What’s new – 2025.5.113
Published: October 15, 2025
Welcome to Syskit Point 2025.5.113! Syskit Point’s latest update introduces Workspace Review, next-generation, enterprise-scale governance for Microsoft 365, combining powerful admin control with a guided, user-friendly review process for workspace owners. It goes beyond traditional Access Reviews by including privacy, sensitivity, and compliance checks – ensuring secure, clutter-free, and AI-ready environments. With improved automation, actionable insights, and recommendation-driven tasks, organizations can confidently protect data, boost review completion rates, and demonstrate measurable compliance impact.
Not yet a customer? Try Syskit Point for free.
View the detailsAccess Reviews Evolution: Introducing Workspace Reviews 2025.5.113
For years, our automated Access Review has been a cornerstone of secure M365 environments, and it just got a major revamp! Managing workspaces is getting harder every day, oversharing, sprawl, and compliance requirements make it tricky to keep environments protected and ready for AI.
The new workspace review delivers next-generation enterprise-ready protection at scale – giving admins the control, flexibility, and insights they need, while providing workspace owners with a simple, guided process that drives significantly higher review completion rates.
With controlled delegation, improved user experience, and powerful governance tools, you can secure sensitive data, manage access with confidence, and meet compliance requirements across Microsoft 365. Prepare for an upcoming challenge – ensuring AI readiness through protected, discoverable, and clutter-free data and workspaces.
Workspace Reviews – How it works
1. Workspace Review Setup – Flexible and Easy to Configure
Simplify workspace reviews with flexible policies. Admins can set the rules once, choose what to track, and let reviews run automatically. You can choose between pre-built templates (Membership only, External sharing, Full review) or start from scratch.
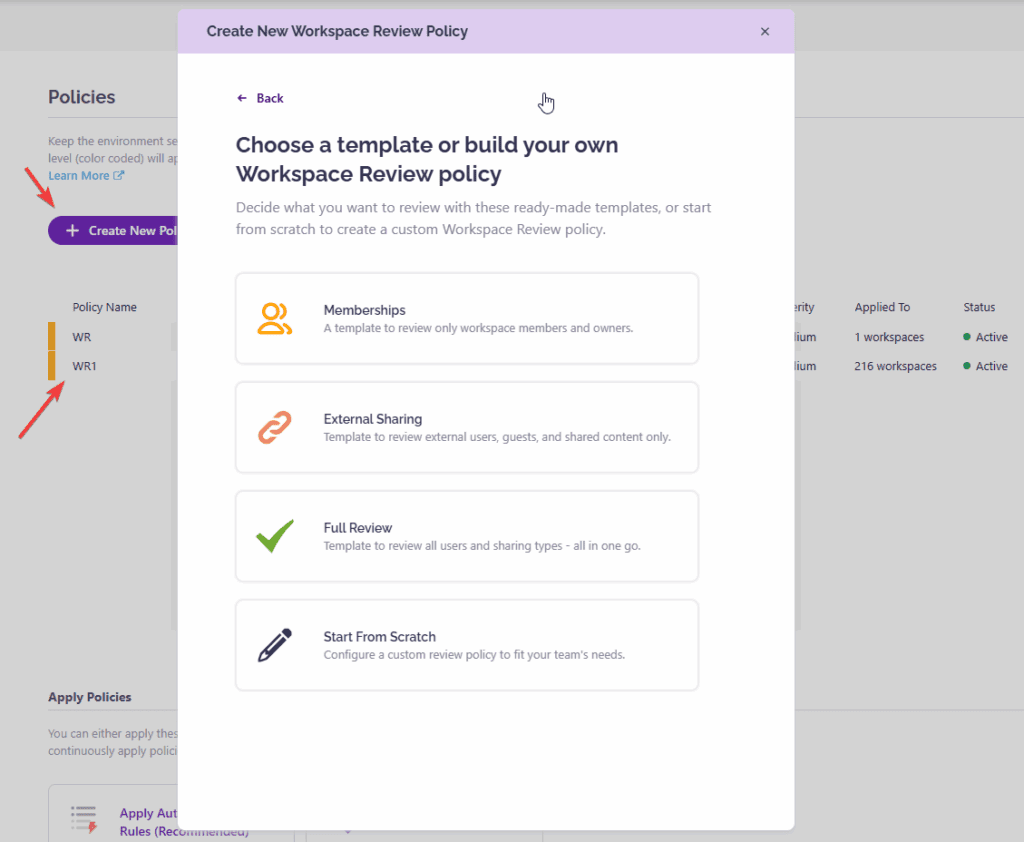
With full control over timing and frequency, teams save time and stay focused on the work that matters most.
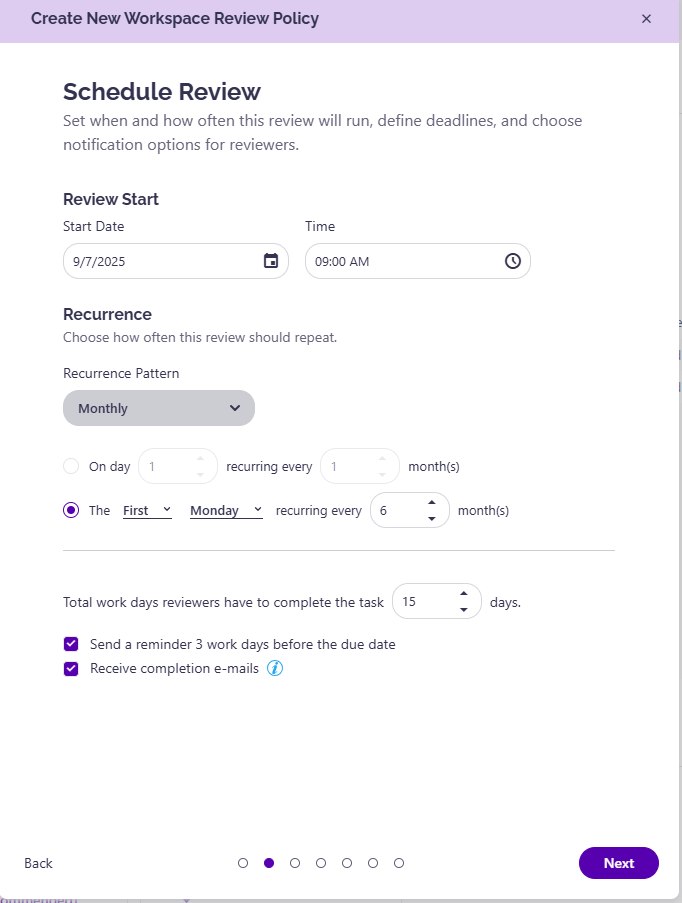
2. Owners Receive a Task and Start the Review – Enhanced Usability and Guided Experience
Owners receive an email and a task inside Syskit Point – no searching, no confusion.
Workspace Review now includes step-by-step guidance, real-time updates, tooltips, and simplified language, significantly improving usability and increasing completion rates.
- Instant feedback – see updates right after performed actions such as removing links or adjusting permissions.
- Clarity in progress – indicators show when access removals are still processing, reducing uncertainty.
- Built-in guidance – summaries and tips explain actions and their impact before each step.
- Team collaboration – start a Teams chat with co-reviewers directly from the task.
This streamlined flow reduces friction, saves time, and keeps work moving.
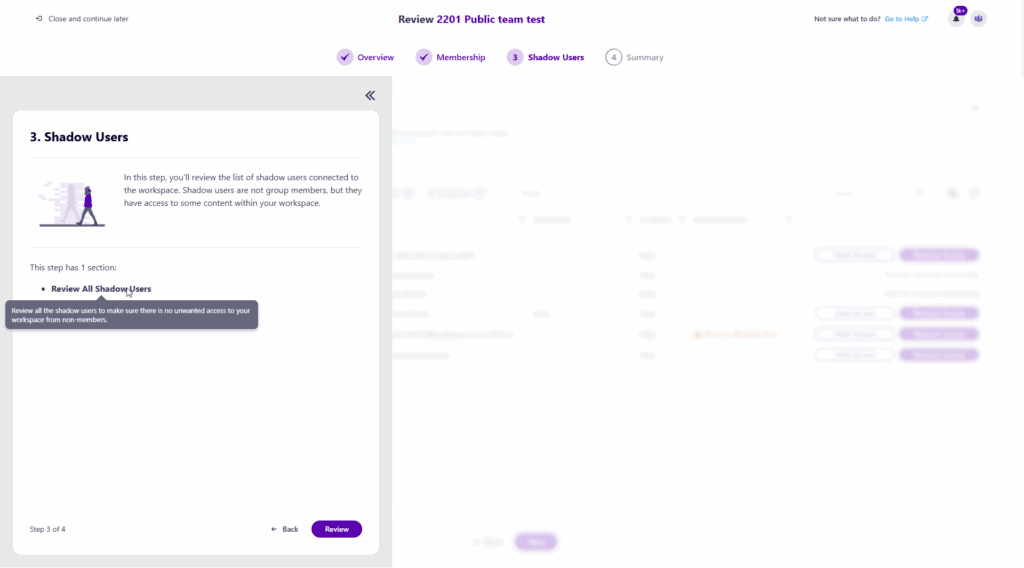
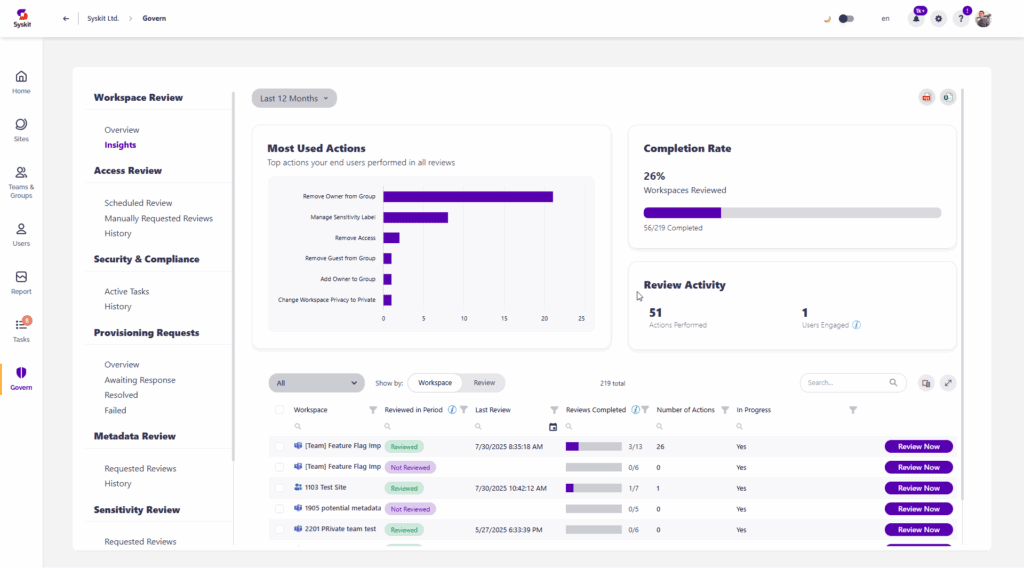
3. Workspace Review Insights – Monitor Progress and Demonstrate Impact
Workspace Review captures what actions were performed during reviews and provides metrics and reports with most used actions, helping IT teams measure impact.
Actions are more detailed than in Access Review and include information about what exactly has been performed. (e.g., if a guest user was removed, which type of sharing link was removed (anyone, company-wide, etc.)). This will help with demonstrating ROI to your stakeholders and measuring success.
Workspace Review – Beyond Checking Access
While Access Review is focused only on checking who has access to what, Workspace Review also includes privacy review, sensitivity review, and resolving other policy violations such as:
- Inactive workspace – if a workspace is inactive, owners will have the option to archive/delete the workspace, and if they decide to do so, the workspace review task will automatically be completed
- Ensuring compliance with the Minimum/maximum number of owners policy – if there are not enough/too many owners on the workspace, owner(s) must be added/removed to resolve the policy violation
- Sensitivity review – if the workspace sensitivity label doesn’t match its content or usage, ask owners to confirm or update the sensitivity label to ensure proper classification and protection
- Privacy review – if the workspace privacy setting is not aligned with company policy (for example, it is public when it should be private), ask your owners to adjust the privacy setting
Recommendation-Driven Governance – Automated Maintenance
Workspace owners receive recommendation-driven tasks, making it easier to take appropriate actions. A common challenge with Access Reviews has been uncertainty around what actions to take. By providing clear, actionable insights, Workspace Review empowers owners with greater confidence, leading to higher engagement, more completed actions, and measurable ROI for administrators.
We will provide recommendations for removing blocked members once detected, removing inactive guests, expired or unused sharing links and more.
You’ve trusted us to secure your M365 environment. Now, let us show you the future of workspace governance. Activate Workspace Review and take your security and compliance to the next level.
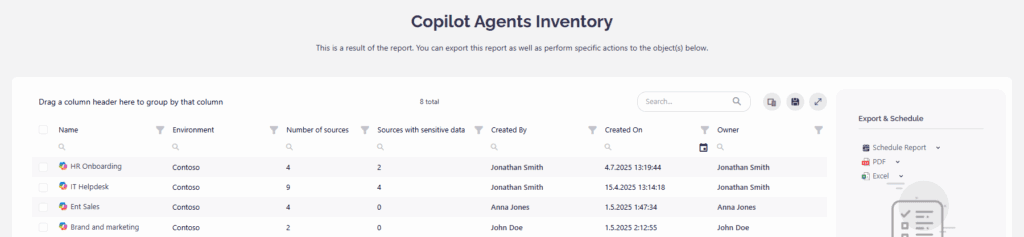
Consolidated Copilot Agent Inventory for Risk Detection 2025.3.101
AI in Microsoft 365 brings many benefits to users across organizations, helping them with creativity, productivity, and completing tasks now with the help of Agents, who act like intelligent assistants. Considering that they integrate with your Microsoft 365 data to provide faster access to information, combine multiple sources of data, or perform actions on behalf of end-users, SharePoint and Copilot agents are creating new security blind spots in M365 tenants, making it one of the top concerns for IT teams recently.
Organizations are adopting Copilot Studio agents, experimenting with use cases, and deploying agents to streamline internal workflows. But what starts as experimentation quickly turns into an inventory no one is watching, leading to uncontrolled sprawl. However, agents are constantly accessing data and can potentially expose sensitive content.
We are rolling out a new capability that allows you to stay aware of a consolidated Copilot agent’s inventory report. It will list all agents in selected environments, see ownership, and detect agents with too many knowledge sources or those using sources with sensitive data, both of which might be risky. Keep the data safe and agents under control.
Please note: This report is in the early access phase and not visible by default, so if you want to try it, contact us and share feedback. It will mean a lot.