Access reviews best practices
Designing effective access governance in Microsoft 365 requires more than running periodic reviews; it demands a consistent set of practices that keep ownership, classification, and membership healthy over time.
Here are the access reviews best practices we believe you should follow to achieve effective governance for your Microsoft 365 workspaces:
1. Workspace owners
Ownership is the cornerstone of governance. Every workspace should have at least two owners, which is considered the gold standard.
Two owners ensure continuity if one is unavailable due to sick leave, vacation, or departure. More than five owners, however, creates a diffusion of responsibility where no one feels accountable.
Regular reviews should be conducted to ensure each workspace has the prescribed number of owners.
2. Ownerless workspaces
Ownerless workspaces — unfortunately common in many tenants — are a governance nightmare. With no responsible party, there is no one to certify access, update sensitivity labels, or respond to incidents. Regular reviews must therefore begin with validating that ownership is correct and balanced.
3. Sensitivity classification
Sensitivity Labels are an essential component of Access Reviews. A workspace titled “Marketing Team” gives no clue about the sensitivity of its content. Applying a label like “Confidential” or “Highly Confidential” immediately communicates expectations and activates built-in protections such as information rights management (IRM), external sharing restrictions, and policy-based alerts.
During reviews, owners must confirm that labels are correctly applied and still appropriate. A workspace might have started as a general collaboration area but over time accumulated sensitive customer data. Reviews ensure that labels evolve with content, preventing mismatches where confidential documents sit unprotected in general-purpose sites.
4. Team members
Membership lists are dynamic and constantly at risk of becoming outdated. People leave the organization, change departments, or rotate roles. External contractors roll off projects.
Without regular validation, these accounts remain, creating unnecessary exposure.
Access Reviews are the opportunity for owners to tidy membership lists: remove stale accounts, add new hires, and certify that every member still requires access. This practice not only reduces risk but also streamlines collaboration by ensuring workspaces are populated only with relevant participants.
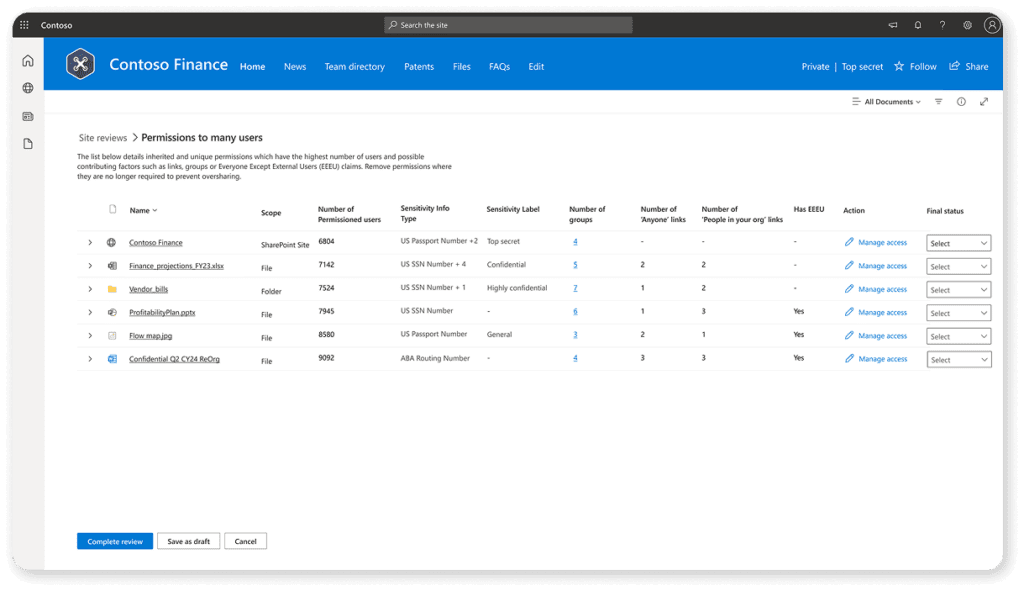
5. Shadow users
SharePoint and Teams allow file and folder sharing outside of formal team membership. These link-based permissions create ‘shadow users’ — individuals who have access but do not appear in the workspace’s member list.
To make matters worse, Microsoft’s sharing defaults have changed repeatedly over the years, leaving behind a patchwork of legacy links with unpredictable access scopes.
Access Reviews must specifically check for these links, revoke obsolete ones, and convert valid external collaborators into formal members where possible. Ignoring shadow users creates blind spots where sensitive content may be accessible without IT’s knowledge.
6. External users
Externals represent the highest risk category. Guest accounts should always be time-limited and tied to specific business needs. Reviews must confirm that every external still has a valid justification for access.
Best practice dictates applying expiration dates, requiring business justification, and re-approving access regularly. An external user lingering in the tenant long after their engagement ended is one of the most common and preventable data leak scenarios.