Securing and governing Microsoft Copilot with Syskit Point
Table of contents
As organizations begin using Microsoft Copilot, it becomes even more important to secure and govern your Microsoft 365 environment and prepare for Copilot. Copilot promises to enhance collaboration and productivity, but to harness its full potential while safeguarding sensitive data, IT teams must adopt proactive measures and implement effective governance strategies as Microsoft Copilot will expose your already existing security risks.
Our Syskit team recently held a webinar on security challenges associated with governing Microsoft Copilot and offered practical strategies for mitigating risks and enhancing security and governance. Our insights were drawn from extensive research, industry expertise, and practical experience, offering valuable guidance for IT teams and decision-makers alike.
Watch the entire webinar recording below or read our blog for some key highlights and takeaways on how to leverage Microsoft Copilot effectively while maintaining robust security measures.
Understanding Microsoft Copilot: A Game-Changing Innovation
In their study from March of 2023 Salesforce asked 500 senior leaders what their feelings about generative AI are. 57% of them feel that this is going to be a game-changer and 33% thought it was over-hyped. But even among the sceptics 80% agree that generative AI will help them better serve their customers.
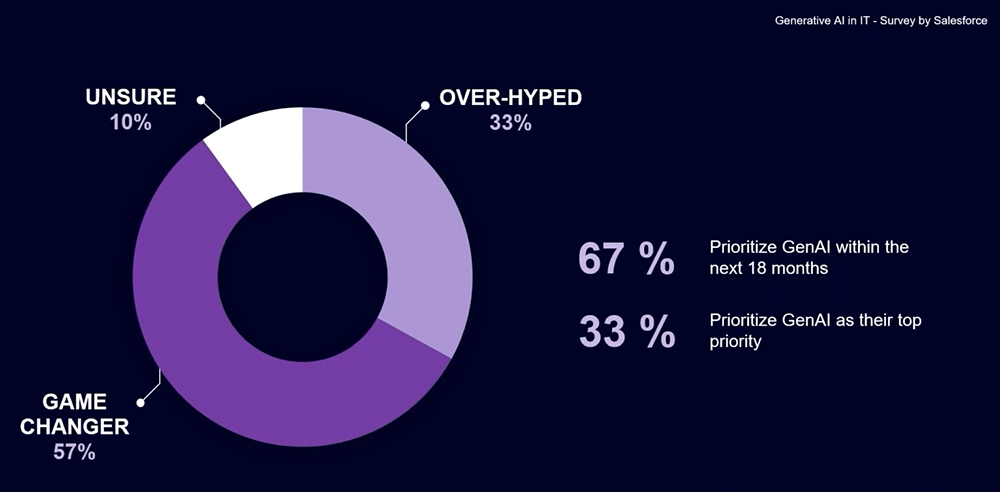
When it comes to security risks, 71% of those senior IT leaders also believe that generative AI will introduce new security risks.
This is a very valid concern but to shine some light on that let’s look at how Copilot actually works.
How Microsoft Copilot works
At the core of Copilot’s functionality there is a semantic index, Microsoft Graph, and the LLM.
The process of data flow in Copilot begins when a user enters a command into an application like Word or PowerPoint. Initially, Copilot enhances the input by adding context and relevant content through a method known as grounding. This process utilizes information from Microsoft Graph, to make the responses more pertinent and useful for the user’s specific needs. It’s important to note that Copilot for Microsoft 365 only accesses data that users have permission to view.
Next, the enhanced prompt is encrypted and sent to the LLM, which operates within the Microsoft 365 Service Boundary but outside your tenant boundary. Once received the LLM processes the prompt, generating a response.
Following LLM processing, Copilot further refines the response through additional grounding with Microsoft Graph, along with conducting checks for responsible AI use, security, compliance, and privacy.
Finally, the processed and vetted response is relayed back to the application for the user’s review, ensuring it aligns with organizational policies and provides accurate, actionable information.
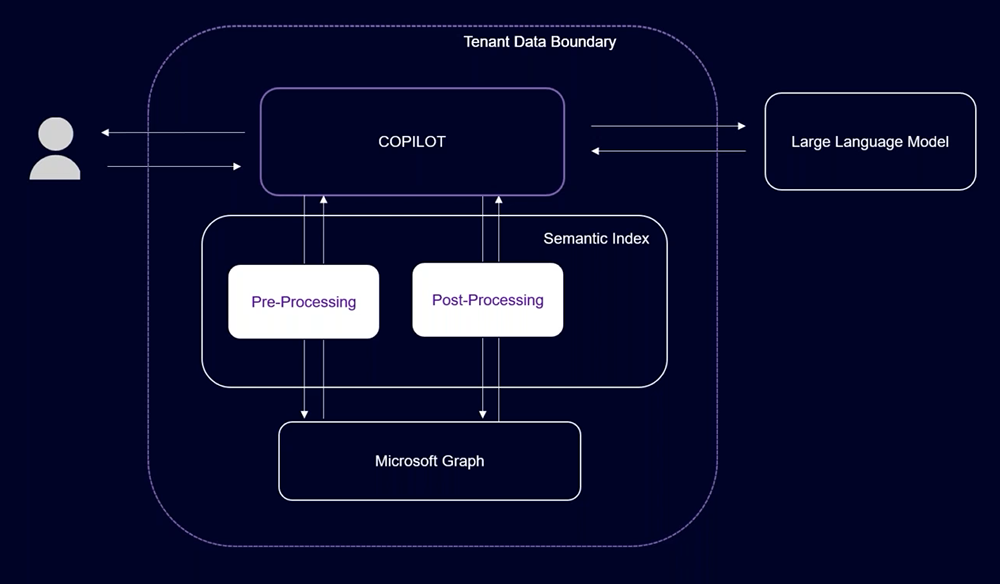
The key things to remember here are that there are 2 boundaries – Tenant boundary and Microsoft 365 service boundary so the LLMs do not have direct access to our data nor will it be trained on your data but it is going to receive some of your data to generate a better response. That said, if you make requests from inside the European region, only the LLMs inside of the European region will process that request.
So going back to the concern that Copilot will introduce new security risks, it will not, but it will expose and amplify all your existing security risks.
Addressing Security Challenges: Practical Solutions
Below are some practical solutions for addressing Copilot security challenges. We also created a blog post on Copilot best practices based on recommendations from Microsoft.
Change Sharing Links Defaults
By default, encourage users to utilize specific sharing settings to enhance data privacy and security. Evaluate and update existing sharing links to align with organizational policies. Regularly evaluate sharing settings and remove unnecessary access to minimize data exposure.
Review Public Teams and Group Access
Regularly audit public Teams and review permissions granted via large groups. For example, Everyone or Everyone except external users and ensure that sensitive information is restricted to authorized personnel only.
Implement Regular Access Reviews
Leverage Microsoft Entra to conduct periodic access reviews, focusing on shadow users and inactive accounts. Engage group owners in the review process to enhance accountability and efficiency. Recurring access reviews ensure that user permissions remain aligned with organizational needs and policies.
Establish Lifecycle Management Reviews
Monitor the lifecycle of Microsoft Groups and review content relevance regularly. Identify and archive outdated or redundant data to maintain data integrity and relevance. Automate the management of inactive workspaces to reduce clutter and ensure data cleanliness within Microsoft 365 environments. This is the part of garbage in, garbage out. You need to make sure that your content is relevant on your sites because Microsoft Copilot is going to pull everything from everywhere and it cannot differentiate what’s relevant and what isn’t.
Utilize Sensitivity Labels
Deploy sensitivity labels to enforce granular access controls and encryption. Sensitivity labels classify and protect sensitive data, ensuring that access is restricted based on predefined security policies.
If you set up sensitivity labels in such a way that only a subset of people can decrypt the files that are protected, Microsoft Copilot is going to respect that on top of all the other security measures that you have on those files. This is one of the better ways to make sure that those sensitive files are encrypted and not available company-wide.
Perform User Permission Audits
Conduct audits of user permissions and align them with organizational roles and responsibilities. Mitigate unauthorized access by ensuring that users have appropriate permissions.
Understanding the Role of Third-party Solutions
While Microsoft provides native controls for managing security within Microsoft 365, there are gaps that third-party solutions can effectively address. Syskit Point can bridge these gaps, offering enhanced control and visibility when securing and governing Microsoft Copilot. By leveraging Syskit Point alongside native controls, organizations can better prepare for Copilot deployment and mitigate security risks effectively.
In discussions with customers, we’ve identified three key challenges that IT teams must address to ensure a secure and seamless Copilot implementation:
Minimizing Oversharing: Remember Microsoft Copilot will only expose existing security risks, so the main issue that we see here is that organizations already have oversharing challenges which they might not be aware of. Because of its ease of use, Copilot is going to expose those oversharing issues to your users.
Evaluating and controlling sharing settings, including default sharing configurations and sensitivity labels, is essential to prevent oversharing in the future but you’ll need to address the existing challenges as well.
Syskit Point simplifies the Copilot rollout process by providing comprehensive reports on sharing links, group access and user access allowing for quick evaluation and removal of unwanted access.
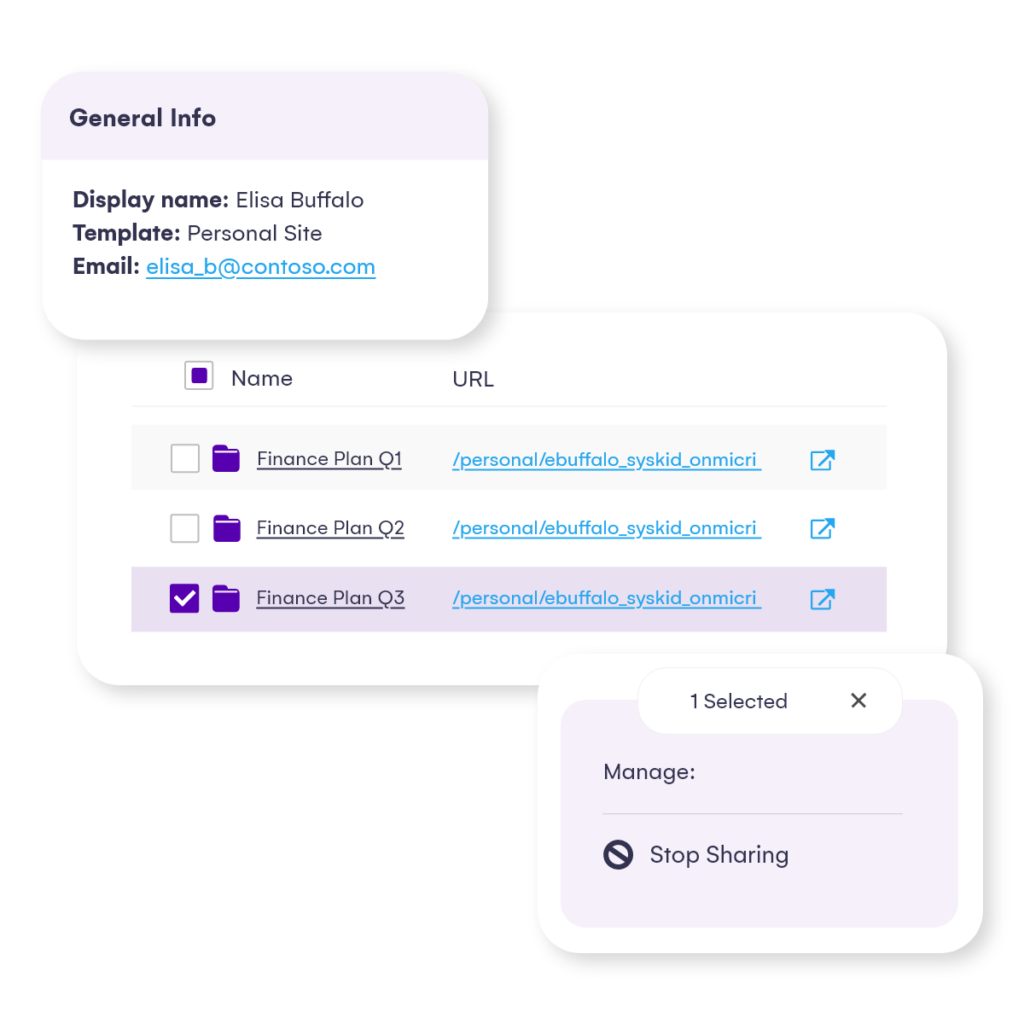
Establishing Access Reviews and Lifecycle Management: Once you have gone through the trouble of minimizing existing oversharing on your tenant, you need to ensure that it stays clean.
Setting up regular access reviews ensures that every workspace has been checked for potential oversharing regularly and with lifecycle management you can minimize stale content on your tenant which Microsoft Copilot can use and mislead your end users by confidently providing this stale information it has access to.
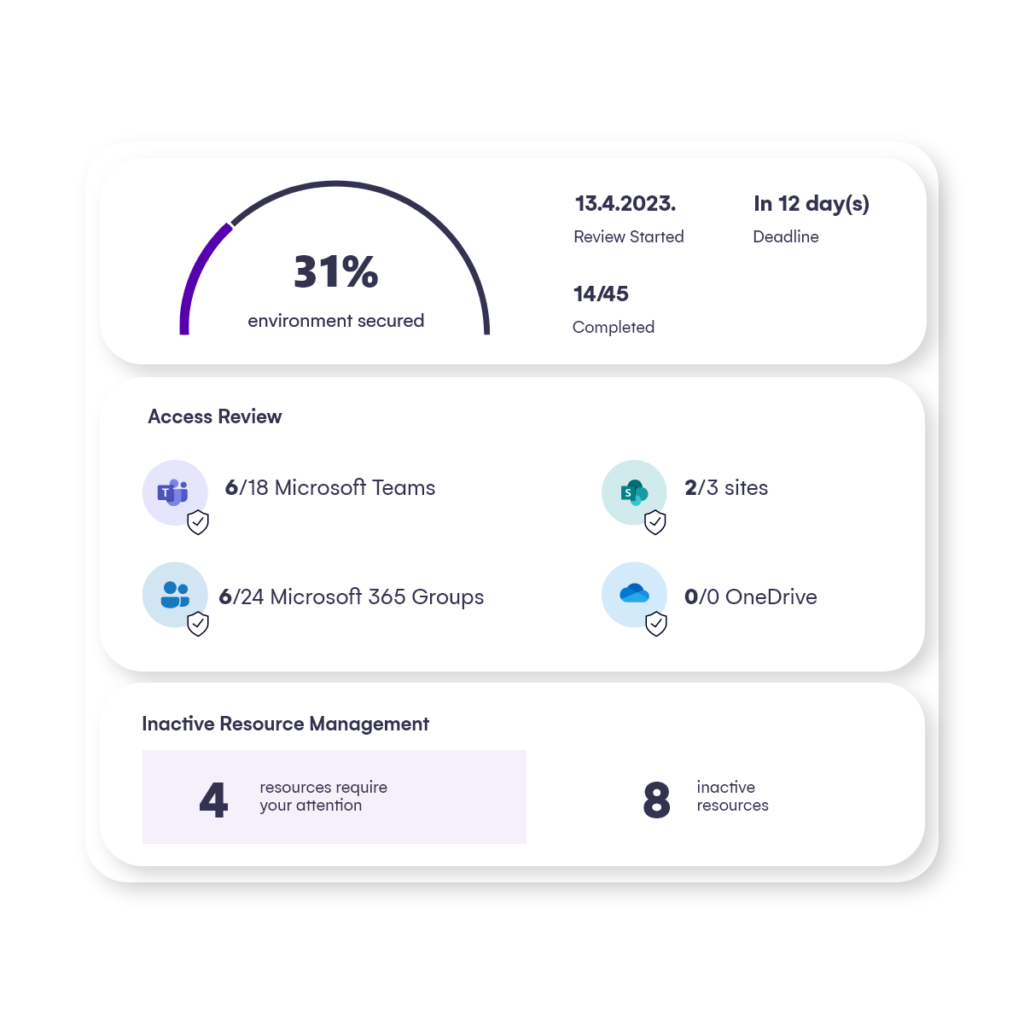
Enhancing Visibility and Control: IT teams often struggle to maintain visibility and control over user permissions and group access. With Syskit Point’s user access reports, IT teams as well as line managers can quickly identify and manage user permissions, ensuring that users have access only to what they should have access to before applying a Copilot licence.
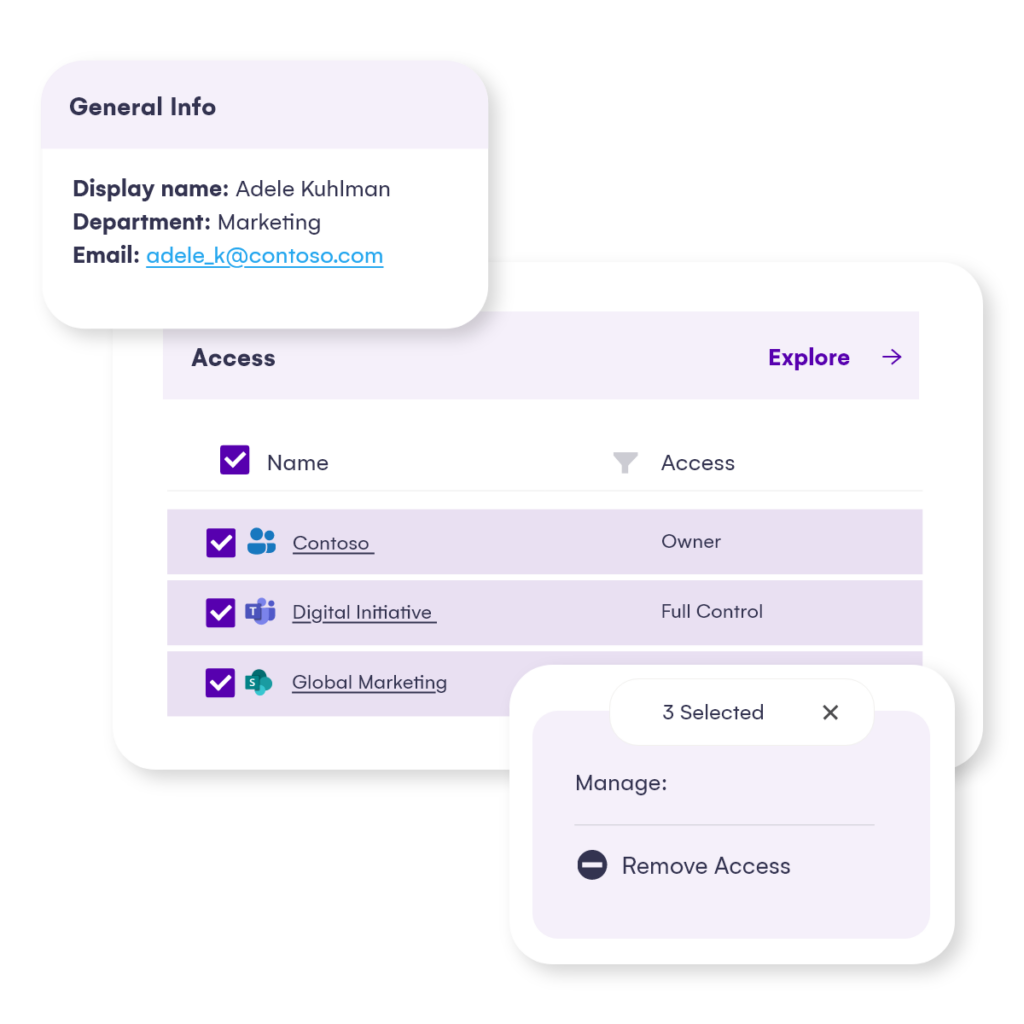
Governing Microsoft Copilot
If we take a step back, these Copilot challenges are actually governance challenges with governing your entire Microsoft 365 environment.
Governance was always meant to be a team game, and never once did we talk to someone in IT who didn’t want to mitigate all of the potential risks that they have on their tenants. IT teams and security teams were struggling to properly implement these governance procedures because there wasn’t much support from the wider organization.
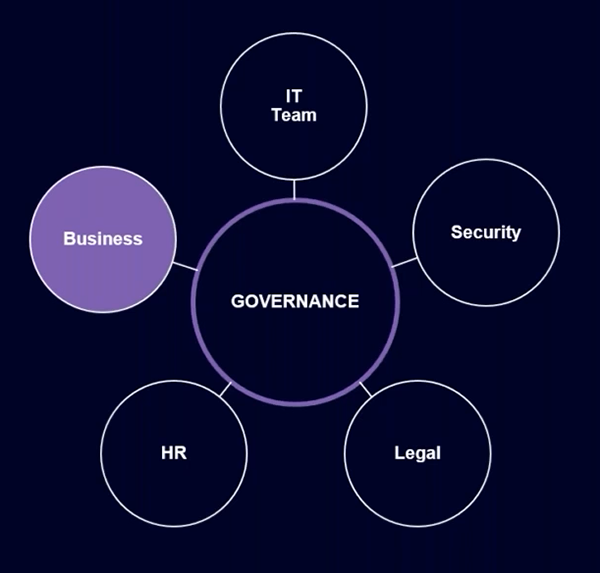
End users now have that big motivation and that is an opportunity that we should all take to start implementing governance properly because it is there to help end users utilize Copilot more efficiently. We can secure our tenants in the way they should have been secured from the start.
There is going to be a lot of work that you need to do to prepare and maintain your Microsoft 365 environments.
Conclusion
As organizations prepare for Copilot deployment, it’s essential to first focus on quick wins and establish foundational governance processes. By leveraging the right tools and implementing proactive measures, IT teams can minimize security risks, streamline collaboration, and maximize the benefits of Microsoft Copilot within their Microsoft 365 environments.
By adopting proactive measures, leveraging third-party solutions such as Syskit Point, and implementing comprehensive governance strategies, organizations can confidently embrace Copilot while safeguarding their data and enhancing productivity.
Having the right tools to help you succeed with Copilot is the key. We’ve seen that Microsoft native controls have some gaps and we should utilize all of the help we can get. Syskit Point is here to help you in securing and governing Microsoft Copilot in a much more controlled way.


