Sensitivity labels best practices
Table of contents
Before exploring the Microsoft sensitivity labels best practices and recommendations, it is very important to explain what they are. Sensitivity labels are like unique tags for your important documents and emails. They help you protect your information by telling people how sensitive it is.
For example, you could have a label for “Top Secret” information or “Internal Use Only” that helps you identify and classify your enterprise data.
When you put a label on your data, it can do different things to keep it safe, such as:
- Hiding sensitive information: It might blur out parts of the document.
- Locking it up: Only people with the correct key can open it.
- Adding a warning: It might put a big sign on the document saying it’s confidential.
Think of sensitivity labels as a special lock on a treasure chest. You’re the one who decides who gets the key!
In a complex organization, it’s surprisingly easy to accidentally grant staff members access to confidential information, such as SharePoint documents. This can put both the document’s creator and its contents at risk. When dealing with sensitive or protected information, applying the appropriate sensitivity label is like putting a protective shield around the file, ensuring it’s encrypted and allowing the owner to manage access for individuals or groups.
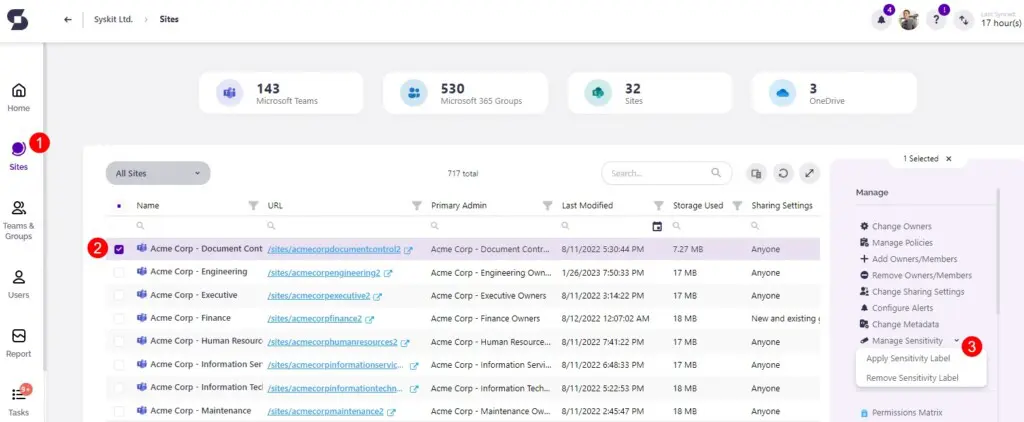
These labels act as gatekeepers, preventing unauthorized access and ensuring the information remains secure. For instance, if you need to share a document containing personal information like VAT or ID details with Vlad Catrinescu, for example, for processing, you can simply label it as confidential, restricting access to authorized personnel only.
If Vlad decides to delegate the task to an Administrative Officer, the officer would be unable to open the document without your approval, as they lack access. This process safeguards the security and integrity of the document and its stakeholders, preventing potentially harmful breaches.
What are the best practices for sensitivity labels in Microsoft 365?
We’ve collected and organized eight Microsoft sensitivity labels best practices to help you get the most out of this powerful tool. Here there are:
1. Classify information based on sensitivity
Talk to your business/security team and define clear categories. Create well-defined sensitivity labels such as Public, Internal, Confidential, or Highly Confidential, aligning with your organization’s data protection policies. Don’t go with Gokan’s essential documents. You can also tailor labels to your organization and customize labels to reflect the data your organization handles, such as financial, personal, or intellectual property.
2. Integrate sensitivity labels with Data Loss Prevention (DLP)
Integrate sensitivity labels with DLP policies to enforce rules that prevent data leakage, such as blocking the sharing of sensitive content with external parties. You can also use these labels to trigger specific DLP actions, like encrypting emails with highly confidential information or preventing uploading labeled files to unapproved cloud services.
3. Automate labeling where possible
I won’t dive into auto-labeling since it deserves a chapter of its own. Still, it’s worth noting that you can leverage auto-labeling capabilities to automatically apply labels based on content, such as keywords, patterns such as credit card numbers, or other types of sensitive information.
4. Apply encryption and permissions management
Set up labels to apply encryption, ensuring only authorized users can access or modify the content. Labels can also enforce specific restrictions, such as read-only access or preventing users from copying, printing, or forwarding sensitive information.
5. Monitor and review label usage
Conduct regular reviews of how sensitivity labels are applied and used to ensure alignment with organizational policies. Utilize the Microsoft 365 compliance center to monitor and generate reports on label usage and configure alerts for potential mislabeling or unauthorized access attempts.
6. Review, review, and review
Periodically review and refine labeling rules to ensure they accurately capture and label sensitive information. This helps prevent both over-application and missed key data.
- Accuracy: The nature of sensitive information and regulatory requirements can change over time. Regular reviews ensure that labels are up-to-date and accurately reflect the current state of data sensitivity.
- Compliance: Regulations and standards for data protection evolve. Regularly reviewing labeling rules helps ensure ongoing compliance with legal and industry requirements.
- Preventing over-labeling: Too many labels or overly broad labels can create confusion and reduce the effectiveness of data management strategies. Regular reviews help refine labels to be more precise.
- Preventing under-labeling: Critical sensitive information might be missed or improperly handled if labels are too restrictive or outdated. Periodic reviews help catch and correct these gaps.
- Adaptation to new threats: As new types of threats and vulnerabilities emerge, labeling rules may need to be adjusted to effectively address these changes. It is important to note to keep up to date with Compliance Standards as well, as they are always evolving.
Regular reviews ensure that labeling remains effective and aligned with organizational needs and regulatory expectations.
7. Integrate labels across all Microsoft 365 services
To maintain a unified protection strategy, consistently apply sensitivity labels across all Microsoft 365 services, including SharePoint, Teams, OneDrive, and Exchange. They ensure that the same sensitivity labels are applied uniformly across different platforms to create a cohesive and comprehensive protection framework. This standardization helps prevent security gaps and ensures that data protection policies are uniformly enforced.
Create, deploy, and manage sensitivity labels using centralized management tools, such as the Microsoft Purview portal or the Microsoft Purview compliance portal. Centralized management allows for streamlined policy updates and ensures that changes to sensitivity labels are propagated consistently across all services. Sensitivity labels are applied to individual documents and containers, such as sites and channels in SharePoint and Teams. This approach ensures that all content within these containers inherits the appropriate label and adheres to the same protection policies.
8. Stay updated with Microsoft 365 features
Provide users with training on the importance of consistently applying sensitivity labels and using them effectively across different Microsoft 365 services. Clear communication and guidelines will help users understand the role of sensitivity labels and apply them correctly.
Stay current with the latest features and enhancements in Microsoft 365’s Information Protection and Compliance capabilities to strengthen your labeling strategy. Connect with the Microsoft community and Syskit to access support resources and stay informed about Microsoft best practices and emerging threats.
Adhering to these sensitivity labels best practices helps organizations effectively manage and protect sensitive information, minimize the risk of data breaches, and maintain compliance with regulatory requirements.


