Power Platform ownership best practices: How to avoid orphaned apps and flows
Table of contents
Microsoft’s Power Platform (Power Apps, Power Automate, Power BI, Power Pages Copilot Studio) has revolutionized how organizations approach business process automation and application development. It empowers citizen and professional developers to build and deploy solutions rapidly, accelerating digital transformation and driving efficiency. Development democratization promotes innovation by allowing business units to create solutions directly.
However, the rapid proliferation of apps and automated workflows introduces significant governance challenges if not managed proactively. One critical yet often overlooked aspect is ownership. When an application or flow is created, it is tied to a specific user account – the owner. This owner holds the keys: the ability to modify, share, manage connections, and ultimately delete the resource.
What happens when an app or flow is orphaned?
What happens when that same owner leaves the organization, changes roles, or deactivates their account? Without proper planning and alternative ownership structures, these vital digital assets can become orphaned.
An orphaned app or flow might continue to run for a time. Still, it exists in a management void – uneditable, unshareable by standard means, and often invisible to IT until it fails, causing potentially significant business disruption.
This article provides a comprehensive guide to understanding the critical importance of Power Platform ownership, the risks associated with orphaned resources, and most importantly, the best practices and tools organizations can implement to ensure continuity, visibility, and robust governance over their low-code solutions. If this article cannot help you, Syskit Point could be the solution you need for some of these headaches.
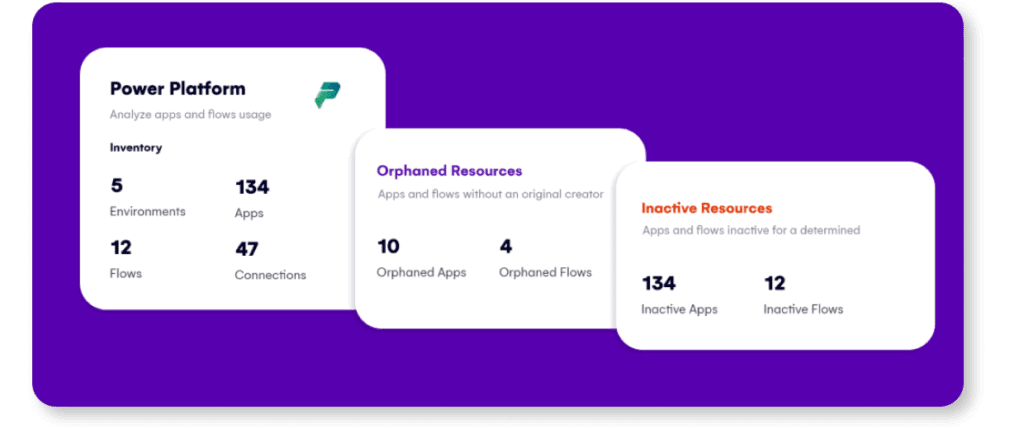
Syskit Point brings much-needed clarity to the chaos of Power Platform sprawl. It gives IT and admins a single place to detect and explore every Power App, Flow, and Power BI asset across the environment. With real-time visibility into ownership, access permissions, and usage patterns, it becomes far easier to identify orphaned or unused resources before they become a problem.
Syskit Point also highlights premium components and connection details, helping prevent security risks and unexpected costs. Most importantly, it lets you take action, such as assigning new owners or removing outdated apps and flows, so you can maintain control without hunting through layers of hidden dependencies.
Why ownership matters: The foundation of responsible innovation
Clear and active ownership is not just an administrative detail; it’s fundamental to the responsible and sustainable use of the Power Platform. Without it, chaos and risk can quickly undermine the benefits of rapid development.
Accountability and responsibility: Every business process or application, regardless of how it was built, needs someone accountable for its function, maintenance, and impact. I sometimes use the RACI model for business-critical apps. The Ownership designates this responsibility. The owner (and designated co-owners) are the contact points for issues, updates, and questions regarding the asset’s purpose and operation. How to make and use RACI charts – Microsoft 365.
Business continuity and resilience: Business processes, especially automated ones, must be resilient. What happens if a critical Power Automate flow fails? Who fixes it? If the only person who understands or can edit the flow is no longer available, the process breaks down, potentially halting operations. Proper ownership structures, particularly co-owners or service accounts, ensure someone is always available and empowered to manage and repair critical assets.
Security and compliance adherence: Power Platform solutions often interact with sensitive data and integrate with various systems. Owners ensure their apps and flows adhere to company security policies and data privacy regulations (like GDPR or CCPA) and utilize connections securely. Many organizations I managed have used data policies we enabled across all environments to ensure this. Orphaned resources escape this oversight, potentially harboring outdated connections, excessive permissions, or non-compliant data handling practices.
Lifecycle management and evolution: Digital solutions are not static; we can see this outside the Power Platform. Look to loop components; they have dynamic data, and my dream? Replace all static parts of SharePoint and Power Apps (label, textbox, …) with loop components. But that’s another story. They need updates to accommodate changing business needs, underlying platform updates, or evolving security standards. Owners drive this lifecycle, deciding when an app needs new features, when a flow’s logic must be adjusted, or when an asset is obsolete and should be retired. Without an active owner, solutions stagnate, become inefficient, or break.
Visibility and control for IT: IT and Power Platform administrators need visibility into the digital estate they manage. Knowing who owns what allows them to understand the purpose of various apps and flows, assess their impact, manage capacity, and enforce governance policies effectively. Orphaned resources represent blind spots, making comprehensive management impossible.
The unseen threat: Risks of poor ownership management
When managing Power Platform environments with orphaned resources, I’ve learned one thing: failing to manage ownership effectively isn’t just inconvenient; it poses three tangible risks to the organization, and here is what I discovered the most in cross-EU companies:
Security vulnerabilities and data breaches: Orphaned apps or flows might retain connections (e.g., SharePoint, SQL Server, external services) established by the departed owner. If these connections have elevated privileges or access to sensitive data, they represent a security risk.
Compliance violations and penalties: Apps and flows handling personal or regulated data must comply with relevant laws and internal policies. An orphaned resource cannot be easily audited or updated to meet new compliance requirements.
Wasted resources and licensing costs: Orphaned resources may continue consuming resources – API calls, data storage, and premium licenses – even if they are broken or no longer needed. Without an owner to assess their value and necessity, the organization continues to pay for digital assets that provide no benefit, contributing to license sprawl and unnecessary costs.
How apps and flows become orphaned
Understanding how resources become orphaned helps in designing preventative measures:
Employee departure is the most frequent cause. Let’s say an employee named Vlad builds apps or flows for themselves or their team. When Vlad leaves the company, his Azure AD (Entra ID) account is turned off or deleted. The Power Platform assets would instantly be orphaned if he were the sole owner.
Internal role changes and transfers: Vlad moves to a different department or role where he no longer needs or manages the apps/flows he previously built. Without a formal handover process to the new owner, Damir, these assets will be forgotten and effectively orphaned when the original owner loses context or access permissions relevant to the old role.
Project handovers gone wrong: In this scenario, Vlad is part of the project team or an external contractor who builds a solution. At the project’s conclusion, the handover to the business unit or IT support team is incomplete. Ownership is never formally transferred from the builder’s account to a designated operational owner (like a service account or a team lead), leaving the asset vulnerable when the project team disbands or the contractor engagement ends.
Use of non-standard or personal accounts (discouraged): In poorly governed environments, users might initially build solutions using personal Microsoft accounts or non-standard credentials. This practice is highly discouraged as it inherently creates ownership and security risks, making resources instantly orphaned from the organization’s perspective if that external account owner becomes unavailable.
Defining the problem: What are orphaned flows and apps?
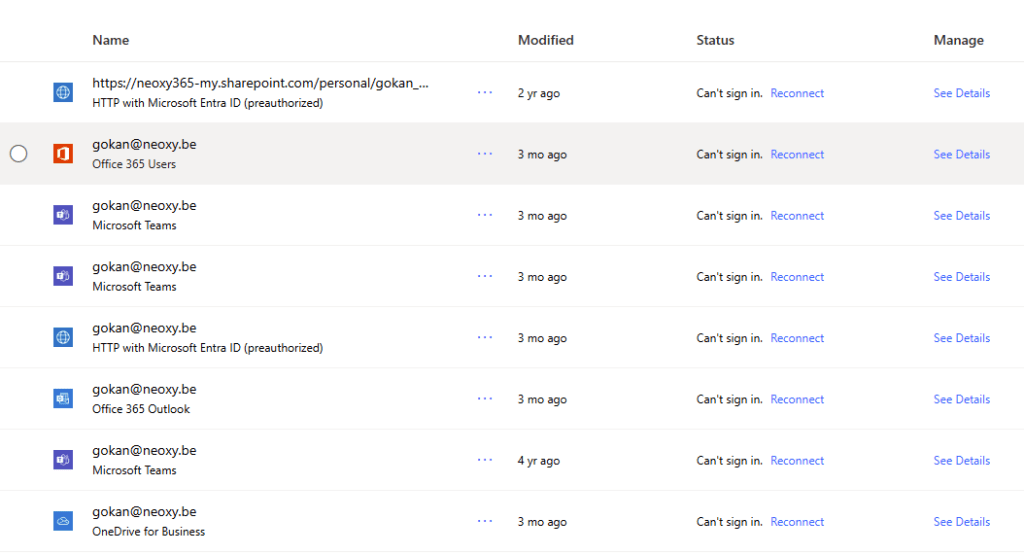
Let’s clarify what constitutes an “orphaned” resource in the Power Platform context. A Power App or Power Automate flow is considered orphaned when its primary owner’s account in Azure Active Directory (now Microsoft Entra ID) has been deactivated or deleted. The platform identifies the owner based on their unique object ID in Azure AD. Once this link is broken, the resource lacks a valid, active primary owner to manage it through the standard maker portals. While an orphaned flow might continue running for some time (if its connections are still valid, e.g., using shared service accounts or connection credential caching persists), it enters a state of limbo.
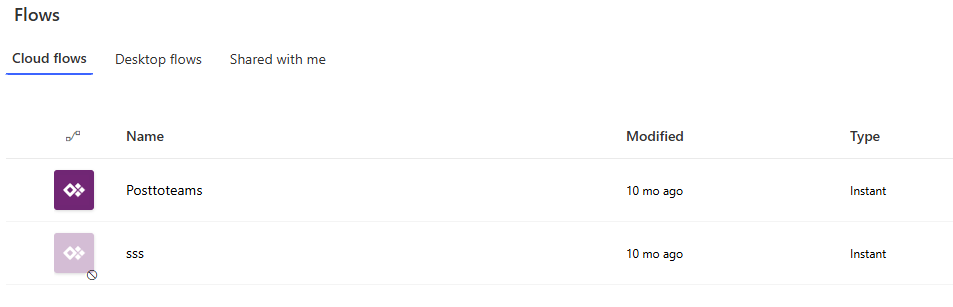
Key management actions become impossible or extremely difficult for standard users or even fellow team members:
- Editing: Cannot be opened in the editor.
- Sharing: Cannot be shared with new users or groups.
- Permissions management: Existing permissions cannot be easily modified.
- Connection management: Updating or changing connections becomes problematic.
- Deletion: Cannot be easily deleted by non-administrators.
- Exporting/importing (within solutions): Management via solutions becomes impaired.
Distinguishing between Inactive vs. Orphaned
It’s essential to differentiate between an inactive asset (one that hasn’t been used or run recently but still has an active owner) and a truly orphaned asset. Inactivity might warrant archival or deletion based on policy, but the owner can still be contacted. Orphaned assets lack this crucial link, requiring administrative intervention. Power Platform administrators can typically reassign ownership of orphaned resources via the Power Platform Admin Center, but this is a reactive measure. Identifying these assets proactively and preventing them from becoming orphaned in the first place is far more efficient and less risky.
The built-in solution: The critical role of primary and co-owners
The Power Platform provides a fundamental mechanism to mitigate the risk of orphaned resources: co-ownership.
The primary owner is the user account initially associated with the app or flow upon creation, or the account to which ownership has been explicitly assigned. The primary owner has complete control over the resource – editing, sharing, deleting, managing connections, etc. Typically, this person builds the asset or is primarily responsible for its function.
The co-owner, on the other hand, is a user (or multiple users) granted the same level of control as the primary owner. They can perform all the same management actions. Think of a co-owner as a designated backup or partner in responsibility.
Why is co-ownership non-negotiable for business-critical assets? Having at least one co-owner is crucial for business continuity for any app or flow that supports a business process (i.e., not just a personal productivity tool). If the primary owner becomes unavailable (leaves, changes roles, or has an extended absence), the co-owner(s) can immediately manage, troubleshoot, update, or reassign the resource as needed. This prevents the asset from becoming orphaned and ensures the supported business process remains resilient. Relying solely on a single primary owner introduces an unacceptable single point of failure for essential solutions.
Permissions and capabilities of owners vs. users: Understanding the difference is vital. An app’s standard ‘user’ can run it, and a ‘run-only user’ of a flow can trigger it (if configured). However, only owners (primary and co-owners) can modify the app/flow definition, change its sharing settings, manage underlying connections, view run history in detail (for flows), and delete the resource. Co-ownership grants these essential management capabilities.
Best practices for proactive ownership management
Preventing orphaned resources requires a combination of clear policies, technical strategies, integrated processes, and user education.
Policy mandates
- Mandate co-ownership: Establish a formal policy requiring that all Power Apps and Power Automate flows intended for shared use or supporting business processes must have at least one active co-owner and the primary owner.
- Define criticality and ownership requirements: Classify applications and flows based on their business criticality. Highly critical assets might require multiple co-owners, ownership by a stable service account, and inclusion in formal disaster recovery plans.
Technical strategies
- Leverage service accounts/application users: For highly critical, long-running, or cross-departmental flows and apps (especially those performing background system integrations), strongly consider using dedicated Service Accounts (regular user accounts configured for non-interactive use, requiring licenses).
- Utilize Solutions: Encourage makers to build and package their apps, flows, connection references, environment variables, etc., within Power Platform Solutions. Solutions make managing and deploying across environments significantly easier, transferring ownership of all related components as a single unit. Ownership of solution-aware flows can be more easily managed.
- Employ a robust environment strategy: Segment development, testing, and dividing production workloads into different environments. Assign environment administrators and establish clear ownership expectations within each environment. Critical production solutions should reside in managed, dedicated environments with stricter governance controls – for more details on this, check out my blog post How to create a scalable Power Platform governance model for growing adoption.
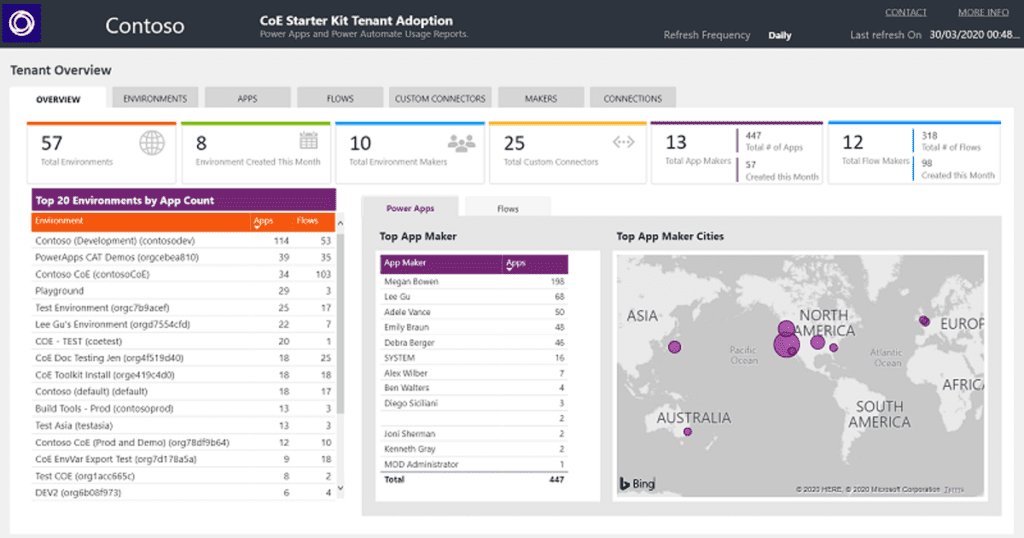
- Establish regular ownership audits and attestation: Use tools like the CoE Starter Kit or Syskit Point to audit the app and flow ownership regularly. Implement an attestation process where owners periodically confirm they still need and are responsible for their assets. This helps identify abandoned or potentially soon-to-be orphaned resources.
Effective ownership management relies on having the right tools to monitor the environment, identify risks, and take corrective action. Basic ownership with PPAC allows administrators with the necessary roles (e.g., Power Platform Admin, Dynamics 365 Admin) to view resources within specific environments. They can manually change the primary owner of an individual app or flow, which is crucial for rescuing already orphaned assets. However, this is often a reactive, one-by-one process. On an environment level, admins can provide lists of apps and flows per environment, showing the current owner. This is useful for spot checks but lacks aggregated reporting across the tenant. You can also use the Center of Excellence (CoE) Starter Kit, PowerShell for Power Platform Administrators (Custom Reporting and Automation Scripts & Bulk operations), or even Power BI (Custom Visualizations on CoE Data & Trend Analysis and Health Monitoring).
Building a resilient and well-governed Power Platform ecosystem
The Power Platform offers incredible potential for innovation and efficiency, but realizing its full value sustainably requires diligent governance. Orphaned applications and flows represent a significant, often hidden, risk that can lead to business disruption, security vulnerabilities, compliance failures, and wasted resources.
The core of the problem lies in the dependency on individual user accounts as owners. When individuals leave or change roles, their digital creations risk being abandoned without a clear path for continuity.
However, this risk is entirely manageable through proactive strategies:
- Acknowledge the Importance: Ownership is not an administrative afterthought but a cornerstone of responsible Power Platform usage.
- Embrace Co-Ownership: Mandate and enforce the use of co-owners for all non-personal Power Platform assets. This simple step provides crucial redundancy.
- Utilize Stable Ownership: Leverage service accounts or application users for critical, long-running, or system-level automations and applications.
- Leverage Tooling: Implement and actively use the Center of Excellence (CoE) Starter Kit, PowerShell for visibility, auditing, and remediation, or the Syskit Point.
- Educate and Empower: Train makers on their responsibilities and provide clear guidelines.
By implementing these best practices, organizations can move from a reactive stance to a proactive one. This ensures that the apps and flows driving business value remain supported, secure, and adaptable throughout their lifecycle, safeguarding the investment made in the Power Platform and fostering a truly resilient and well-governed low-code ecosystem. The time to establish robust ownership practices is now, before the proliferation of potentially unmanaged assets becomes an overwhelming challenge.


