Battling with your IT Team
Table of contents
Recently, I attended Infosec Europe, an incredible conference about information security, not least because it was free to attend. I like an event like this because, in one or two days, you can see all of the vendors’ offerings and actually talk to the people at those companies to see if they know what they’re talking about. As a quick side note, if a company sends people to work on the stand who don’t know what that company does, then move on!
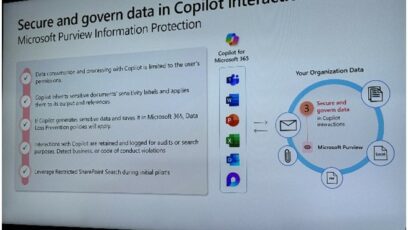
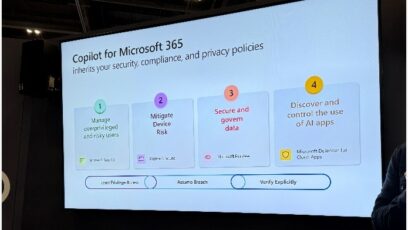
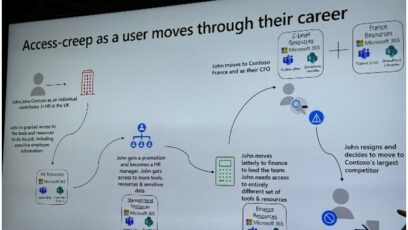
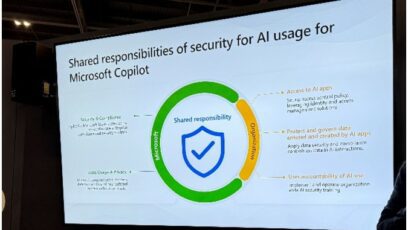
Back to Infosec. Firstly, there were some great presentations. I can’t summarize it all here, but here are a couple of slides I found particularly useful:
Secondly, there were many great talks and discussions deep-diving into security protocols and processes, as well as some very interesting discussions about the culture of security. The question that kept coming back to mind was simply “Why is there so much conflict between your IT team and your end users (dev teams, marketing, sales, etc.) when it comes to governance tasks?”
Everyone is working for the same company, surely with the same goals!? It is an all-too-common problem that business users conflict with the teams trying to look after those core systems. Why is this? And what can you do about this governance conflict?
This is a particularly important question when managing a Microsoft 365 environment. There are two basic styles of users of Microsoft 365:
- IT folk. These people are paid to govern the system, and I make sure there are no breaches of security or similar. If there is a breach, for example, a junior staff member accessing confidential information, then it can be the IT team where the finger is pointed.
When something is leaked, either internally or externally, they are the people pulled up in front of the boss with questions to answer. Because of this, they do (and should do!) everything they can to close systems down and restrict access (aka the principle of least privilege, or PoLP). - Users. Most end users of a Microsoft 365 system see the admin and/or security team as a PITA. They slow them down, make every task twice as long with “unnecessary” admin, and are often on a different wavelength. I’ve even heard the phrase “businesses run at the speed of their IT team” used as a thinly veiled criticism.
Why is this?
Understanding the governance conflict
End users often do not prioritize governance tasks because they assume that IT teams or specialized groups will handle everything for them. This misunderstanding can lead to significant issues, especially when it comes to managing metadata for different workspaces.
Metadata management
Metadata includes information such as the purpose of the workspace, its intended audience, and how it will be used. Since each workspace is unique and created by different users, IT departments cannot effectively manage this metadata without input from the workspace creators. This results in a lack of organization and efficiency, particularly when everybody is so incredibly busy.
Challenges in the enterprise
In large enterprises, the problem is amplified due to the sheer number of users and workspaces. Employees often search through numerous folders and spaces, making it difficult to find relevant information. Effective communication strategies are crucial to ensure that end users understand the importance of maintaining governance and metadata.
Improving Communication and Responsibility
Overcoming IT’s push approach
IT departments frequently adopt a “push” approach, where they delegate tasks to end users without adequate explanation or support. This approach can be perceived as dismissive, leading to resistance and frustration among end users. IT staff might view end users as lacking understanding, while end users may feel overwhelmed and unsupported.
Proposed solution
A shift towards a more supportive and communicative approach can help – i.e. a change in culture. This includes explaining the importance of tasks and how they benefit both the individual and the organization. Strong communication strategies should be employed to make end users feel valued and responsible. I generally find that the starting point for this is to “assume good intent.” Most people are doing their best with limited time and resources to do the right thing – start from this assumption and see where it gets you.
Integrating onboarding documents and digital hygiene
Creating a culture of responsibility
Onboarding documents should be an integral part of the company’s culture, akin to maintaining personal hygiene. Just as making your bed every morning is a routine that instills discipline, taking care of digital data should become a habitual responsibility for every employee.
Steps to Implement
- Onboarding Documentation: Develop comprehensive yet straightforward onboarding documents that outline the responsibilities related to data governance and metadata management.
- Regular training: Instead of overwhelming end users with extensive training sessions, provide them with regular, bite-sized pieces of information. This can include tips, quick guides, and best practices.
- Use of automation tools: Utilize tools like Microsoft Copilot to create automated articles and updates on platforms like SharePoint. This ensures that end users have access to up-to-date and relevant information without being inundated.
Setting clear expectations
It’s essential to set clear expectations regarding data management responsibilities. When everyone understands what is expected of them, they are more likely to be diligent and proactive.
Communication Strategies
- Frequent updates: Provide regular updates and reminders about best practices for data management.
- Positive reinforcement: Recognize and reward employees who consistently follow good digital hygiene practices.
- Feedback mechanisms: Implement systems for end users to provide feedback on the support they receive, ensuring continuous improvement.
By addressing the gaps in communication and responsibility between IT departments and end users, organizations can significantly improve their data governance practices. This involves making onboarding documents a part of the company culture, setting clear expectations, and utilizing automation tools to facilitate continuous learning and adherence to best practices. Ultimately, fostering a collaborative environment where both IT and end users understand and value each other’s roles will lead to more efficient and effective data management.
Do it with the help of technology
Of course, it goes without saying that we stick to all of these principles at Syskit when managing our own information and data. We take security very seriously. We are both ISO/IOC 27001 and SOC 2 Type 2 compliant. Does this make working here more difficult? No! Everyone understands the importance of what we do and, therefore the importance of security.
But I think it is more than that and in fact it’s really to do with the culture that understands that we all have jobs to do, some of us are more worried about security, some of us are more worried about new innovations and some of of us just want to cut great code.
But when you can bring those things together, you can create great products like Syskit Point, designed to help customers with visibility, governance, and security problems in Microsoft 365 not least by understanding that in my experience most IT security admins are just trying to do right by the business.
Specifically, the ability to delegate governance tasks to site owners and, therefore, delegate governance to the right people can help you achieve both aims of having highly productive teams, but also teams acting in a way that supports the security of your environments. Find out more about Syskit’s governance solution.