop, or a malicious state attack. When it happens, do you want the attacker to have access to 5 sites or 50? This is why you need to limit oversharing and follow the security principle of Just Enough Access. Don’t worry; later in this guide, we will cover some of the tools available to make sure this doesn’t happen, and you don’t have to deal with the stress.
Compliance concerns
I know compliance isn’t the most fun topic to talk about, but it’s probably one of the most important ones. If you do not follow your compliance requirements, your company can face major fines or even be shut down by regulators. We won’t go into specific regulations like GDPR, HIPAA, or PCI DSS, as each company needs to follow different regulations, but you (should) know which one applies to you.
One of the things we need to mention as we talk about compliance is that not all content has the same importance in your tenant. Fair enough, every data leak is bad, but if someone overshares your vacation policy, it won’t have a big impact on your business. However, if someone creates an anonymous link (intentional or not) to a list of patients or clients you signed an NDA with, that will have a huge impact on your organization.
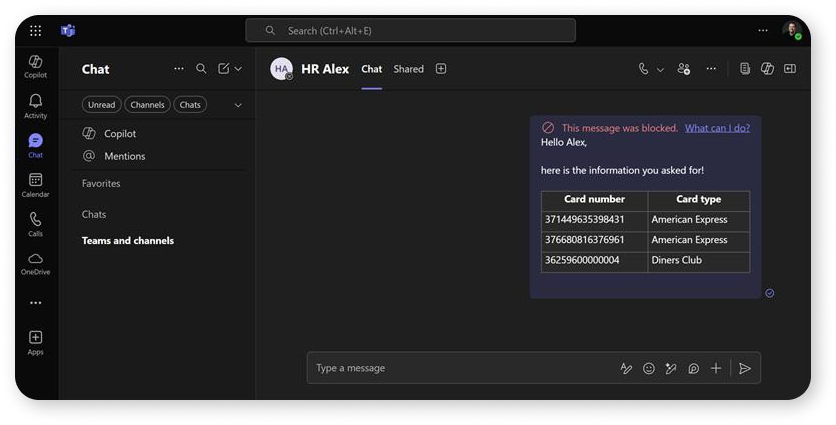
Oversharing can also be sharing sensitive data (credit cards, client lists, patient information, for example) in locations where they shouldn’t be allowed to. Sometimes, simply having some of your internal employees have access to this information is a compliance violation and can be the difference between your company being around in 10 years, or not. Remember that Microsoft offers tools to automatically block this information when overshared; unfortunately, not enough companies use them.
Operational risks
While security and compliance are important, there is a reason why everyone in your organization does not have access to all the information. Imagine if everyone had access to every single change your board wants to make over the next 12 months? What if someone accidentally discovers discussions about layoffs in the next quarter and spreads the rumors? What impact would that have on your business operations and, even more importantly, integrity?
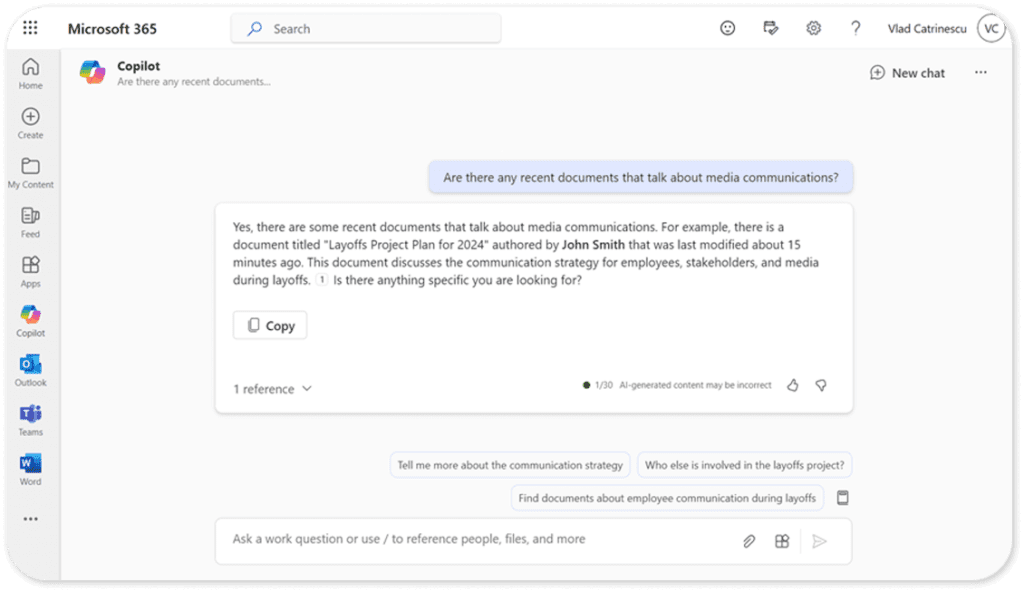
While in the past, users had to know what to search for in order to find overshared content (in some cases even dig), AI is the great amplifier. A user can ask a question about something they do daily, and overshared content could be presented as in the example below. What if my user shouldn’t have had access to that project plan?
Imagine if everyone had access to others performance reports, bonuses, or company strategy? With 63% of data breaches coming in from insiders, even if data does not leak to the outside world, it could bring the productivity of your organization to a halt.
Oversharing QUIZ: Do you overshare?
Here are a couple of questions that will help you see if your organization is oversharing:
- Do you still have access to projects / sites that you do not work on anymore?
- When you share a file / site do you manually go and select the least permissive option?
- When was the last time you reviewed permissions and removed people from the sites that you own?
- If you try to share a file including a credit card on your intranet, will the system let you?
- What about sending it via email to an external user?
- When was the last time you reviewed your shared file permissions in OneDrive?
So, are you oversharing?