Share smarter: Microsoft 365 oversharing solutions
Table of contents
In our sixth episode on maximizing your Microsoft 365 potential, Vlad Catrinescu and Drew Madelung discuss how to control Microsoft 365 oversharing. They explore the nuances of Microsoft 365 oversharing, its implications, and how you can effectively manage it within your tenant.
Their previous episodes discussed orphaned workspaces, orphaned users, teams ownership, and inactive guest users.
Watch the entire episode about Microsoft 365 oversharing below and read some of the key takeaways in this blog post.
Understanding Microsoft 365 oversharing
Microsoft 365 Oversharing occurs when users grant excessive access to files and resources within the Microsoft 365 environment. Users share links without considering the available settings, leading to potential security risks. They take the easy route of sharing with a broad audience and don’t consider the principle of least privilege. As a result, unauthorized individuals may gain access to sensitive information, posing significant security risks to your organization.
Simply put, users share content with everyone and then they never review it, or even if they share it with the right people at that time, they never go back and review permissions regularly. What happens is that you have users out there who still have rights to things that they do not need for their day-to-day jobs.
Microsoft 365 oversharing and Copilot
Another thing to consider is oversharing and preparing for Microsoft Copilot or if you look at some of the things in the news around people who have had too much access to SharePoint is that an account gets breached and they’re able to go find information that they weren’t supposed to because of what they have access to in SharePoint.
But, when it comes to getting ready for Copilot, it doesn’t matter if the intention is malicious. Copilot will take all of the data that it can in, including sensitive data. Such unprotected and overshared information can be easily accessed through Copilot, posing a severe security threat.
So, there’s this high-level concept of Microsoft 365 oversharing, but the more specific one is at the granular level of sharing things with organizations or sharing things through emails or sharing sites. It leads to this potential visibility of content that you weren’t necessarily intended to see.
Zero-trust security
Zero trust is a security concept that is a way of thinking about all your digital assets today as a user: I should only have permission for the things that I need for my job today. I should not have access to things that I might need in the future or things like that. Whenever I need them, I’ll get access to them. But today we want to limit my user to only having access to the minimum amount of data I need to do my job. This way, if I ever get compromised. We are still limited in the amount of data that is leaked versus if I had access to everything.
Why restricting external sharing can potentially be less secure
Some organizations like to restrict external sharing completely. As an admin, you’d probably think that having the least permissive option is the most secure one, right? Because we’ve been conditioned and trained in the past to say that no external access equals more security. But from a security point of view, you’ll lose points in Microsoft Secure Score which analyzes your environment and gives you a score based on your settings.
If you turn off external sharing, you will lose points. Why is that? Because there is a business need for users to work with external entities to share files. If you don’t enable people to do it inside your enterprise tools such as SharePoint and OneDrive, what are they going to do?
Now you have shadow IT, you have files in other systems you have no idea about. It’s better to enable your users to do all of this in M365 where you have all your settings on guest users, you have audit logging, you have sensitivity labels, and all those things you can do to secure your files. If you allow shadow IT, you’ve just lost control. It’s maybe the least secure option here, which again, is a funny thing to say that enabling external access is more secure than not doing it.
The risks of Microsoft 365 oversharing
Microsoft 365 oversharing poses various risks to organizations, including:
Increased exposure to data breaches: Granting unnecessary access to files increases the likelihood of data breaches. Unauthorized users may gain access to sensitive information, leading to potential data leaks and compliance issues.
Lack of control and governance: When files are shared indiscriminately, administrators lose control over who can access and modify them. This lack of governance complicates data management and auditing processes, making it challenging to track and enforce security policies.
Compliance violations: Microsoft 365 oversharing can lead to compliance violations, particularly in regulated industries where data privacy and security standards must be maintained. Unauthorized access to sensitive data may result in severe penalties and reputational damage.
Controlling Microsoft 365 oversharing
To mitigate the risks associated with Microsoft 365 oversharing, admins can implement various strategies and tools:
Fine-tune SharePoint Online sharing settings: SharePoint Online offers robust sharing settings that allow admins to control internal and external sharing. By configuring sharing permissions at the tenant level, admins can enforce security policies and prevent unauthorized access to sensitive content.
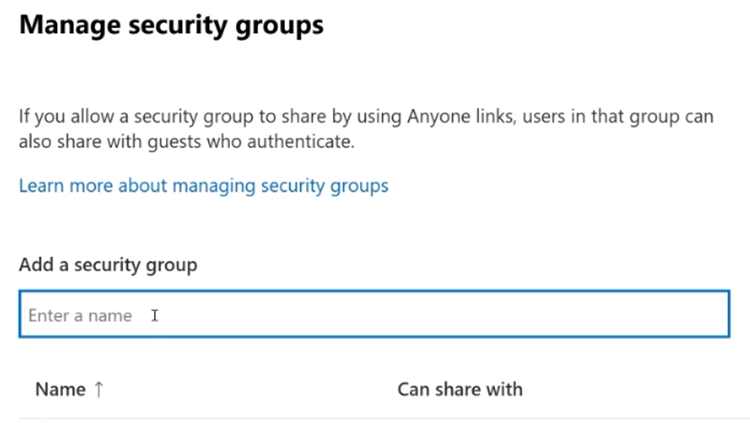
Leverage security groups: Utilizing security groups enables admins to restrict external sharing based on user attributes such as department, location, or training level. By defining specific criteria for external sharing, organizations can ensure that only authorized users can share files externally.
Implement guest access expiration policies: Guest access expiration policies help admins manage oversharing by automatically revoking access for external users after a specified period. This feature ensures that external collaborators only have access to shared resources for the duration needed, reducing the risk of prolonged exposure.
Educate users on best practices: Educating users on the importance of responsible sharing practices is essential for preventing oversharing. Admins should provide training and resources to help users understand the implications of oversharing and how to securely collaborate within Microsoft 365.
SharePoint Premium
One of the tools you also have to control oversharing is data access governance reports, which are part of SharePoint Premium. Previously named Microsoft Syntex, with a SharePoint Advanced Management License (SAM). One of the reports you have is sharing links. You go to view reports and then you have three reports that you can run: the anyone links, the people in your organization links, and then the specific people links shared externally.
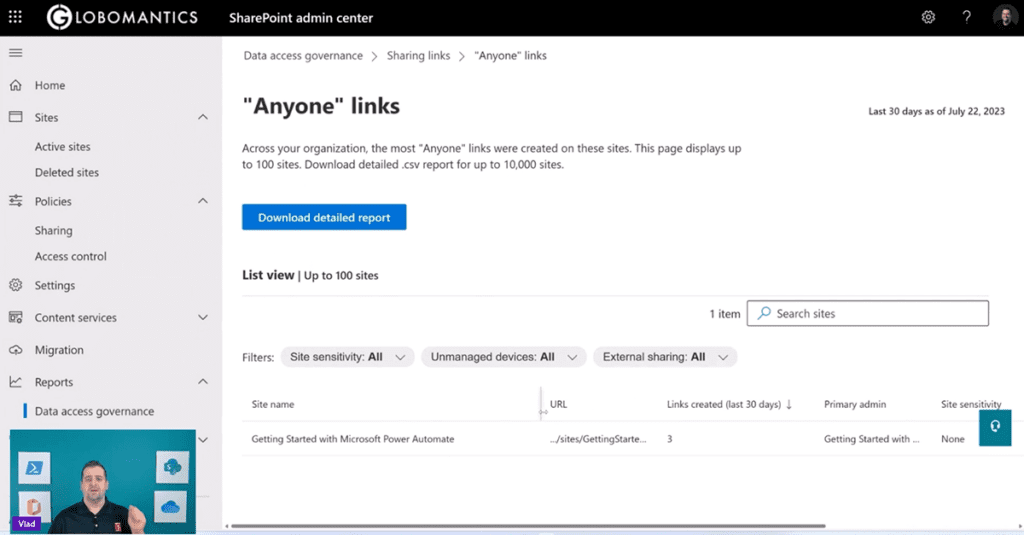
You can click on one of these reports and then you can see, “Hey, you know what’s in this site here? I have the URL of the site, I have 3 links of type anyone in this case that got created. I can see the site sensitivity. I can see do I have external sharing on or not.”
Sharing model overview
When people share a link, do they always look at all the available settings or do they just click on “Copy link” and then if it works, click send? Users often overlook sharing settings and simply copy links, resulting in billions of instances of oversharing every month.
Default sharing settings are often too permissive, allowing anyone with the link to access and even edit documents.
Default sharing settings
Admins can configure default sharing settings to be more restrictive, such as limiting access to specific people instead of allowing anyone with the link to access. It’s important to educate users on the significance of default sharing settings and encourage them to be mindful of sharing permissions.
External sharing settings
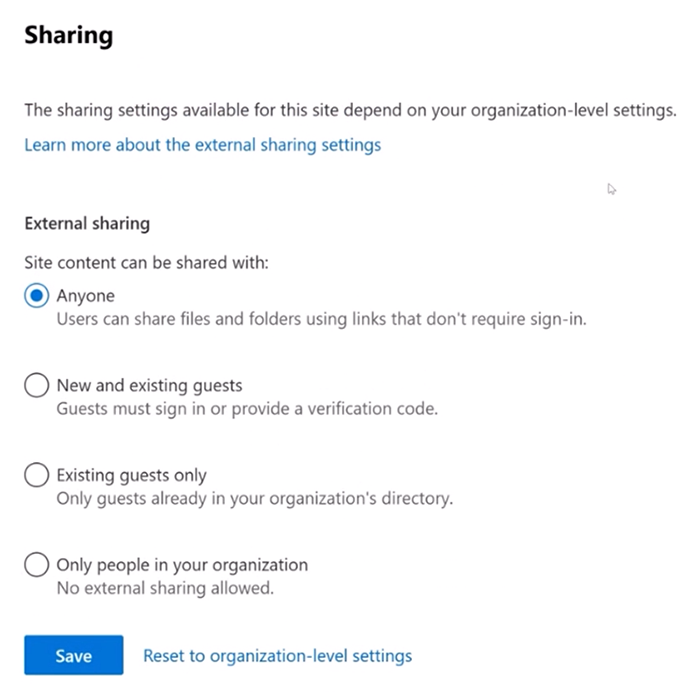
Admins can control external sharing settings both at the tenant and site levels.
Implementing restrictions at the site level provides granular control over sharing permissions, especially for collaborations with specific vendors or partners.
Options include setting link expiration dates, restricting access to view-only, and specifying domains allowed for sharing.
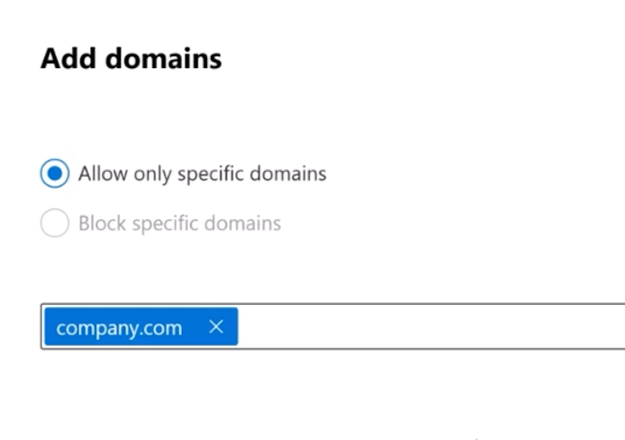
Allow list of domains
You can add domains from external organizations that you work with on an allow list that will only allow sharing with specific external domains. However, every time you work with a new organization, you will have to add them to the allow list.
Many organizations use allow lists to invite anyone from the companies they work with. This also prevents them from inviting somebody from a random company.
Block list for domains
You also have the option to block specific domains. Let’s say that you work for CompanyA and CompanyB is your biggest competitor. You can use the block list to say you can share with anyone in the world except CompanyB.com. But in practice, more organizations work with allow lists than block lists.
Site-level sharing controls
Site-level settings can further restrict sharing permissions, ensuring that sensitive sites remain accessible only to authorized personnel.
Restricted site access policies prevent unauthorized users from accessing sensitive content, even if explicitly granted permission. This is an amazing feature to prevent internal oversharing on your most sensitive sites.
Monitoring and reporting
Access Reviews can also be used on all internal and external users that are part of a group to make sure that they still need access to that group.
Data access governance reports (DAG) can help you monitor oversharing by providing info that helps you govern access to SharePoint data.
PowerShell scripts are useful tools for monitoring and managing sharing activities. You can always create your own PowerShell scripts to find out who has access to what. The APIs are there, but it can take quite a bit of time to figure out all the reports you might want.
Microsoft Graph Data Connect provides advanced reporting capabilities, allowing admins to analyze sharing trends at scale. Microsoft Graph Data Connect solution gives the solution for moving data in which Microsoft will help position that data in a way that you can consume it. So, it stages it and gives you a way that you’re not constantly hitting the graph APIs to get the audit information for sharing or sites.
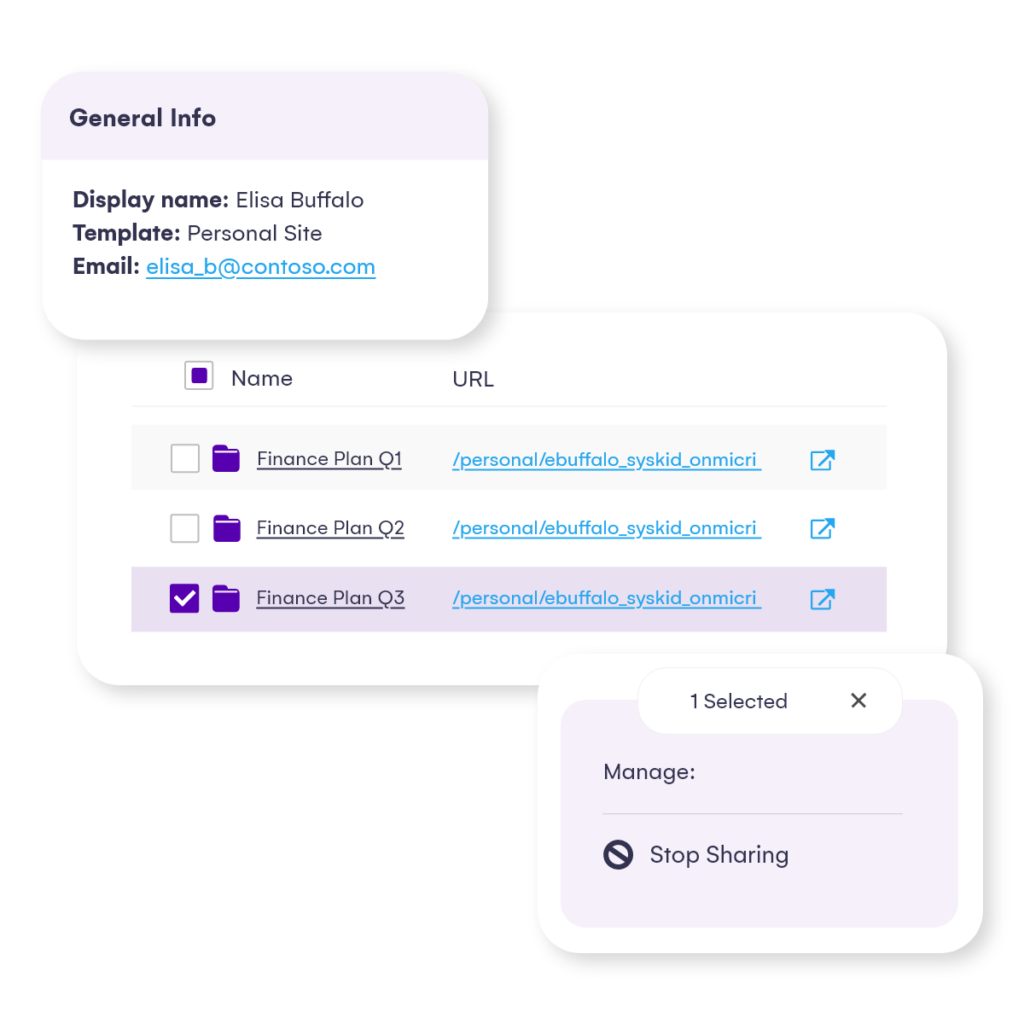
Third-party tools like Syskit Point offer pre-built reports and solutions for Microsoft 365 oversharing detection and management. Syskit Point’s powerful reports solve your visibility issues by showing both internal and external users’ actions across SharePoint Online, Teams, Microsoft 365 Groups, and OneDrive, in a single dashboard. You can automatically review external sharing and guest users – periodically or whenever Point detects them as inactive. As well, you can generate a list of all anonymous sharing links. You can add or remove your users, members, guest users, and sharing links across your environment with one click.
Take control of Microsoft 365 oversharing
Controlling Microsoft 365 oversharing is crucial for maintaining data security and compliance within your Microsoft 365 environment. By implementing robust sharing settings, leveraging security groups, and educating users on best practices, admins can mitigate the risks associated with oversharing and ensure that sensitive information remains protected. Remember, proactive measures to prevent oversharing are key to safeguarding your organization’s data and reputation in an increasingly interconnected world.
For more info on Microsoft 365 oversharing, Vlad Catrinescu hosted a webinar titled Mitigating Microsoft 365 oversharing risks. Check out the video below.
In the next episode
In the next and final episode in our video series, Vlad and Drew give insights into SharePoint Online storage management and reporting strategies.