Microsoft 365 compliance: Key concepts, questions, and answers
Table of contents
Getting Microsoft 365 compliance right means securing your business, safeguarding corporate reputation, and gaining a competitive advantage. Particularly now, with workforces more distributed, architectures more hybrid, and attack surfaces growing wider. That’s why Microsoft 365 offers a suite of tools to support you in ensuring compliance for the modern era.
Traditional IT management roles have moved beyond the perimeter, forcing governance to become agile, responsive and required to adapt and scale their compliance processes. Alongside these internal drivers, there are many government-led data-driven initiatives, and laws are continuously enacted or updated while considering human privacy rights.

What is Microsoft 365 compliance?
Microsoft 365 offers multiple components to help your business adhere to standards, policies and best practices for compliance and data governance.
These have been designed for different requirements faced by compliance teams today. From governments and regulators to strict industry-led standards typical within highly controlled industries such as financial services. Each administrative tool can help you build a plan for keeping your environment compliant while making sure users have the least-privilege access.
Common regulatory compliance frameworks
Europe’s GDPR was introduced in 2018, helping to align the previously divergent laws within member countries.
Since then, other regions have adopted similarly far-reaching legislative approaches. The US is currently evaluating the American Data and Privacy Protection Act, the first federal privacy law for the country.
Brazil’s LGPD came into effect in 2020 to unify 40+ data processing laws.
“By 2024, 75% of the global population will have its personal data covered under privacy regulations”
Gartner
Of course, legislative alignment at such a scale will take time.
The challenge for organizations — particularly those with complex architectures — is that compliance can’t wait. Even if the business is compliant, they also have to be able to demonstrate compliance to independent auditors. That means gaining the visibility to identify, monitor and show the necessary controls are in place and functioning correctly.
Here’s what some common frameworks require and how Microsoft 365 helps:
Microsoft 365 and GDPR
Organizations have to provide assurance that they have the necessary policies, procedures, and structures to process personal data. This includes responding to subject access requests, maintaining adequate security, and training staff. Microsoft 365 offers features around advanced auditing (including extended log retention), data classification (through automated labeling), and access management (covering all delegations, privileges, and operations).
Microsoft 365 HIPAA compliance
A central element of HIPAA is the requirement for entities to “ensure the confidentiality, integrity and availability” of patient data. This scope extends across all areas of the Microsoft 365 environment, covering safeguarding, permissioning, and protection. To support customers, Microsoft states, “Microsoft enables you in your compliance with HIPAA,” and has published this list of Microsoft Azure compliance offerings. Among these is the Azure firewall for managing inbound and outbound traffic and internet connectivity. Further layers of availability come from the option to deploy a scale set of virtual appliances behind the firewall for extra protection.
M365 and ISO 27001
A major challenge with ISO 27001 is being able to apply its standards across all your assets. Full visibility is essential, along with defined roles, responsibilities, and retention periods. Achieving this requires a framework that can be scaled and replicated wherever your data resides. To support Microsoft 365 compliance, Office 365 has annual audits against ISO 27001, and you can use the resulting certification for organizational assessments.
M365 and ISO 9001
This international standard covers multiple quality management principles, each requiring continual monitoring across the business. The Azure ISO 9001 certificate covers Azure, Dynamics 365, Power Platform, and some Microsoft 365 services. You can find the full list at the Service Trust Portal.
Good Clinical, Laboratory, and Manufacturing Practices (GXP)
For international life science organizations, GXP compliance can be a challenge. That’s because different countries have their own guidelines and regulators. This means multiple Microsoft 365 services are required to ensure data confidentiality, integrity, and availability. However, stringent enforcement by Microsoft means organizations using Azure can meet their GXP requirements. For example, they can meet certain regulations enforced by the US Food and Drug Administration (FDA) and the EU’s computerized systems.
Sarbanes-Oxley Act (SOX)
Organizational silos add to SOX compliance complexity, where reporting must align with finance and IT. This is exemplified by the requirement for reports to contain an Internal Controls report. Organizations have to validate financial statements as being accurate within 5% variance and show controls are in place to safeguard financial data.Of course, many institutions in the financial industry still maintain legacy systems. That’s why it’s worth viewing Microsoft Azure Guidance for SOX. In particular, the shared responsibility implications for workloads on-premises and cloud-based. This hybrid scenario also impacts Identity and Access Management, another key element of SOX compliance.
National Institute of Standards and Technology (NIST)
NIST has a five-function framework:
- Identify (risks to systems, people, assets, data, and capabilities)
- Protect (critical infrastructure and service delivery)
- Detect (when a cyber security event occurs)
- Respond (actions to take and how to contain the impact)
- Recover (plans for resilience, restoration and reviewing post-incident)Organizations are responsible for ensuring compliance with the relevant laws and regulations. However, help is available through Microsoft Purview Compliance Manager. This contains a template for building a NIST assessment. Alongside the template, Microsoft offers user and device authentication protocols through Azure AD and Conditional Access policy configuration.
System and Organization Controls (SOC)
SOC compliance is determined via third party audits. These are conducted on Microsoft 365 products (covering Azure, Dynamics 365, Power platform, and some online solutions) on a rolling 12-month basis. Audit reports and certificates are available from the SOC portal. You can download these and share them among partner organizations to demonstrate compliance. The reports examine Microsoft’s cloud systems and assess the fairness of descriptions of controls.
Cyber security Maturity Model Certification (CMMC)
The CMMS is a response to the increased complexity of cyber attacks within supply chains. The program is linked to the NIST framework and focuses on protecting sensitive information and intellectual property. Enactment is pending and expected sometime in 2023. Microsoft offers solutions to support compliance certification for organizations wanting to prepare now. These include Microsoft Government Community Cloud High. This cloud platform has US-based data centers to meet data sovereignty requirements. Microsoft staff working there must be US citizens and are subject to tight background checks.

Elements of Microsoft 365 compliance
The Microsoft 365 Advanced Compliance Suite will augment your Microsoft 365 compliance and data governance requirements. It includes Microsoft Purview, your starting point for data, security, and risk management. Microsoft Purview can also act as an automated element of any Data Protection Officer requirements.
Microsoft Purview
Microsoft Purview can cover your data estate end-to-end, including Teams, SharePoint, OneDrive, and Exchange.
You’ll need an activated Microsoft Purview account that’s been created in Azure. You’ll also need permission to access the governance portal: https://web.purview.azure.com/resource. From there, you can deploy Microsoft Purview solutions such as:
- Data Loss Prevention
Protects sensitive information and intellectual property stored in Office 365. - Information Protection
Identifies and protects sensitive data such as credit cards, bank accounts and passports. - Lifecycle Management
Classifies and governs data using labeling, retention, and event-based actions. - Message Encryption
Encrypts emails from within and external to your organization. - Communication Compliance
Mitigates risks from inappropriate communication by detecting, capturing, and remediating messages. - Customer Lockbox
Controls content using access authorization for your service operations. - Audit
Ensures visibility for audited activities and logs in your Microsoft 365 services. - Compliance Portal
Monitors your organization’s overall risk posture, with reviews and recommendations for actions, plus advanced compliance configuration options. - Compliance Manager
Displays a compliance posture score, alerting you to risks and areas that need improving. - Customer Key
Provides an added layer of encryption for your content through BitLocker and Distributed Key Manager. - Insider Risk Management
Checks for accidental or malicious signals and patterns relating to IP theft, data leakage and other possible security risks. - Information Barriers
Restricts communication between groups to prevent unauthorized sharing of classified information. - Privileged Access Management
Allows users to perform sensitive tasks based on a just-in-time Principle Of Least Privilege (POLP). - eDiscovery
Finds the data you need – at the source – with native search and collection.
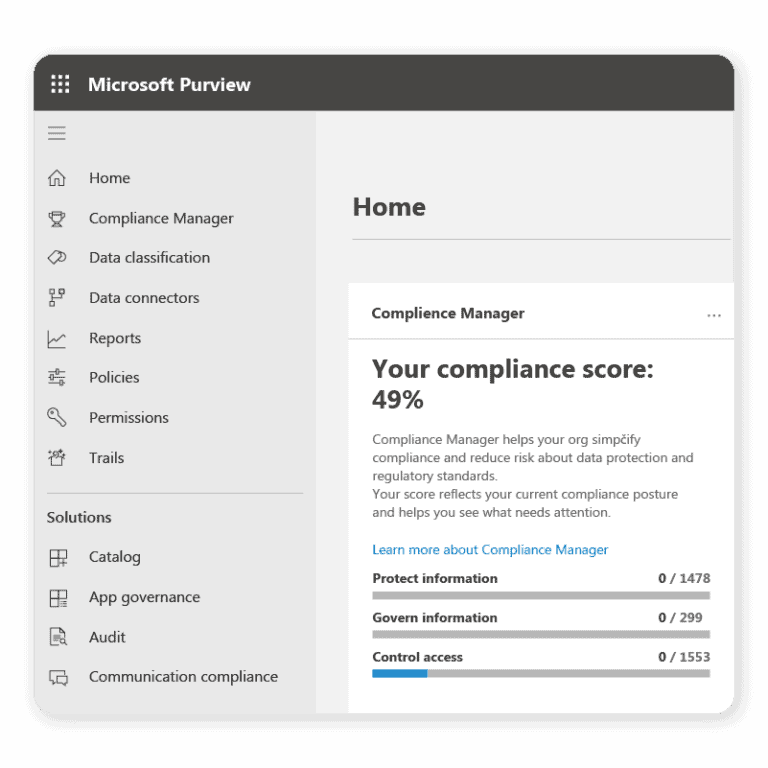
Microsoft Advanced Security Certifications
It’s a constant challenge to keep up with worldwide and industry-based compliance. That’s why Microsoft runs a variety of Governance, Risk, and Compliance (GRC) certifications. These range from Cybersecurity Architect Expert to Microsoft 365 Security Administrator Associate.
For cloud-oriented upskilling, the Azure Compliance Hub offers 100+ certifications. These span global regions, industry-specific regulations, and emerging government-driven initiatives. Options include Azure Security Engineer and the Azure AD-focused Identity and Access Administrator Associate certification. There are also how-to guides for compliance implementations and mappings.
SharePoint compliance
As digital estates grow in complexity, automation is becoming an increasingly crucial tool for SharePoint compliance. This is evident in how Microsoft has added auto labeling capabilities for detecting sensitive data. For example, automatically labeling SharePoint files containing credit card numbers. This data can also be automatically encrypted to ensure your organization fulfils storage compliance requirements.
For behavioral-based SharePoint compliance monitoring, there are also Microsoft 365 usage reports. These allow admins to view how employees are using services in the tenant.
Although when an employee leaves, deleting their account means their data usage is also deleted –within 30 days. So, it’s worth checking the relevant compliance and governance processes first.
Additionally, you may also need to adjust your privacy settings to view identifiable internal user details. Here’s how you can do that:
- Visit the Microsoft admin center.
- Click Settings > Org Settings. 3
- Click the Services tab.
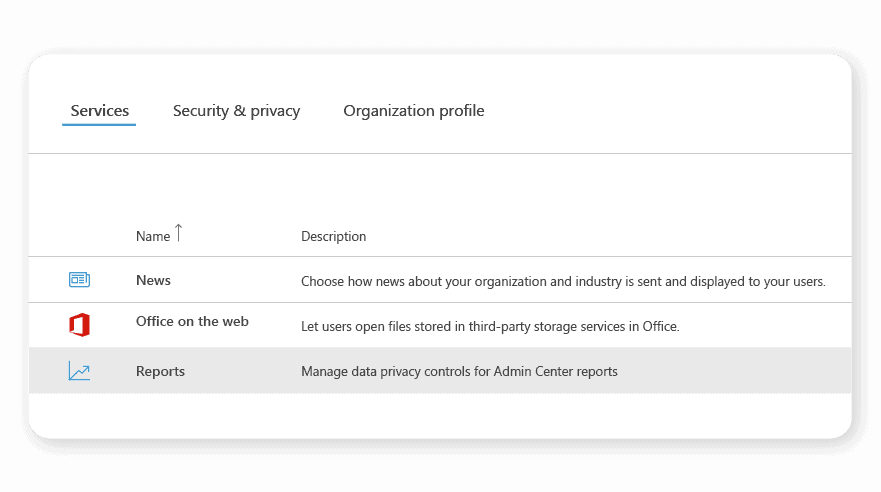
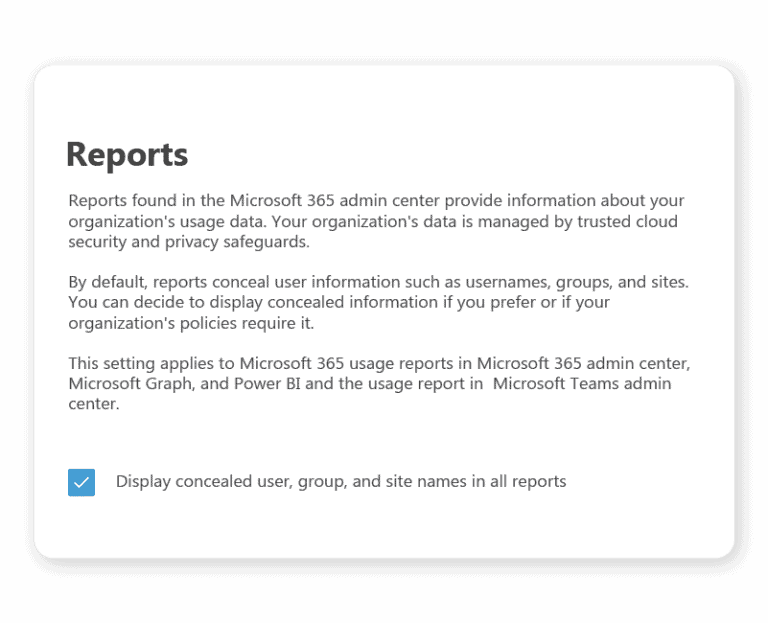
- Click reports
- Tick the box.

Microsoft Teams compliance
Admins can apply sensitivity labels and policies in the Microsoft Purview compliance portal. These are extended and enforced across Teams, Microsoft 365 Groups, and Microsoft Purview.
A use case would be labelling Teams to restrict control guest access, preventing external users from being added. Maintaining strict control of ownership will also help reduce the risk of orphaned channels in Microsoft Teams.
You can configure labels and policies at two levels:
- User-level
Apply policies at specific Teams users, or across the organization. - Teams-level
Apply policies to Teams channels, including Private channels.
Naturally, user-based compliance is at the heart of Microsoft Teams. All activities have to be logged for audit compliance. However, this also must be balanced with employees’ privacy around stored data logs, video calls, and other sensitive communication and collaboration content.

How to ensure Microsoft 365 compliance in your organization environment
Maximizing Microsoft 365 means mapping and unifying your data governance across on-premises, multi-cloud, and SaaS. Here are some key areas to consider within your environment:
Cloud storage and management
The need to set data retention policies is clear. However, things get more complex when you go deeper into data retention requirements.
With HIPAA, organizations must store and manage records for at least six years after the creation date. That’s relatively straightforward. However, HIPAA also requires these records to be kept six years after the “last effective date.”
This calls for high levels of visibility into the Microsoft 365 cloud environment to know when data is no longer used. Microsoft Defender for Cloud Apps can provide this across your connected apps’ activities. Through the Activity Log, you can uncover Shadow IT with comprehensive control over sensitive data.
Microsoft offers a 99.99% uptime guarantee with Teams. For the remaining 00.01%, organizations require outage backup scenarios to be put in place.
Today’s distributed and scalable ecosystems also need to have automated incident protection. One option is Microsoft Defender for Office 365. Its automated investigation and response capabilities (AIR) are augmented by investigation and remediation processes. These can take care of recognized threats while your team focuses on more high-level security demands.
Cloud security and auditing
Cloud access is business-critical – and so is access management. Azure offers both Role-Based Access Control and Identity Access Management, for managing, controlling, and auditing resource access.
Microsoft also recommends syncing cloud identities with any identities still based on-premises. You can do this using Azure AD’s hybrid identity solution. By creating and managing single identities in this way, hybrid enterprises can stay productive. Employees can collaborate with external third parties while mitigating security risks beyond the traditional perimeter.
Data leak prevention
This is one of the most vulnerable attack vectors, underscored by the fact nearly two-thirds (63%) of companies were breached last year. Now, combine this vulnerability with the growing volume of sensitive data flowing in and out of organizations. It’s clear organizations require similarly dynamic protection. That means policy enforcement – at scale.
Azure Information Protection (AIP) is built for this scenario. You can configure policies for classifying, labeling, and protecting data based on sensitivity levels and Personally Identifiable Information (PII). This can be automated or user-driven, with events viewed through one consolidated service. As with all Microsoft security and compliance solutions, access to AIP depends on your Microsoft 365 license.
Device management
For today’s hybrid organizations, device management is evolving as fast as industry legislation. Mobile devices, long-established since the days of BYOD (Bring your own device), are now joined by IoT devices, virtual machines, and other physical machines.
To protect these distributed environments, organizations require a robust device management solution. Many have turned to Microsoft Intune to secure their proprietary data, wherever it’s stored and accessed. What’s more, it’s possible to cloud-attach Intune to on-premises configurations. This unlocks cloud-based capabilities, such as conditional access and the ability to run remote actions (with Windows Autopilot).
User management
As an organization’s headcount increases, managing the tenant can quickly require extra resources. There can be more admins, a larger helpdesk, with more configuration support. Add in the global rise in remote working, and user complexity is magnified – just as visibility decreases.
Azure Active Directory (Azure AD) offers multiple ways to align and centralize user access. For hybrid environments, Microsoft recommends integrating on-premises and cloud directories.
Other best practices for managing users include tracking account creations and deletions. Accounts created and deleted within 24 hours should raise an alert. Alerts can also be triggered when non-approved users or processes create accounts. Privileged and non-privileged accounts should also be monitored, for users being assigned by non-approved users.
User and device compliance
This involves defining policies for tracking user access to resources and devices. These are the minimum requirement for an endpoint to connect to your systems. You’ll also need to decide whether policies should apply to devices or users.
Start by considering if you want a consistent device experience for every employee (such as for a specific mobile device). In this scenario, you could have policies apply to users. If the device type varies, such as a kiosk compared to a mobile card reader, device policies are often the best option.
You can manage compliance processes through Azure AD, for applications such as SharePoint, Microsoft 365, and OneDrive. It starts with creating definitions of normal and expected behaviors. Any violation can trigger an alert or action. To reduce manual effort, you can integrate Conditional Access to block users or devices automatically.


