What’s Next for M365 Governance? Announcing Workspace Reviews
Table of contents
For years, our automated Access Review has been a cornerstone of secure M365 environments, built in partnership with our customers to solve the fundamental challenge of “who has access to what.” It has successfully provided a critical layer of security for thousands of organizations.
But the digital workspace never stands still. The challenges of today are more complex than ever, from the subtle risks of inactive guests and forgotten sharing links to the new frontier of ensuring your data is secure and AI-ready.
As your partners in M365 governance, we knew it was time to ask, “What’s next?“
We spent the last year in deep conversation with many of you, exploring how we could evolve our powerful review capabilities to meet these modern challenges. You told us you needed more than just access control; you needed a comprehensive view of a workspace’s entire health, from its creation to the end of life.
Inspired by your feedback, we’ve been hard at work building that future.
Today, we are proud to announce the next evolution: Workspace Reviews.
It’s a major leap forward, designed to provide the deeper insights and smarter automation required for the M365 of today, and tomorrow.
The Modern Governance Challenges We’re Solving Together
The promise of Microsoft 365 is simple: seamless collaboration. But for IT and security leaders, that simplicity has created a new generation of complex challenges that native tools were never designed to handle.
Main challenges we encounter when speaking with IT directors and admins:
- Uncontrolled sprawl
- Oversharing
- Wasted time on manual work
- Unlabeled high-risk workspaces
- Inability to track governance efforts
- End user confusion about what’s expected
The Unchecked Growth of Workspace Sprawl
It starts innocently. A new project kicks off, and a new Team is created. Then another. And another. Soon, you have hundreds or even thousands of workspaces, many of which are inactive, ownerless, or redundant.
This isn’t just clutter; it’s a rapidly expanding attack surface. Each abandoned workspace is a potential backdoor, holding old data and forgotten permissions that create silent, unmanaged risk.
The Silent Epidemic of Oversharing
In the rush to get work done, users inevitably create risky sharing links, add guests who only need temporary access, and misconfigure privacy settings. This “silent oversharing” is one of the biggest threats to data security.
The problem is that most of the time, neither the user nor the IT team has any idea it’s even happening until it’s too late.
The “Wild West” of Unlabeled M365 Workspaces
Your organization has policies for sensitive and confidential data, but are they being enforced? When workspaces lack proper privacy or sensitivity labels, you’re flying blind. You can’t protect what you can’t see.
Without proper labeling, you have no reliable way to apply security policies, prevent data leakage, or ensure your most critical information isn’t exposed in a low-security workspace.
Regularly reviewing sensitivity labels and privacy settings is essential because workspaces constantly evolve. New members join, content changes, and permissions shift. Over time, accidental changes or outdated settings can expose sensitive information or block collaboration.
Routine reviews help catch these issues early, keeping your environment secure, compliant, and aligned with how teams actually work today.
IT Admins Drowning in Manual Work
Your team’s time is your most valuable resource, yet it’s constantly drained by repetitive, manual governance tasks. Chasing down individual owners, manually checking permissions, and acting as the central gatekeeper for every minor access request turns your expert IT team into an operative service.
This manual approach doesn’t scale, burns out your best people, and prevents them from focusing on high-impact strategic initiatives.
The Invisibility of Real Metrics and Governance ROI
You run a review process, but what do you get? A simple “complete” or “incomplete” status. You have no visibility into what actions were actually taken. Were any risky links removed? Were any inactive guests deleted?
Without these granular metrics, you can’t measure your impact, prove the ROI of your governance strategy, or even know if you’re any more secure than you were yesterday. It’s like trying to navigate without a compass.
Syskit Point: A 360-Degree View of Workspace Health with Risk Reduction Metrics
To solve these modern challenges, we realized we couldn’t just add more features to the old way of doing things. We needed a new philosophy. That philosophy is at the heart of Workspace Review, our next-generation governance feature. It’s built on three core principles: empowerment, intelligence, and impact.
1. Empowerment: Shifting from a Bottleneck to a Partnership
The biggest challenge in any governance process is an overworked IT team trying to manage everything manually. The first principle of Workspace Review is to change this dynamic by empowering both the admin and the business user.
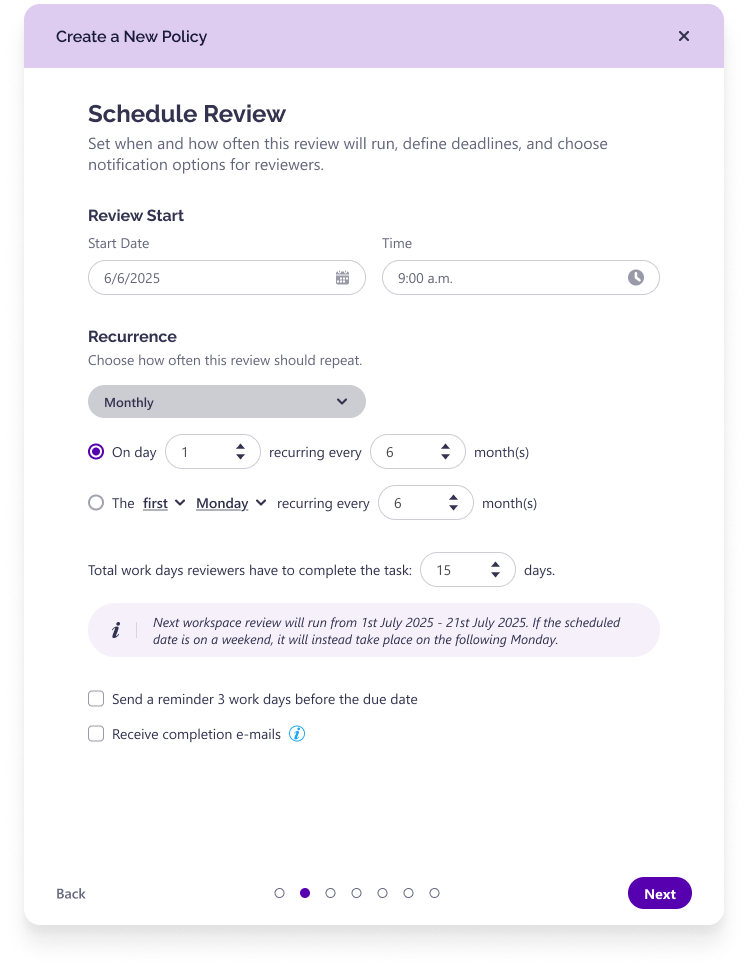
Our intuitive policy engine gives you full control to build governance capabilities that fits your exact needs. You can start in minutes with pre-built templates or create highly specific, custom policies. Define what gets reviewed, from membership and sharing links to sensitivity and privacy, and control the entire lifecycle with flexible scheduling, one-time recurrences, and manual on-demand triggers for easy testing.
This admin-level control is what enables the second half of the partnership: safely delegating responsibility to the people who know the context best, the workspace owners. But delegation only works if the process is simple. We empower owners with a guided experience that eliminates guesswork, turning a complex task into a quick, confident action. You set the rules; they execute with clarity.
2. Intelligence: Going Beyond “Who” to Understand “What” and “Why”
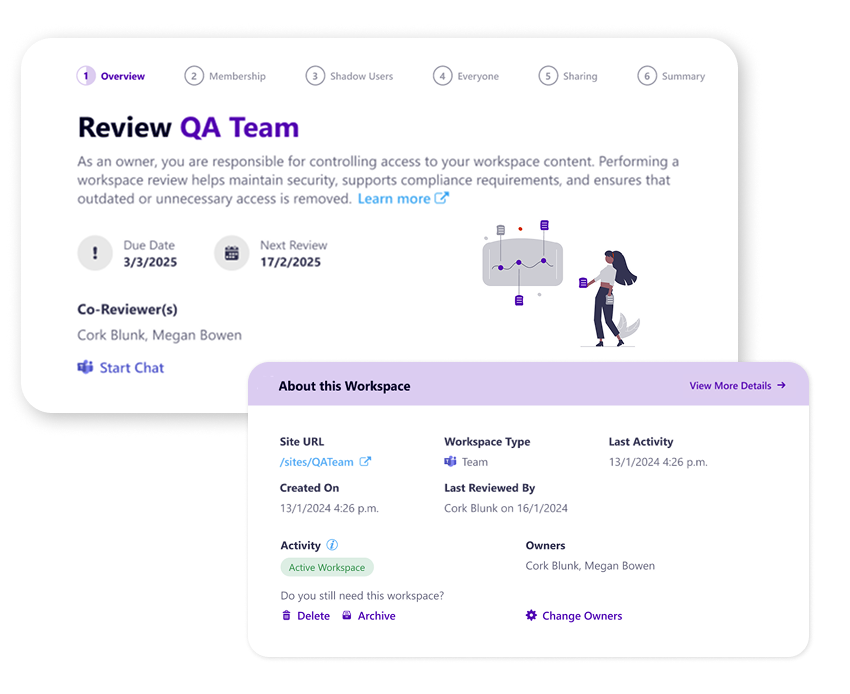
A simple list of users is no longer enough information to make a smart security decision. The second principle of Workspace Review is to infuse the process with intelligence. This means going beyond just access and providing a comprehensive, 360-degree view of a workspace’s health.
This includes automatically flagging critical policy violations that often go unseen:
- Workspace Lifecycle: Is a workspace inactive and a candidate for archival or deletion?
- Ownership Gaps: Does a critical Team have too few owners, creating an orphan risk?
- Sensitivity and Privacy Labeling: Are workspaces containing sensitive data labeled?
Most importantly, we provide recommendation-driven tasks. Instead of just showing an owner a problem, we recommend the solution: “This guest has been inactive for 90 days. We recommend removing them.” This intelligence is what transforms a review from a chore into a quick, decisive action.
3. Impact: From “Complete/Incomplete” to Measurable ROI
The final principle is that governance efforts must be measurable. For too long, success has been a “black box.” You know the work is important, but you can’t prove it.
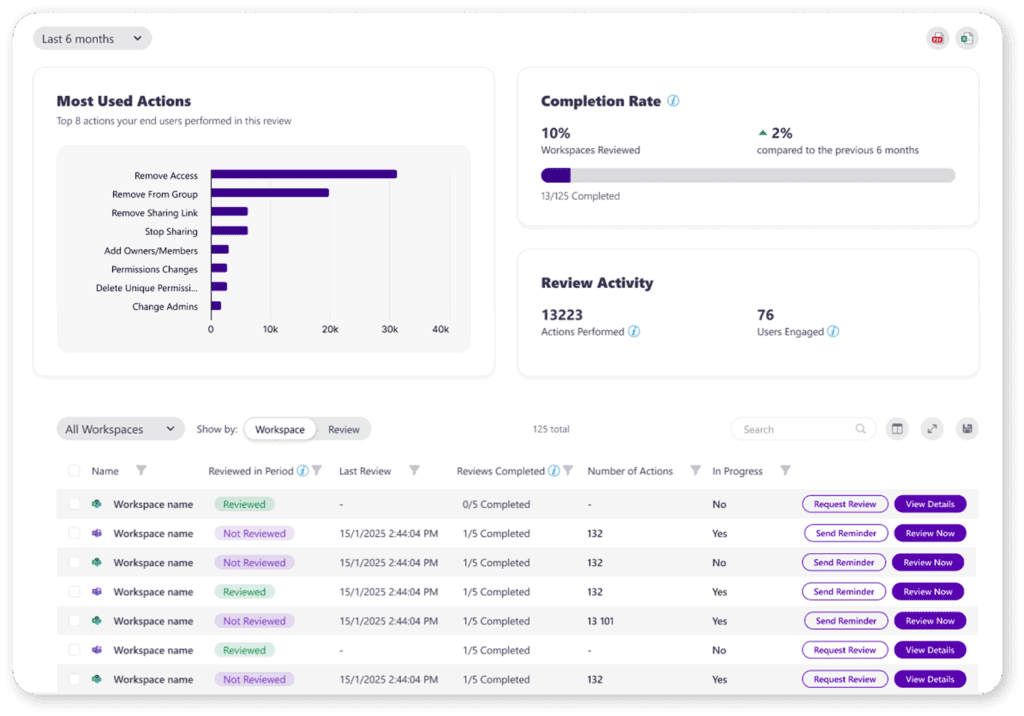
Our new Insights Dashboard was built to solve this. It moves beyond a simple “complete” or “incomplete” status to capture every granular action performed during a review. You can now see exactly how many risky sharing links were eliminated, how many inactive guests were removed, and which policies are having the biggest impact.
This data allows you to finally tell a clear, compelling story of risk reduction. You can confidently walk into a meeting with stakeholders and demonstrate the tangible ROI of your governance strategy, turning your security program from a cost center into a proven value-driver.
This new approach, built on empowerment, intelligence, and impact, is our answer to the challenges of the modern workspace. It’s the foundation for a more secure, compliant, and AI-ready M365 environment.
A Note for Our Existing Access Review Users
If you are currently using our Access Review feature, you might be wondering what this means for you. Don’t worry—your existing setup is not affected by this launch. The new Workspace Review is a separate feature, meaning your current Access Reviews and the new Workspace Reviews can run in parallel while you explore the new capabilities. You have until January 2027 to fully transition.
However, we strongly encourage you to explore Workspace Review much sooner. It is a powerful leap forward, designed to give you deeper insights and more control than ever before. Our Customer Success Team is ready to guide you through the simple transition process when you are ready.


