Microsoft Copilot – How to apply best practices with SharePoint
Table of contents
Most organizations are now evaluating Microsoft’s Copilot solutions and understanding how generative AI solutions combined with their business data can help their business achieve more. But, most of them hit a roadblock: Is the content in our tenant relevant and secure enough to enable Copilot?
We say that Artificial Intelligence is a great amplifier. If you have good quality content, it will amplify everyone’s productivity. However, if your environment doesn’t follow best practices, especially regarding security, Copilot will amplify that and highlight your current security flaws.
Microsoft is aware of this challenge and recently published some very important guidance for organizations in an article called Microsoft Copilot for Microsoft 365 – best practices with SharePoint.
While Microsoft shares some great guidance and high-level steps on how to use the SharePoint Premium Advanced management features to configure your environment, in this blog, we will show you how easy it can be to get your SharePoint environment Copilot-ready with Syskit Point.
How does Copilot for Microsoft 365 work?
Let’s first do a quick recap of the basics. What makes Microsoft 365 Copilot unique is its ability to utilize all your data in the Microsoft Graph with the GPT-4 Large Language Model (LLM) and provide answers and solutions grounded in the best data available: Your own data. You can view a nice Microsoft graph below on how the whole process works, and of course, you can learn more about it on Microsoft Learn.
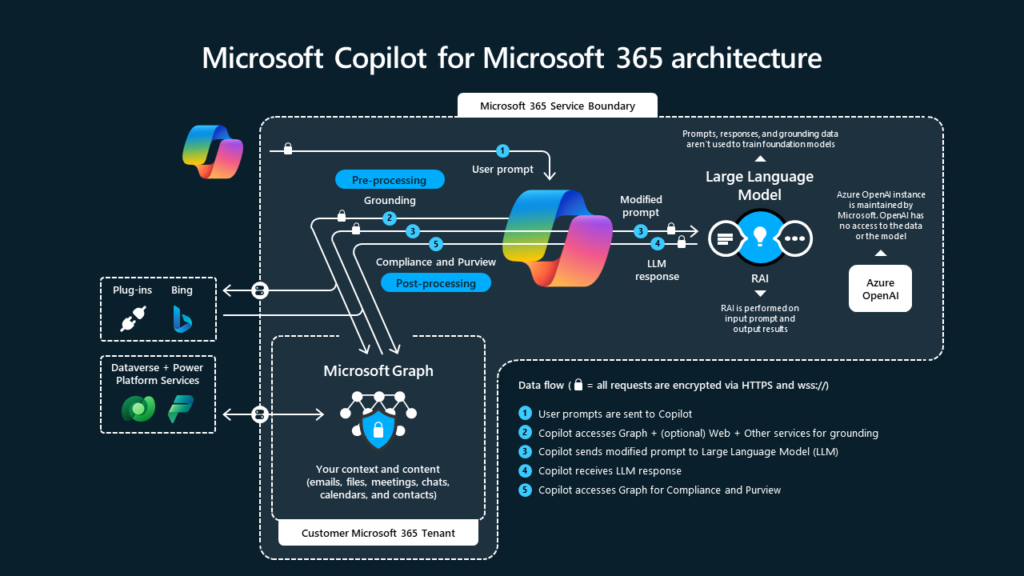
What do SharePoint permissions have to do with Microsoft 365 Copilot?
Microsoft 365 Copilot can access data from all our tenant, whether it’s Outlook emails, Teams chats and meetings, and all our data in SharePoint and OneDrive. SharePoint stands out since that is where all our documents, videos, and more are stored.
Do not worry. Just like Microsoft Search, Copilot only has access to information that you have at least read access to. Copilot will never use information that you do not have permission to access, but what if your tenant has sites with misconfigured permissions?
Too many companies have practiced what we call “Security by Obscurity” for long periods, hoping that users do not access data they do not know about, even if technically they would have access to it.
However, Copilot’s ability to parse terabytes of data in milliseconds makes it easier for everyday users to discover they didn’t know they have access to inside a Copilot answer and expose your organization to internal data leaks.
We call this oversharing, and it’s one of the biggest challenges organizations are facing today in their Copilot deployments.
However, whether you plan to implement Copilot or not, fixing oversharing should be one of your main priorities to ensure your organization is secure from internal and external risks.
Microsoft best practices for SharePoint before implementing Copilot
In the recently released list of best practices that every SharePoint admin should follow, Microsoft has shared five different steps you should take to combat oversharing and secure your Microsoft 365 data:
- Review site-level sharing controls and remove “Everyone Except External Users” from the people picker.
- Identify inactive sites, then restrict access or delete them.
- Identify potentially overshared content.
- Take remediation actions to address oversharing.
- Set restricted access control and block file download policies on business-critical sites.
Let’s deep dive into each step, understand why it’s important, and how we can easily do it with Syskit Point.
Step 1 – Review site-level sharing controls and remove “Everyone Except External Users” from the people picker
In our first recommendation, Microsoft recommends that we try to fix the problem from the source, review site-level sharing controls, and remove “Everyone Except External Users” from the people picker.
Microsoft gives some great recommendations, such as configuring the default sharing links to be most restrictive (for example, from company-wide to specific people) and making sure that any access request goes to the SharePoint site owners (which they do not mention but make sure you do not have any orphaned sites!).
There are some recommendations; however, in our first step, you need to put more consideration into restricting members from sharing content. We, of course, always assume that Site Owners will make fewer mistakes than members, but if there’s something we learned from our on-premises days is that restricting members from being productive will turn into Shadow IT problems, and instead of empowering users to be more productive, we might end up back in the “I am waiting for IT” days of SharePoint.
– Sharing and access management
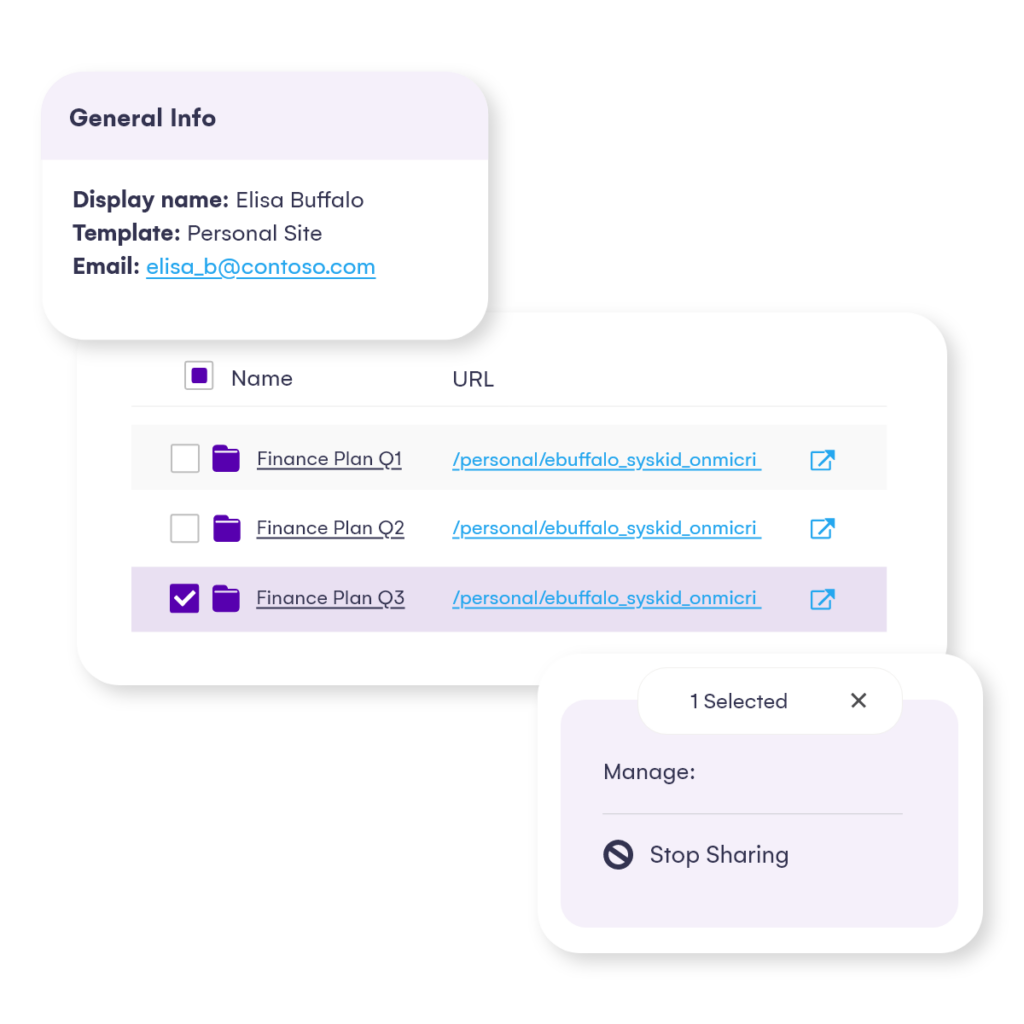
With Syskit Point’s centralized inventory, there is no need to restrict collaborative options or risk end-user adoption. You have complete control of who has access to what down to the file level and real-time actions to manage access and sharing accordingly.
Use the site dashboard or the Permission Matrix to easily identify who can access your content, including Everyone except external users, other group-type memberships, and all sharing links. Easily drill down to the file level and remove unwanted access with real-time management actions, all presented in an easy-to-use and understand interface.
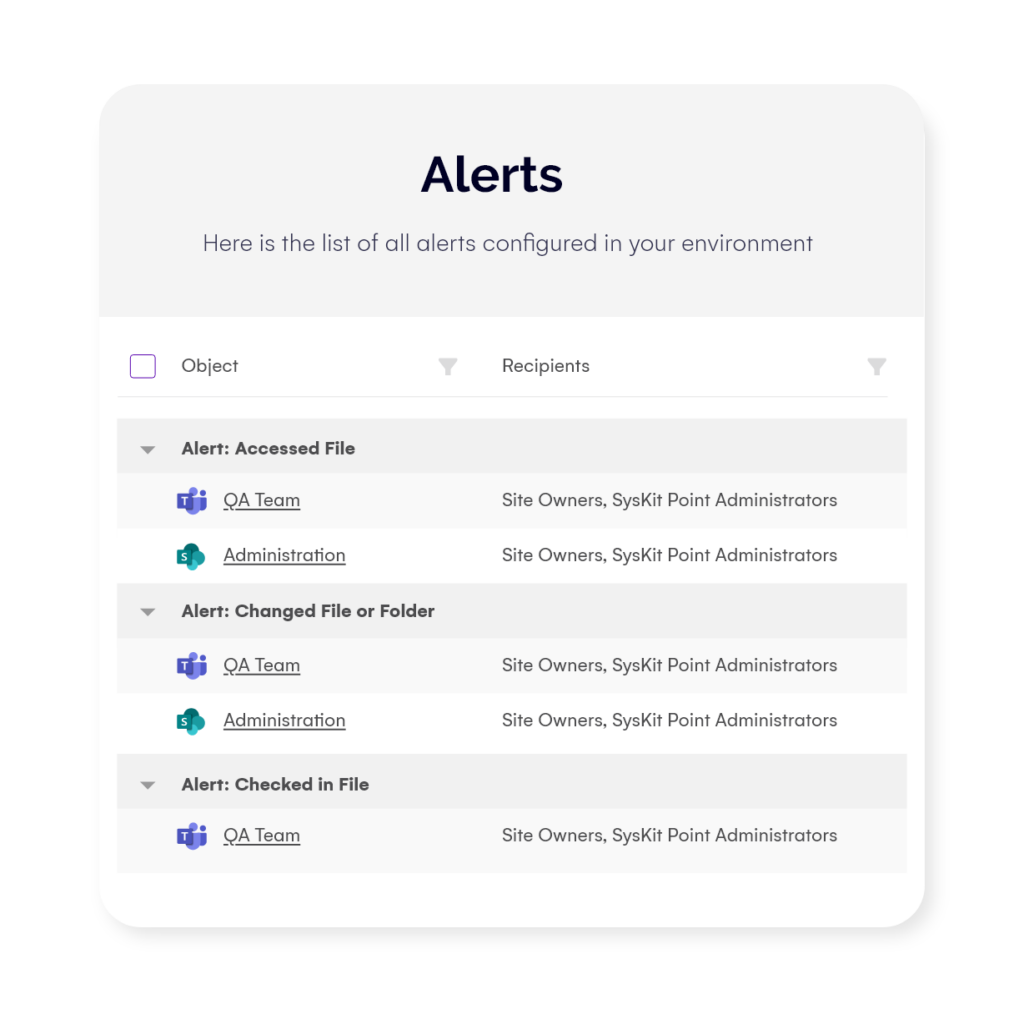
– Alerts
If you want to keep a tighter look at what is happening on your sites, use the alerting option to instantly get notified if suspicious internal or external sharing is happening.
– Access requests
Streamline access requests for sites, teams, and groups – M365, as well as security and distribution groups – using the Syskit Point workspace center. Use custom approval workflows to boost security for confidential or highly sensitive workspaces and introduce second-level approval if needed. The history of all access requests and approvals is at the disposal of admins to keep control and, of course, for audit and compliance purposes.
The Syskit Point Team’s app provides a single source of truth for your end users to get a detailed inventory of all teams, sites, and groups available in your organization. At the same time, it allows them to gain access more easily and prevents sprawl and workspace duplication due to lack of visibility.
Step 2 – Identify inactive sites, then restrict access or delete
One of the newest challenges that Microsoft customers are starting to face is too much content in their environment. According to Microsoft organizations are spending over 46 billion dollars per year storing and managing content – and let’s be honest, while paying for content we need to keep our business running makes sense, why pay for duplicate content or content that is not relevant to our organization anymore?
In the era of Copilot, we have a new challenge! Stale, old, or duplicate information can confuse Copilot as it doesn’t know which document is the real source of truth. Is it the document from your OneDrive that you just moved to a new folder, is it the document in the project Site, or is the document in an old site you haven’t touched in years?
Irrelevant content that is not useful to your company anymore will cost you every day in storage costs and will have an even bigger impact on your Copilot adoption if you do not work on getting rid of it! The big challenge however is, discovering this content.
– Lifecycle management governance policy
Using Syskit Point’s lifecycle management governance policy, you automate the detection of inactive sites and send tasks to workspace owners to decide the appropriate action. Owners get the task in their inboxes and get to choose whether to Archive it or Delete it or, for compliance reasons, keep it for the agreed period, even though it is inactive.
When the site, group, or team is archived, all permissions except owners are removed, making it no longer accessible to previous members, meaning that Copilot will also no longer use this data to provide them with answers.
Steps 3 and 4 – Identify potentially overshared content and take remediation actions to address oversharing
Wait – didn’t we already talk about oversharing so much in this blog post? We mentioned earlier that it’s one of the biggest problems affecting organizations today, and while in Step 1 Microsoft shared recommendations to avoid future oversharing – Step 3 focuses on existing Overshared content. All the recommendations from Microsoft leverage SharePoint Advanced Management features such as Data Access Governance and upcoming features such as SharePoint Site Access reviews.
Something to be aware of is that at the time of writing this blog post in March 2024, Data Access Governance reports will only show you new sharing links (of the report of your choice) in the past 28 days, which makes it very difficult to find content that was shared using an Everyone Except External Users or Anyone links more than a month ago.
– Syskit Point reporting and management
Point provides a wide range of reports to help you detect and contain potential oversharing.
- The Sharing Links report gives a detailed overview of all sharing links created in your environment. You can easily detect and manage sharing with specific people, as well as anonymous and company-wide links directly from the report in bulk.
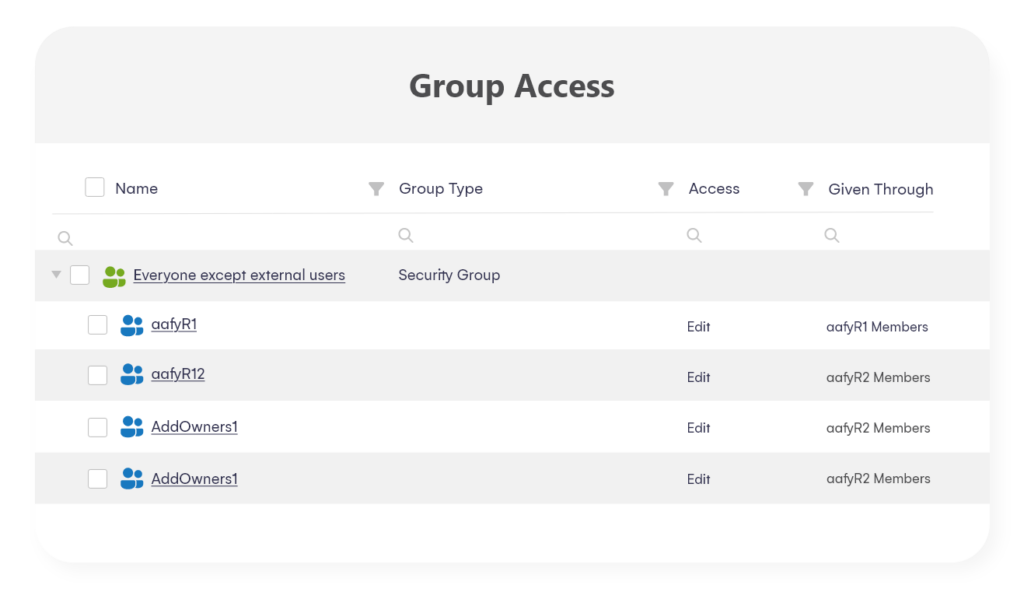
It will provide information for sites, teams, and groups, as well as OneDrive. Even more important, Point detects all sharing link types and access regardless of how long ago it was created (more than 28 days in the past). - The Group Access report can help you detect oversharing with large groups (by the number of members) or with specific groups like Everyone except external users, Everyone, and All users’ groups. All group types are supported – security, distribution, M365, and SharePoint.
- Syskit Point User Access is one of the vital reports, as Copilot relies on end-user permissions. It provides a list of all workspaces on your tenant, down to a file level where a particular user has access to. Revoke any unwanted access or sharing in real time directly from this report.
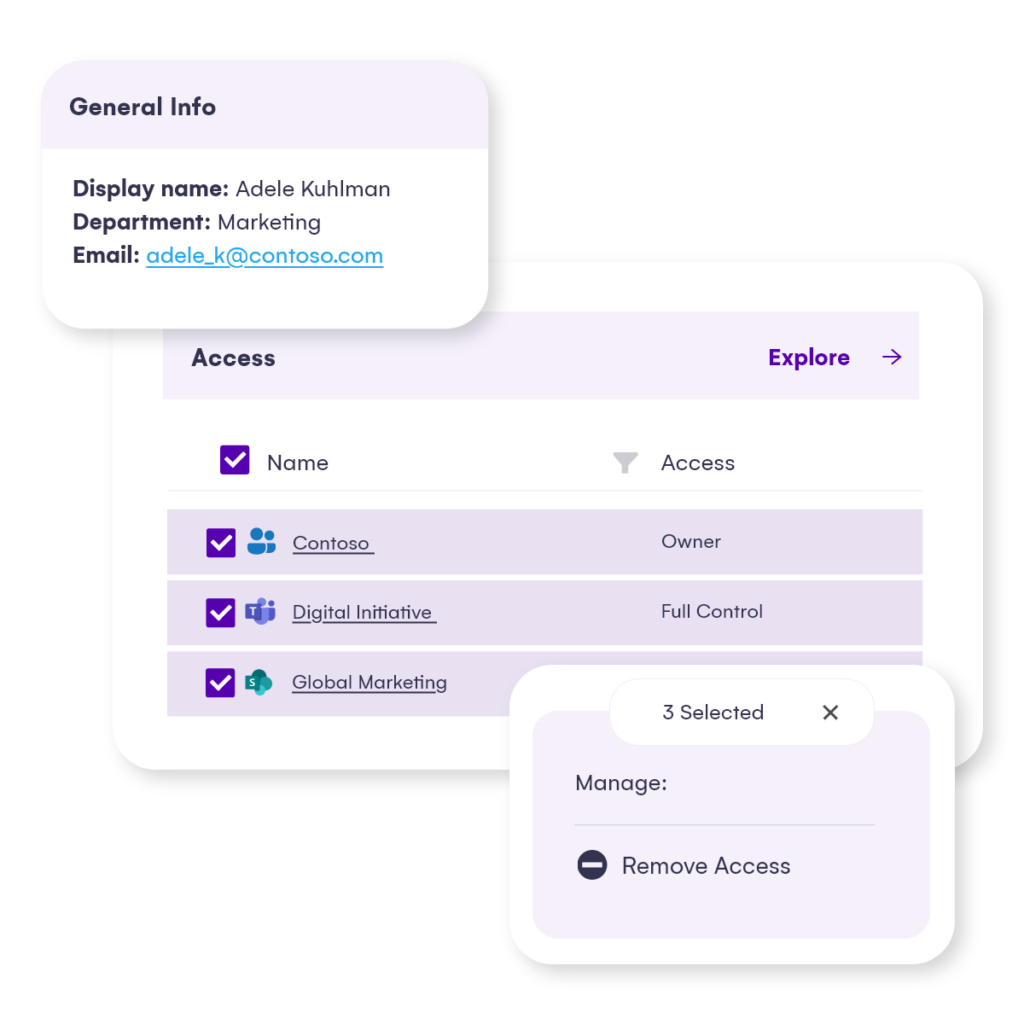
- For a particularly sensitive workspace, use our Shadow users policy. This automation crawls the tenant and detects if a particular workspace you want to track has any access granted, directly or via a sharing link, outside the group/team membership. If such a violation is detected, action to remove unwanted users is available in real time.
– Change history
You can complement all of those reports with audit reports that Syskit Point holds for 90 days (optionally up to 1 year and more) to make it easier to detect all permission changes and user activity on your tenant or a particular site. Easily pinpoint who did what and what activities have led to potential oversharing.
Both admins and site owners can try and explore the following reports:
- User activity – what a particular user (internal or external) has been doing across the sites and what changes have been made by this user.
- Permission changes – all access and sharing activities for a particular site or tenant-wide.
- File and page activities – all content changes, including modifying, deleting, downloading, etc., done by internal or external users.
- Audit Log Overview – all activities from your tenant, including user, file, and folder changes, permission changes, and all configuration changes across the tenant.
– Access reviews
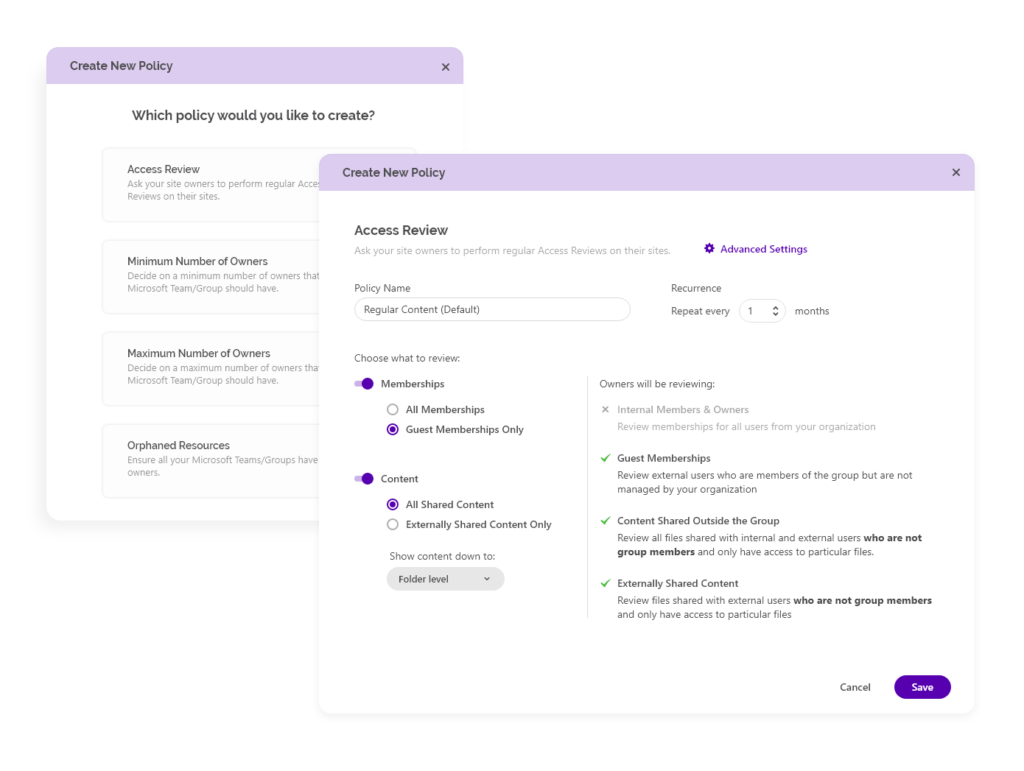
When you want to scale the Microsoft Copilot for M365 rollout to the entire company, IT teams need to include your site owners to ensure that oversharing is continuously remediated. For that purpose, we built the Syskit Point Access Reviews governance automation.
This governance automation allows the admin to schedule regular access reviews, keep control of the review progress, and get detailed audit reports of performed actions at the end of the review period.
When the time comes, Syskit Point sends tasks to site owners, asking them to review memberships and sharing links for their sites. This includes external and internal sharing, as well as guests.
They need to either remove the unwanted access or leave it as is but provide a comment on why this is needed. They become reliable partners in governing the M365 environment by confirming that only the right people can access their data.
This way, we empower all admins to eliminate manual interference and make the review process more reliable and more accessible for your end users, resulting in minimizing any chance of oversharing.
Additional benefits you get with Syskit Point
But Syskit Point is not just about that. Here’s a quick overview of the most important benefits you get with Syskit Point in your admin toolbelt:
- Sharing and access reporting, alerting, and management actions are available for admins and for the site owners as well, enabling you to delegate governance into the hands of the people who have the best operational knowledge to secure their content. The application is built with non-IT personnel in mind, providing great UX for your owners.
- There is no limit to how many times you can generate reports, and they are available instantly in the user-friendly interface.
- Point detects all sharing links and access regardless of how long ago it was created.
- Reports are built with small and enterprise clients in mind, making them scalable and robust.
- Audit logs can be obtained for 1 year or more.
- Syskit Point does not require any SharePoint Advanced Management add-on, SharePoint Premium, or Entra ID P1/P2 licenses to provide these reports and governance automation, saving you thousands of dollars annually worth.
Step 5: Set restricted access control and block file download policies on business-critical sites
In our final step, Microsoft shares two new recommendations, first around blocking file downloads using the block download policy (which can be a security requirement but has no impact on Copilot) as well as make sure you use Microsoft Purview to apply encryption to your documents. Microsoft has a very detailed blog post on Microsoft Purview data security and compliance protections for Microsoft Copilot which explains how Purview and Copilot work together.
As those configurations are often done by an Information Protection administrator and not a SharePoint administrator, we will not deep dive into those settings in this blog post, but make sure you talk to your Information Protection admin as you implement Copilot in your organization.
Get Copilot ready today
We hope this blog post was valuable in showing you how Syskit Point can help you make your tenant Copilot-Ready, and whether you plan to implement Copilot tomorrow, or in a few years, you should start implementing those security best practices today.
If you want to see Syskit Point in action, check out our webinar on securing and governing Microsoft Copilot:
Start securing your environment and optimizing your storage today with our 21-day free trial in your own environment.


