Why and how to use Microsoft 365 sensitivity labels for data protection
Table of contents
Sensitivity labels help you protect and classify your Microsoft 365 groups, SharePoint sites, Teams, and other workspaces in your Microsoft 365 tenant. They play a very important role in data security by preventing unauthorized access and reducing the risk of data leaks. At the same time, they help organizations stay compliant with legal and regulatory requirements by consistently enforcing protection policies.
Think of them as digital security tags you can stick on workspaces and M365 assets, such as files and emails. These tags tell the system, “Hey, this is top secret!” or “This is just internal info.” Based on the label, Microsoft 365 automatically applies protections, like encryption, restricting who can see the file, or even blocking it from being shared outside your company.
They can also go deeper and help you protect data and information not only in the mentioned containers but also in other assets in M365, Microsoft Fabric, and Microsoft Azure, such as meetings, Power BI reports, Loop, and more.
In this blog, we will cover the basics of sensitivity labels, how to apply them, which Microsoft license you need, and how to automate the policies.
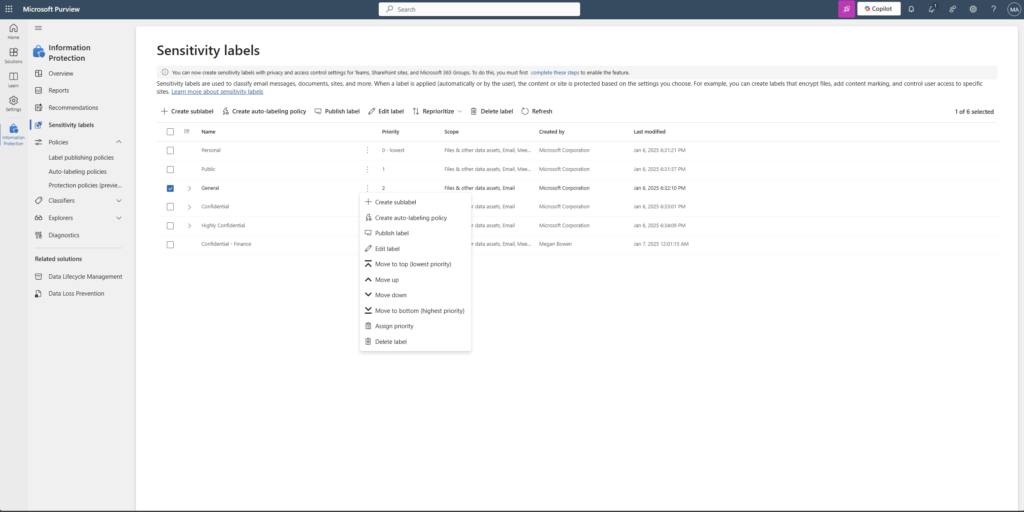
How sensitivity labels protect sensitive data in M365
When you apply a sensitivity label, you classify data and enable proactive protection settings and actions. There are multiple levels of protection available when we apply sensitivity labels, but today, we’ll discuss two basic levels: workspace (container) level and files level.
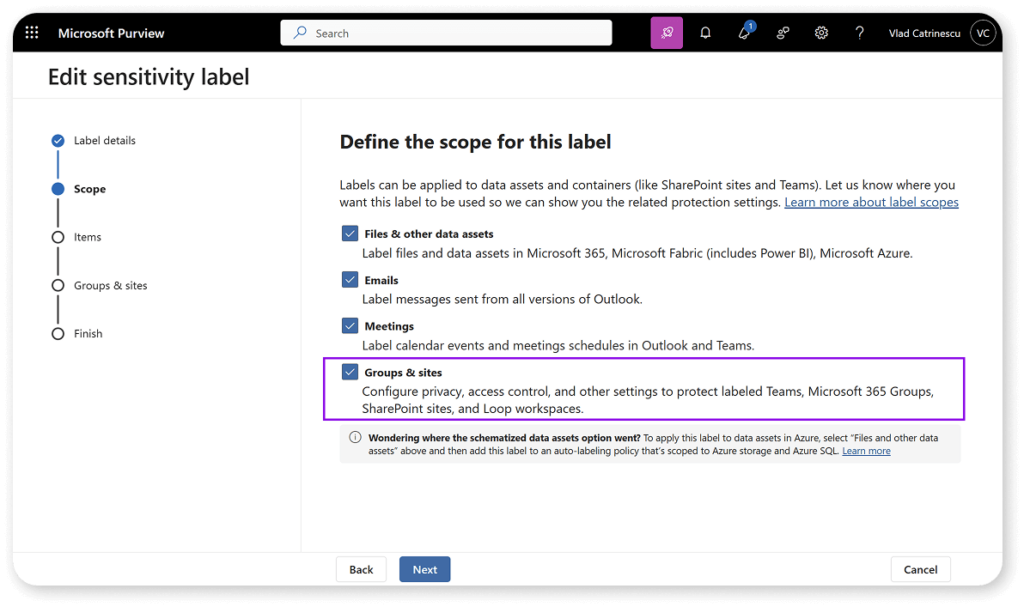
The workspace/container level provides you with:
- Ability to control the level of access that internal and external users will have to label teams and Microsoft 365 Groups (Predefine privacy and external user access),
- Capability to control external sharing and configure Conditional Access settings (access from unmanaged devices),
- Option to decide whether private teams will be discoverable in searches and control the types of teams that can be invited to shared channels (Control private teams’ discoverability and shared channel settings),
- A default sharing link for sites and sites sharing settings (via Power-shell configuration only).
The files/meetings/emails level provides you with:
- Capability to restrict access to authorized users to control who can access and view labeled items (predefine allows users and groups, define expiration dates for authorized users),
- Ability to add custom headers and footers,
- Setting for auto-labeling files and emails based on specified conditions and rules,
- Ability to protect meetings and chat by labeling (and optionally encrypting) meeting invites and any responses and enforce Teams-specific options for the meeting and chat.
Why is it important to label your workspaces?
Think of your M365 workspaces like different rooms in a giant office building. Some rooms are open for everyone, like a breakroom, while others, like HR or Finance, should only be accessible to certain people. If you don’t label these spaces properly, you risk accidental data exposure, where sensitive files end up in places they shouldn’t be.
For example, imagine you create a Microsoft Team to discuss an upcoming company acquisition. If that Team isn’t labeled and restricted properly, an intern or someone from another department could accidentally stumble upon confidential discussions. Worse, external guests could be added without anyone realizing the risk.
Sensitivity labels can help you to:
- Identify and classify sensitive data across your organization so you can build M365 governance policies on top of it,
- Protect your data from unauthorized copying, printing, or sharing (both internally and externally),
- Ensure that your data is handled and stored in compliance with your organization’s policies and regulations,
- Communicate the level of confidentiality and sensitivity of your data to your users and collaborators so they understand better how to handle it,
- Reduce the risk of data breaches, leaks, or losses by protecting your workspaces and data, preventing unauthorized access, and ensuring the information remains secure.
What Microsoft license do I need to start using sensitivity labels?
Sensitivity labels are part of the Microsoft Purview Information Protection solution. For manual sensitivity labeling, the following licenses provide user permissions:
- Microsoft 365 E5/A5/G5/E3/A3/G3/F1/F3/Business Premium/OneDrive for Business (Plan 2)
- Enterprise Mobility + Security E3/E5
- Office 365 E5/A5/E3/A3
- AIP Plan 1
- AIP Plan 2
Please note that Microsoft 365 Apps require user-based subscription licensing for users to use sensitivity labels with Office clients. Device-based licensing isn't supported.
Can sensitivity labels be applied automatically?
Yes, labels can be manually applied by users or automatically applied based on content (keywords, sensitive info types, AI-based classifiers).
To do so, you will need a Microsoft E5 license, Office 365 E5 license, or Enterprise Mobility and Security E5 offering.
How to create and configure sensitivity labels in Microsoft 365?
Sensitivity labels best practices
Before diving deep into the Purview admin center and starting to create and publish sensitivity labels, here are the most important best practices to get you started:
- When you decide to start with sensitivity labels, consider the following aspects of your M365 workspace governance:
- Privacy of the workspace
- Sharing outside the group – internal sharing and collaboration
- Sharing outside the company – how you work with external collaborators
- Potential governance policies you wish to enforce now or in the future based on this classification, for example, Access Reviews
- Use a limited number of labels, 3-5 per scope, so end users don’t get frustrated and confused with too many options.
- Use short and concise label names to avoid confusion, misclassification, and poor user adoption, e.g., Label for confidential data that is for internal usage only:
- Bad: Confidential 1 and Confidential 2
- Good: Confidential – Internal Employees Only, Confidential – External Collaboration
- Educate your users and create detailed knowledge on your intranet for users to fall back on and explore at their own pace
No size-fits-all sensitivity label strategy
Keep in mind that there is no one-size-fits-all strategy when it comes to data classification and sensitivity labels. You need to consider your organization’s specifics, the standards and regulations associated with data management in your industry, your business-critical data, whether you are using multiple solutions to label your data, etc.
It can get overwhelming, but the most important thing is to start. Start small, but start. Microsoft MVP Drew Madelung suggests using a crawl-walk-run method for sensitivity and retention labels. He advises spending more time defining and understanding what these labels need to be rather than hurrying and correcting mistakes.
Real-world examples of data classification
Here is an example of how you can define your labels following these guidelines:
|
Label |
Description (Usage) |
Private Team |
Sharing to Non-Members |
Sharing to External Users |
Access Review Cadence |
|---|---|---|---|---|---|
|
Highly Confidential
|
Content is visible only to members of the container/team; files cannot be shared externally or beyond members.
|
Yes
|
No
|
No
|
30 days
|
|
|
|||||
|
\ Confidential (Internal)
|
Internal Sharing: Content visible to members of the container/team, with the ability to invite other company employees and share files internally.
|
Yes
|
Yes
|
No
|
90 days
|
|
|
|||||
|
\ Confidential (External)
|
Internal and External Sharing: Marked sensitive, but files can be shared with both internal and external users.
|
Yes
|
Yes
|
Yes
|
90 days
|
|
|
|||||
|
General Access
|
No restrictions on content sharing.
|
No
|
Yes
|
Yes
|
180 days
|
Once you’ve decided on the number of labels and taxonomy, follow this step-by-step guide from Microsoft to create and configure labels.
How can Syskit Point help you with sensitivity labels
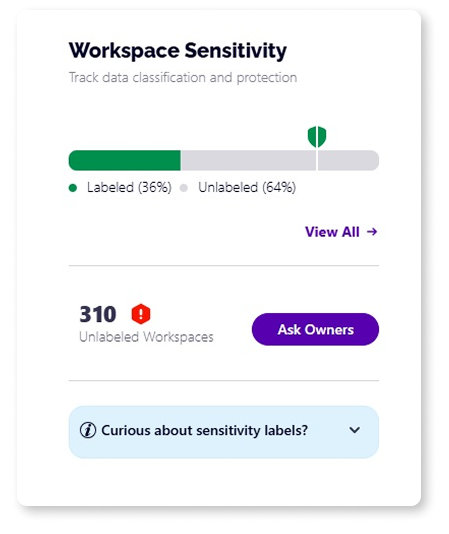
Visibility and monitoring of sensitive workspaces
Using a centralized dashboard, track the number of your workspaces that have been labeled. Drill deeper to get complete visibility into which sensitivity label has been applied to what workspace and which M365 workspaces are still unprotected.
Ask workspace owners to assign the sensitivity label
For all workspaces that have not been assigned a sensitivity label, send a task to the workspace owner to add the appropriate label. The same task can be sent to workspace owners to review whether the applied label is still valid or should be changed to reflect the latest workspace requirements.
Automated governance policies based on workspace sensitivity label
Syskit Point comes with a powerful rules engine that allows you to automate your governance policies based on sensitivity labels, along with other custom properties.
Using sensitivity label as a condition, you can define which governance policies apply to which workspace, regardless of when and how a particular workspace has been created. This includes:
- Ownership policies (minimum number of owners and maximum number of owners),
- Storage optimization (versioning setup),
- Access reviews,
- Orphaned workspaces cleanup,
- Access requests,
- Inactive workspace cleanup.
Syskit Point will continuously crawl for all sites, teams, and groups in your M365 with a particular sensitivity label applied to ensure that the specific governance policies you chose are applied throughout the workspace lifecycle.
For example, you can define that all workspaces classified as Highly confidential should have a minimum of 3 owners and regular access reviews every 3 months. Syskit Point will enforce the policies and ask owners to comply with defined procedures.
Sensitivity labels more important than ever – AI era challenges
You’re probably already using generative AI in your company. AI tools, like chatbots or automation systems, can accidentally access or share confidential information if they’re not properly restricted. For example, imagine an employee pastes confidential customer data into an AI-powered chatbot for help with an email response. If that chatbot isn’t secure, the data could be stored, used to train future AI models, or even exposed to unauthorized users. That’s a huge privacy and compliance risk.
Another risk is AI-driven automation gone wrong. Let’s say your AI system generates reports based on company data. If it accidentally pulls sensitive financial details into a public report, that could lead to a data breach or even legal trouble.
Sensitivity labels offer a simple way to proactively protect data by applying security measures such as content encryption and access restrictions, preventing external sharing, applying watermarks, and preventing copying or downloading of most sensitive files.

Ensuring compliance and security with a strong labeling strategy
In conclusion, sensitivity labels play a crucial role in protecting and managing data within Microsoft 365. They help classify and secure information based on its sensitivity, ensuring that sensitive data is properly labeled and protected throughout its lifecycle. By implementing sensitivity labels, organizations can enhance their data governance, comply with regulatory requirements, and mitigate risks associated with data breaches and unauthorized access.
The integration of sensitivity labels with tools like Microsoft Purview and the ability to automate labeling processes further streamline data protection efforts. Adopting a comprehensive labeling strategy is essential for maintaining data hygiene, supporting AI initiatives, and ensuring overall data security and compliance.
Learn more about sensitivity labels
What are sensitivity labels What are sensitivity labels and retention policies in Microsoft 365 Office 365 sensitivity labels Sensitivity labels best practicesIf you want to learn more about data classification, retention, and sensitivity labels, make sure to watch our webinar, which dives deep into Microsoft Purview and labeling strategies.

