What is Shadow IT? Here’s the overview of it along with M365 governance best practices
Table of contents
The rapid development of cloud-based services has caused a rise in practices that come under the umbrella of shadow IT. Typical examples of shadow IT include the use of:
- Data storage devices e.g., hard disks, smartphones, and flash drives for data transfer.
- Cloud storage like Dropbox, OneDrive, Google Drive, and storage provided by smartphone companies.
- Social messaging apps like WhatsApp, Skype, and Messenger.
- Personal email accounts like Gmail and Yahoo.
Why do employees use Shadow IT?
In this era of increased competition, employees focus on delivering good results in the shortest period to meet efficiency requirements set by the organization. This fact naturally paves the way for them to try things out of the box and make use of technology, and hence employees migrate to shadow IT practices because they get their job done quickly.
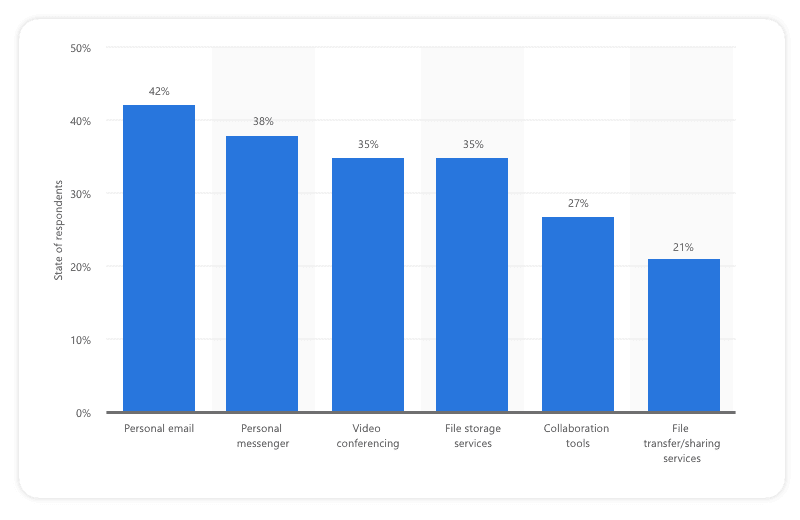
Not keeping up with modern technology, and lack of communication by the IT team with other employees, also promotes shadow IT. In some cases, timely approval of IT services may serve as a bottleneck to the efficiency of employees, and a delay in the approval of assistance can promote shadow IT practices. This is when employees start seeing IT departments as an obstacle to their success. Statistics from 2021 show the usage of shadow IT.
21% of respondents are using file transfer/sharing services for work without the approval of their employers’ information technology team.
A common scenario is that employees are asked not to send documents to anyone in an editable format (e.g., Word or Excel), however, for this task, they are not provided with any tool by IT teams. Consequently, they use an online PDF converter which is a practice related to shadow IT because the data gets exposed to the internet.
Benefits of Shadow IT
- Boosts innovation, productivity, and efficiency of employees.
- Enables employees to work from home in some unavoidable circumstances e.g., the very recent global COVID-19 emergency.
- An improvement in the Key Performance Indicators of the organization/business.
- Increased flexibility and reduced burden for IT teams so that they focus on more business-critical tasks.
- Delegation of responsibilities from a single team (IT) to an individual level.
Drawbacks of Shadow IT
1. Data Loss
If the IT department is not aware of an application or software in use, they simply cannot prevent it. In case of data loss, there may be no way to backup or recover the critical data. Moreover, in the case of the absence of an employee, the organization may never be able to access the critical data.
2. Security Risk
Exposing organizational data to shadow IT systems implies that the IT team has no control over it. Considering sensitive projects, this corresponds to a security threat. There is a good chance of data being leaked, malware being introduced in the network, or the cloud service itself suffering from a cyber-attack. Hackers can use tricks like phishing and ransomware to hack IT devices.
3. Inconsistent Analysis
Shadow IT services are often used to store data because of greater control or ease of sharing among stakeholders. Changes to files may cause inconsistency in data if different versions of files are stored in multiple locations or shared through different channels.
4. Non-compliance
Shadow IT activities increase unmonitored data transfers, making it difficult to comply with data regulation initiatives such as Sarbanes-Oxley Act (US), Defense Federal Acquisition Regulation Supplement (US), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR).
Microsoft 365 and Shadow IT
To overshadow the risks of shadow IT, instead of trying to beat these cloud-based applications, a better choice for the IT teams might be to join them by taking a bit of control on the M365 environment.
In the corporate sector, Microsoft 365 (M365) provides opportunities to teams to become more innovative, productive, and efficient while always staying connected even when working remotely. M365 integrates world-leading business applications such as Word, Excel, PowerPoint, OneDrive, Outlook, Teams, Groups, and SharePoint along with support for Windows in a single package. Keeping in view the continuous increase in the use of Software as a Service (SaaS), M365 provides a cloud-based service to its client organizations for the successful building of a connected workforce. Depending on the size of the business, M365 provides cloud storage space.
With the provision of such a competitive advantage, the task of protecting the M365 environment has become inevitable. Successful organizations manage to build the trust of their clients and that is the key to their success. With M365, protecting the integrity, confidentiality, and availability of the personal data of customers has emerged as a new challenge. Cloud-based applications use the web for data transfer which gives rise to threats of cyberattacks.
Cyberattacks on the M365 environment are carried out in the form of email-based phishing or spear-phishing attacks, automated credential stuffing, or guessing attacks. In a phishing attack, the user is asked to open a fake link (website) or email, following which the credentials are demanded and the attacker hijacks the credentials to break into the system and the sensitive information is compromised.
Moreover, with M365, employees now share a common workplace which calls for regularizing permissions to sensitive information. This calls for prioritizing security and data governance in M365 environments.
M365 Governance Best Practices
The success of IT teams’ governance in this era is attributed to the provisioning of secure cloud services to the organization. Without an effective governance policy, cyberattacks, shadow IT practices, and malicious activities may go unnoticed and unaddressed. Some of the best governance practices in the M365 environment may serve as a solution to shadow IT.
- Team and site sharing – Controlling sharing of teams, groups, and sites to people outside your organization.
- Restricted site and file sharing – Restricting site, file, and folder sharing to members of a specific security group.
- Restricted group creation – Restricting team and group creation to members of a specific security group.
- Audit logs – Keeping a record of who has access to what, who has downloaded what. Moreover, tracking activities of all users and admins.
- Domain allow/block – Restrict sharing with people outside your organization to people from specific domains.
- Multi-factor authentication (MFA) – Microsoft recommends using MFA (for login) to prevent unauthorized access to the M365 environment.
Syskit Point to the rescue
M365 offers an integrated solution for businesses and enterprises. With its cloud storage, it almost eliminates the need to adopt shadow IT practices by employees. Microsoft uses multiple encryption methods (BitLocker, DM-Crypt, Internet Protocol Security, and Transport Layer Security), protocols, and ciphers to help secure customers’ data in its cloud. Moreover, the M365 E5 license provides advanced security and threat protection features thus minimizing the risk of cyberattacks.
However, to protect intentional shadow IT practices, IT teams need to tighten the governance practices in their M365 environment. To this end, Syskit Point is a great addition to the M365 environment as a central point for governance and security. With its boosted security and compliance features, it enables users, admins, owners, and auditors to rediscover M365 in a better way. Syskit Point is a collaborative web-based application that runs on top of the M365 environment. Syskit Point uses the Azure Active Directory (Azure AD) consent framework to connect to the tenant to provide users with maximum safety when using the application. Point helps to declutter the tenant and provides some powerful features in the battle against shadow IT.
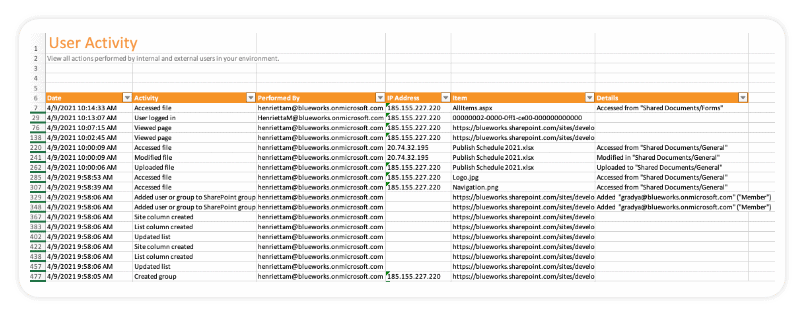
1. Security Alerting
Point sends regular notifications promptly through email. By configuring real-time security alerts, an admin can track activity outside a specific IP address, activity by a specific user, or a user type – external or internal. Moreover, the tracking goes back unlimited in time.
2. Microsoft 365 & SharePoint Online reporting
From a security point of view, anonymous links are the worst. The dashboard in Point shows an overview of inventory, permissions, and data in a single view. With its bulk user management feature, it issues a warning in case there are anonymous links, inactive content, and orphaned groups.
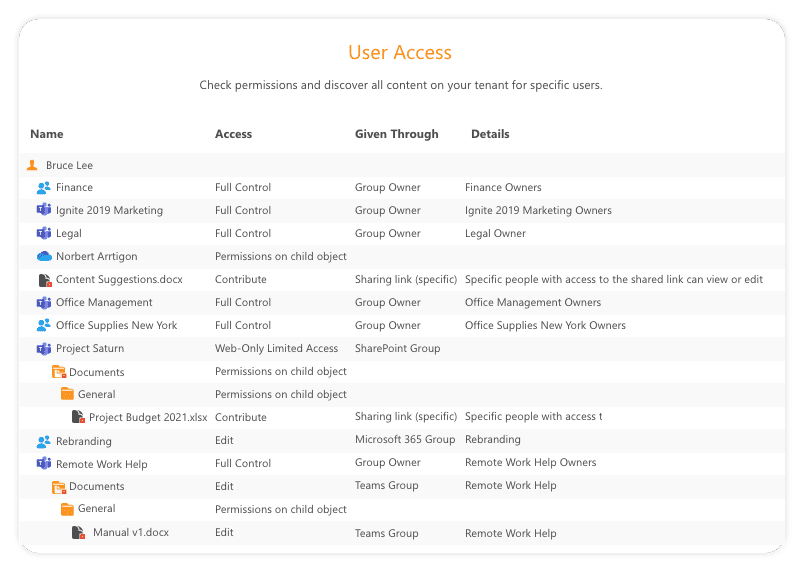
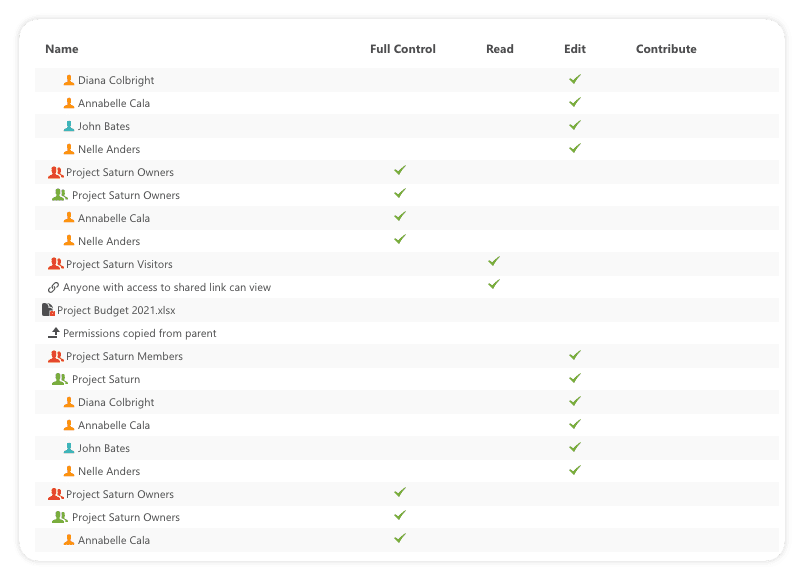
3. Permissions Reporting and finding User Access rights
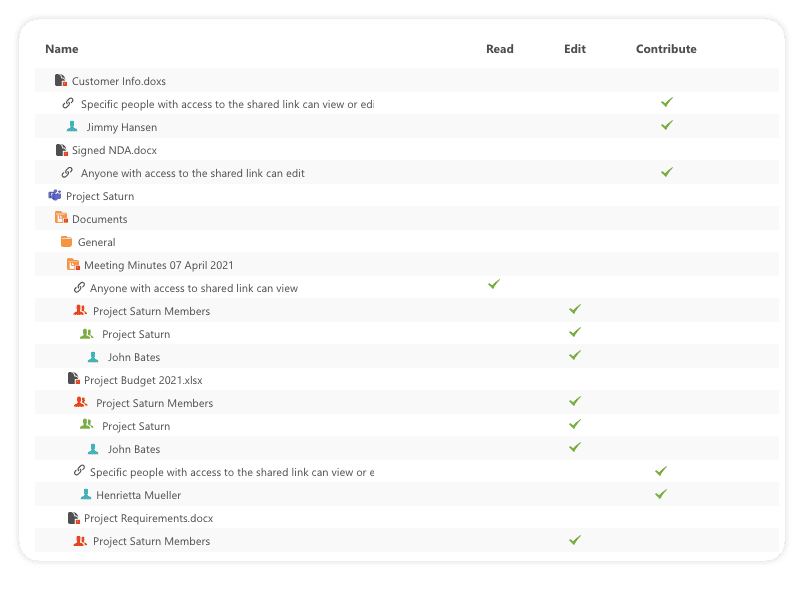
Owners can now see who has access to which document, site, or team. To find users and groups who have access to sensitive information has now become possible. Downloading of private files is also reported to owners. A permission matrix allows easy granting and removal of access to users.
4. External sharing
External sharing, if not controlled, can cause a major security breach. Syskit Point empowers the admins to take control:
- Find if files were shared with anonymous users and guest users from different departments or outside the company.
- Review all sharing settings on a tenant level and check where the sharing is enabled, which type of sharing is enabled (anonymous or authenticated).
- Detect if your users have been sharing content from their OneDrive with external users.
- Stop all file sharing when a user leaves the company, or in case a security breach is detected.
5. M365 Audit activities
With Syskit Point, every user and admin action can be tracked right down to the file level. Some tracked user actions include:
- Deleted, downloaded, or modified files
- Performed search queries
- Shared files
Tracked admin actions include:
- Deleted, renamed, and created sites
- Changed administrators
- Modified organization-wide settings
Conclusion
While it is obvious that shadow IT is not going away, IT teams need to develop a governance framework to minimize the risks of any kind of security breach.
Cloud services provided in M365 keep employees connected even when working remotely. To make the life of IT teams easier, Syskit Point runs on top of the M365 environment and extends the environment with exciting features that include easy access management, real-time alerting, enhanced security, proper governance, online reporting, external sharing, and auditing.


