New in Syskit Point: Ownership best practices, orphaned teams cleanup, and improved external users management
Table of contents
Syskit Point 19.0. is out, and it comes with some exciting new features and customizations. New automations will help you ensure company policies are effectively enforced and stay compliant by including data owners as reliable partners. So, let’s dive deeper and explore how you can keep your environment clean and secure with the new improvements.
Office 365 automated workflows
Keep your environment healthy by enabling workflows based on your policies.
These policies will allow you to:
- define a custom threshold that triggers the automated workflow,
- escalate to higher instances in case of a task’s non-completion,
- automate actions if no one responds.
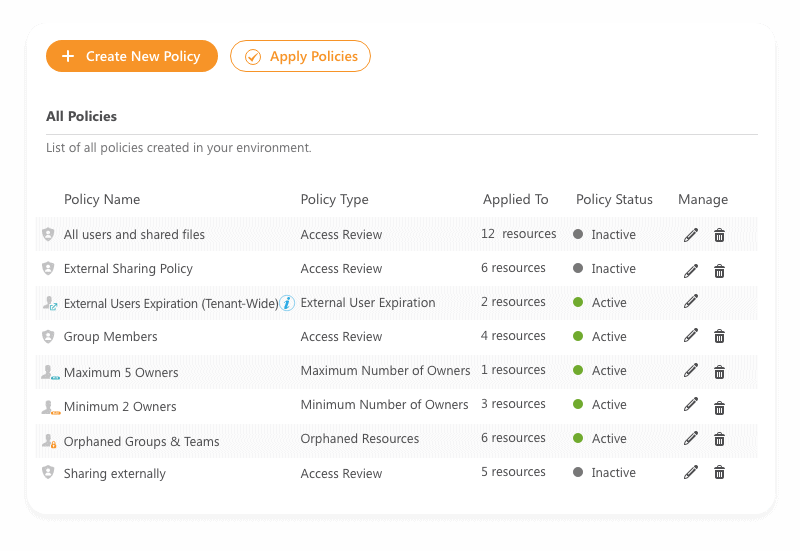
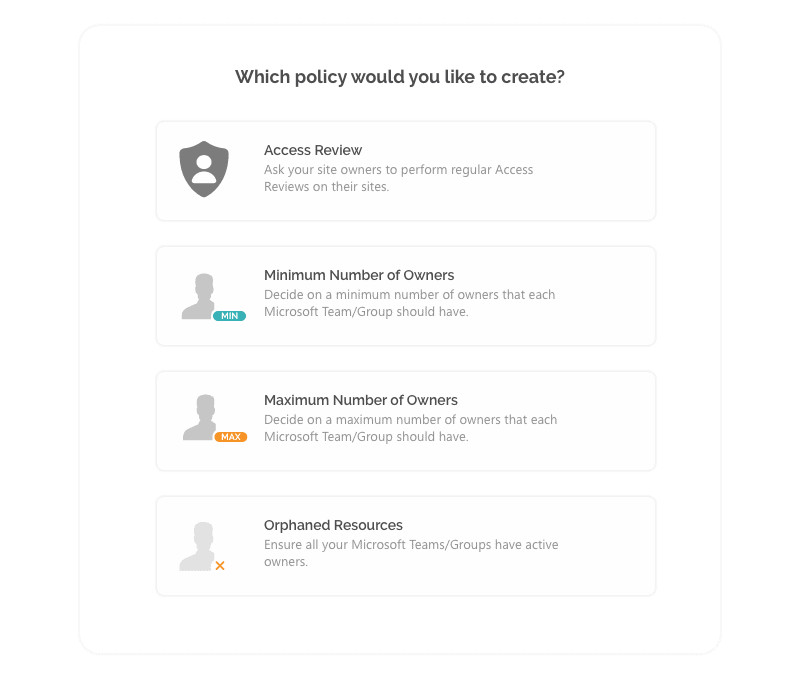
Enforce at least two owners
One of the best practices is that every team and group has at least two owners. In that case, if one of the owners leaves, the team will not stay unattended. With new governance policies, your IT team can sit back and relax as Syskit Point solves this problem automatically. Once it detects a team with less than two owners, it asks the current sole owner to assign a new one to help them manage this team.
If no one takes responsibility for the non-compliant team, Point offers a set of escalation measures to minimize administrative tasks. These measures such as auto-archival, auto-deletion, or delegation to a higher instance can help you ensure that your teams are well-governed without manual intervention.
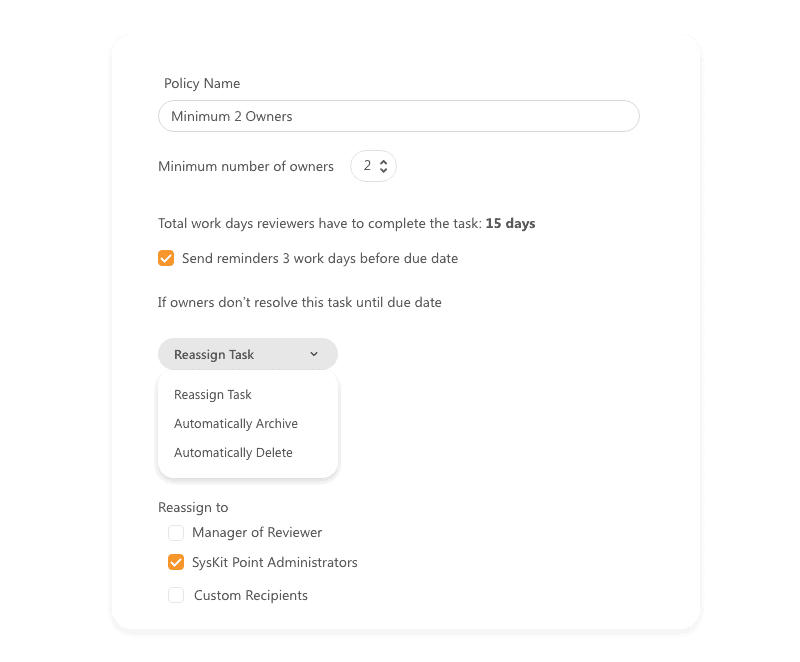
Enforce a maximum number of owners
Having too many team owners is not recommended, and common best practices advise that up to five owners are ideal. The higher the number of owners a specific team has, the higher the chances are that no one will take full responsibility. With Syskit Point, you can detect all teams and groups with too many owners and ensure that all unnecessary ones are removed.
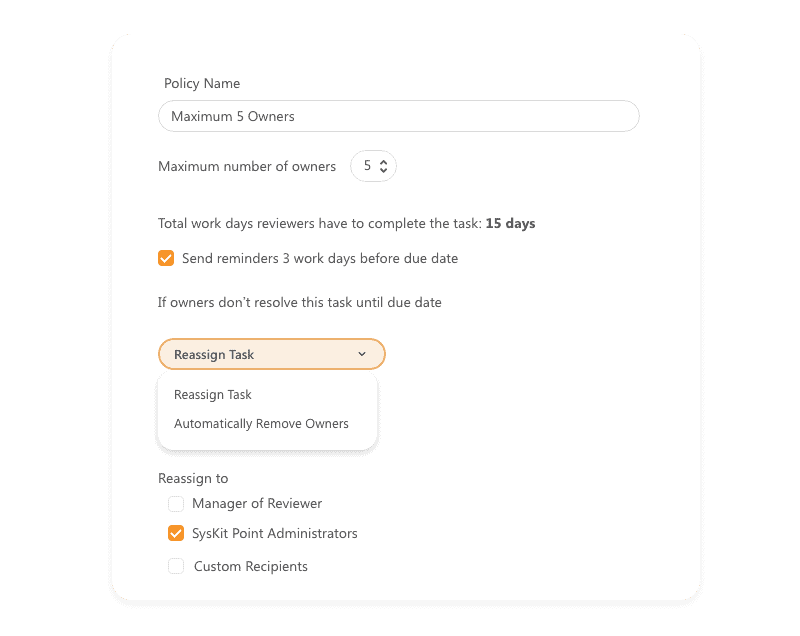
Delegation to higher instances, such as managers and admins, as well as an automated removal action, can help your teams comply with these governance policies. Depending on the group and team type and their purpose, you can define different rules for a maximum number of owners to apply accordingly.
Clean up orphaned Office 365 workspaces
Teams and groups without active owners can present potential security and productivity concerns. If a team ends up ownerless, no one is left to ensure data safety, collaboration, and proper membership management.
This is where Syskit Point’s new governance workflow jumps in by:
- automatically assigning the last owner’s manager,
- asking members to suggest a new owner,
- or letting administrators decide who should be a new owner.

Depending on the data’s sensitivity, you can create and apply different policies to different groups and teams to keep your environment free of orphaned workspaces.
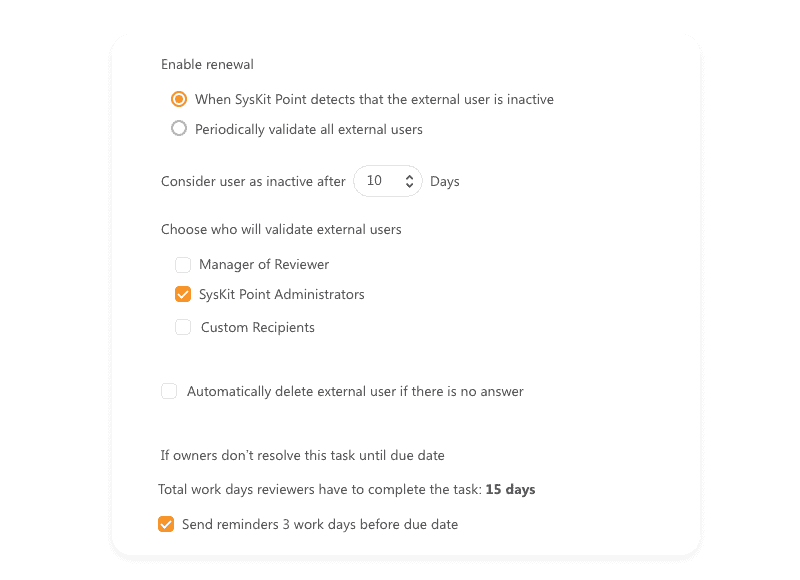
Recertify your Office 365 guest users
External collaboration is an integral part of our everyday work, yet it may bring many security challenges. That’s why it’s essential to have a proper mechanism to continuously review guest users and regularly restrain their access if needed.
With Syskit Point’s new recertification workflow, you can ensure that guest users are reviewed on a periodical basis or whenever Point detects them as inactive. The newest version brings automated removal of guest users that no one takes responsibility for, leaving your environment completely secure, even when you are not actively watching.
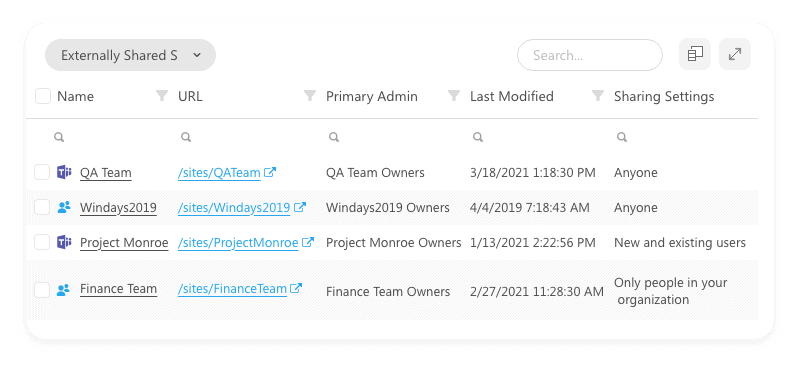
Simpler Office 365 external users reporting
Want to find out how many external guest users are on each site, but clicking on individual ones seems like a daunting task to do? Syskit Point has your back. We’ve been working on a series of improvements to make it a lot easier for you to find and report on your external users. With the newest version, you can see immediately on the main Sites overview which sites have external users and how many of them. When generating reports, Point will help you prefilter the sites that have external sharing detected.
If you want to focus only on File and Page Activities or Site Permissions Changes related to external users, Point makes it a lot easier. Now, you can use our updated filters for Audit log reports and save yourself some time. The same is possible for the User Activities report if you are interested in the activities related to external sharing.