The Microsoft 365 governance implementation checklist IT directors trust
Table of contents
Key takeaways:
- Effective governance is about driving accountability and business alignment in every department.
- Decentralized collaboration makes visibility and repeatable enforcement more important than ever in M365.
- The gap between written policy and real-world controls is where most audit failures and security risks occur.
- Automation lets IT shift from reactive troubleshooting to proactive oversight, freeing bandwidth for strategic work.
- Platforms like Syskit Point turn everyday governance evidence into a living record – making compliance continuous and provable.
Every IT Admin knows the importance of Microsoft 365 governance, but making an effective and clear action plan is a complex challenge.
Governance can often feel like a moving target. You’ve got auditors demanding evidence, policies lagging behind, and the risk of a compliance miss never far away. Without a structured plan, governance is a mess of disconnected settings, manual changes, unnecessary rising costs, and no documentation to back up big decisions.
However, there’s a better way! Our three-phased implementation lays a clear foundation and then builds in your controls, step-by-step. We’ll give you a roadmap to guide you through M365 governance, so you can take control of management, ensure nothing is missed, and have an evidence chain needed to demonstrate compliance.
The complete M365 governance implementation checklist
A strong M365 governance checklist pays dividends. Your processes will be better organized, there’s a lower risk of data loss, and you can approach audit season with confidence.
Implementing a clear checklist turns compliance into a practical system for safeguarding information, controlling costs, and keeping every department accountable.
Before you start: Strategy and alignment
- Define governance goals: Before diving into settings or policies, stop and define your “why?” To answer this question, bring together representatives from IT, Security, Legal, and any other key business units, including end users who will be your advocates on the ground. Discuss what drives your governance need – is it tightened security, sector compliance (think HIPAA, GDPR), or simply an improvement in day-to-day operations? Agreeing on shared goals keeps everyone invested and sets realistic priorities.
- Assess your current state: Audit your current Microsoft 365 setup. Which risks and gaps jump out? Are Teams’ settings open to guests, or are you drowning in unused SharePoint sites? An audit snapshot helps target problem areas, rather than spreading your efforts too thinly.
The combination of strategy, alignment, and assessment sets the stage for governance that actually works.
Phase 1: The foundation
Everyone wants the option of granular control, and foundation work sets the rules for real progress.
- Define roles and responsibilities: Spell out roles and responsibilities. Document who owns each service, and who approves access or leads department data decisions.
- Establish collaboration provisioning rules: Decide who can add new Teams, SharePoint sites, or Groups. Should these rights be open to all, or require approval from senior management? This is collaboration governance in action.
- Set your external sharing policy: Determine if content can leave the organization, and under what conditions. Blanket bans rarely work, so segment them by team or site for smarter protection.
- Create workspace naming conventions: Consistent names make audits, search, and cross-team work easier, while reducing confusion and clutter.
Phase 2: Implementation and security controls
Phase 2 is where the real work begins – transforming policy into practice and locking down risks in your Microsoft 365 environment.
- Configure sensitivity labels: These labels let you classify content (Confidential, Internal Use Only) and ensure every file has built-in protections, from encryption to usage restrictions. Aim for clarity in label names and keep the number of choices manageable for users.
- Implement Data Loss Prevention (DLP) policies: You’ll need to configure policies to auto-detect and block leaks of key data types, such as financial details or healthcare info, across all platforms.
- Configure conditional access policies: Go beyond password-only logins by introducing Multifactor Authentication (MFA) compliant devices, or trusted locations for sensitive resources.
- Secure privileged accounts: All Global Admins need MFA, and Privileged Identity Management (PIM) makes attacks harder and reviews much easier.
- Review and harden default settings: Default settings for key services like SharePoint and Teams may be too permissive for the needs of your business and wider industry. Adjust them to align with the levels of security required.
- Plan user training and communications: Position every new policy – naming conventions, sharing rules – as tools to help users work faster and find what they need. Adoption often hinges on framing security as a productivity win. Governance is ultimately a productivity benefit for users, so sell it that way!
Phase 3: Automation and continuous compliance
Continuous compliance starts with automation. The best-run M365 environments turn manual checks into automatic routines, removing scrambled review processes that leave teams exposed.
- Schedule workspace reviews: Regular workspace reviews ensure ongoing security and compliance. You can prompt workspace owners to periodically verify membership, external sharing links, privacy settings, and activity levels, helping to maintain oversight.
- Implement a workspace lifecycle and retention policy: Configure automated rules to archive or delete stale resources and ensure retention settings match industry compliance standards before anything disappears.
- Monitor for suspicious activity and policy violations: Monitoring is your insurance policy. Set up alerts for suspicious events – like unexpected external sharing, permission changes, or guest sign-ins – so issues are spotted before they become incidents.
Automation saves IT hours and ensures governance is a permanent shield, delivering reliable evidence for every audit. With the right tools, continuous protection is much easier to achieve than you might think!
For more granular information on managing M365, check out our Governance Handbook.
Download your M365 governance checklistFrom manual checklist to automated governance
By following our implementation checklist, you’ve built a rock-solid framework. But remember that the manual tasks in Phase 3 – regular access reviews, workspace lifecycle management, and monitoring – never truly end.
These are ongoing, labor-intensive, and fraught with the potential for missed steps, overlooked aspects, and human error. Access reviews are especially difficult. Reviewers often lack context or get overwhelmed by irrelevant requests, leading to stalled reviews and inconsistent documentation. Keeping up and providing evidence for auditors, drags IT into time-consuming tracebacks and documentation sprints.
“Moving these checks from spreadsheets and email chains to automated workflows is the only way to truly prove your policies are enforced – and to reclaim hours spent on tedious, repetitive governance tasks.”
Danijel Cizek, Product Manager Team Lead at Syskit
Native M365 governance tools
Microsoft provides a powerful suite of native governance tools for Office 365, with each serving a specific piece of the puzzle.

- Microsoft Purview stands out as the central hub for governance – covering data classification, retention, compliance management, and Data Loss Prevention (DLP) with robust policy controls and reporting features.

- Microsoft Entra ID (formerly Azure Active Directory) provides essential access reviews, group-based licensing, and granular permissions management. Essential for identity management and access control.

- SharePoint Advanced Management (SAM) is an add-on that enables detailed lifecycle and content governance in SharePoint and OneDrive, allowing IT to automate workspace policies specific to collaboration platforms.
“Remember – these solutions operate in isolation rather than as a unified system. IT teams still need to connect the dots by manually managing settings and workflows across admin centers, and piecing together audit trails from separate tools.”
Danijel Cizek, Product Manager Team Lead at Syskit
A fragmented approach consumes more effort than expected, making unified compliance and governance monitoring a major challenge for busy IT teams. The solution is found through automated governance.
Activating your checklist with Syskit Point
This is where your governance checklist goes from tasks on a spreadsheet to a fully automated compliance system!
Syskit Point acts as your always-on governance assistant by taking care of the heavy lifting, surfacing risks, and creating a provable audit trail.
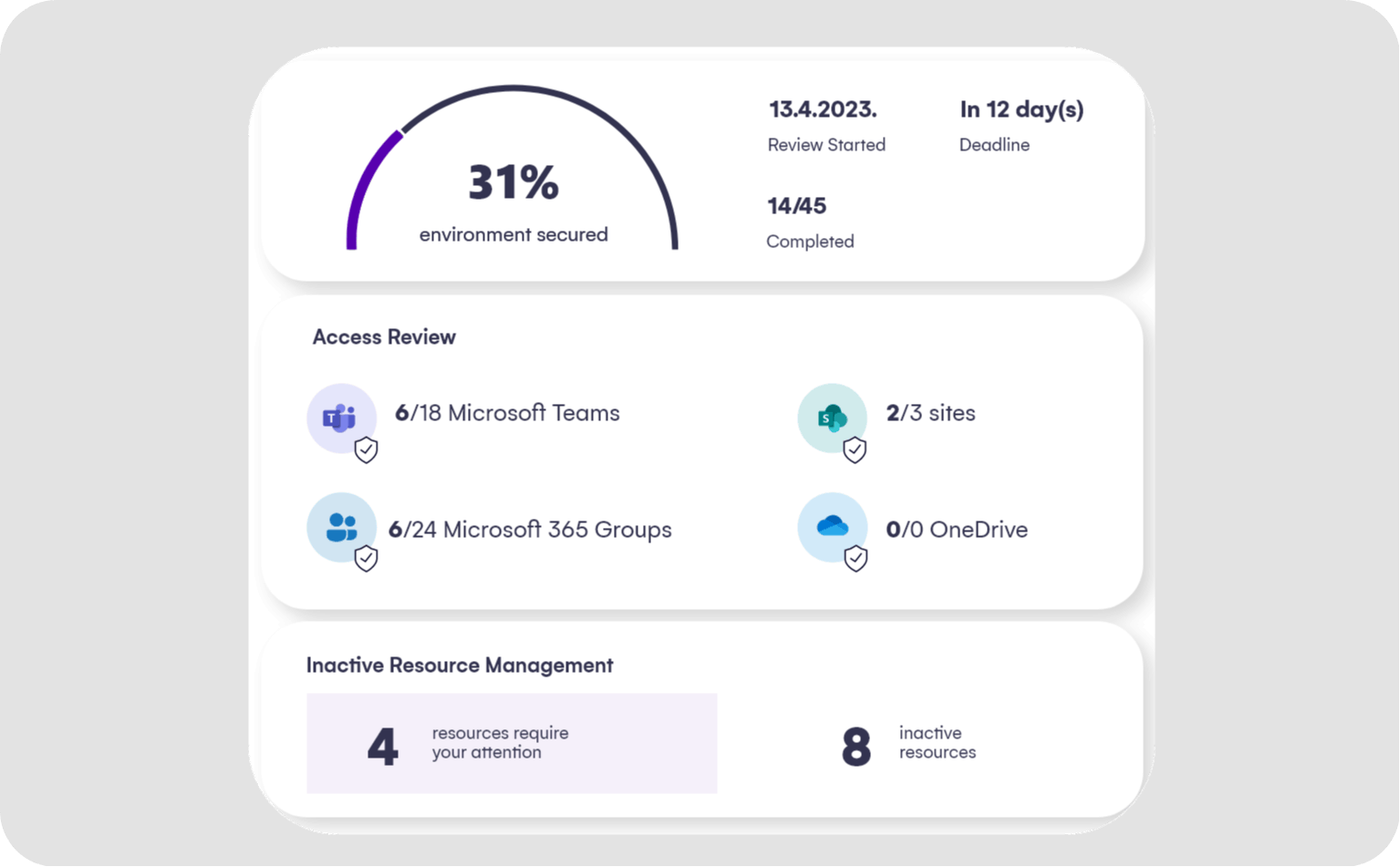
First, Syskit Point automates workspace reviews across your Microsoft 365 estate, extending oversight beyond simple permissions to include sharing links, privacy, sensitivity, and inactivity checks. Built-in scheduling and customizable review templates let organizations set policies for every workspace, so access is always up-to-date and documented. Owners receive targeted review tasks when it matters most.
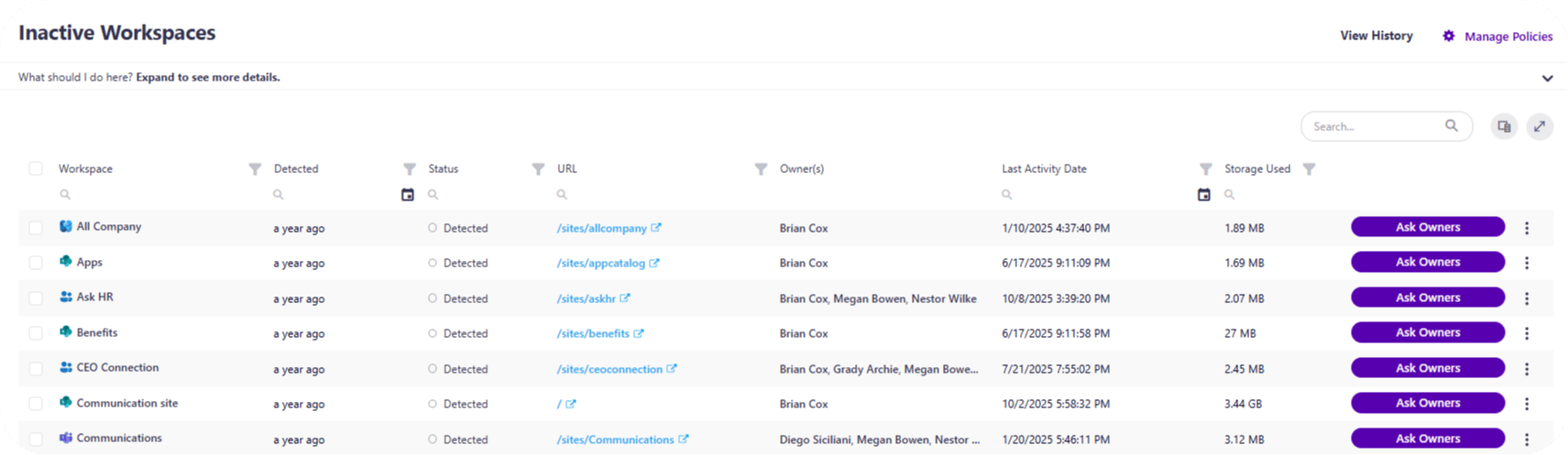
Next, Syskit Point manages the workspace lifecycle efficiently. Inactive Teams, Groups, or SharePoint sites are detected based on your defined policy. You can trigger archival or deletion actions, cutting through sprawl and reducing the risk of forgotten ghost teams with stale access.
But automation doesn’t stop there: Syskit Point’s alerting engine vigilantly monitors for suspicious behavior and policy violations – like unauthorized external sharing or privilege escalations – giving IT teams and business owners rapid insight and proactive control.

You’ll receive instant granular alerts about unlabeled workspaces, security and compliance vulnerabilities, the number of inactive M365 licenses at your disposal, and more.
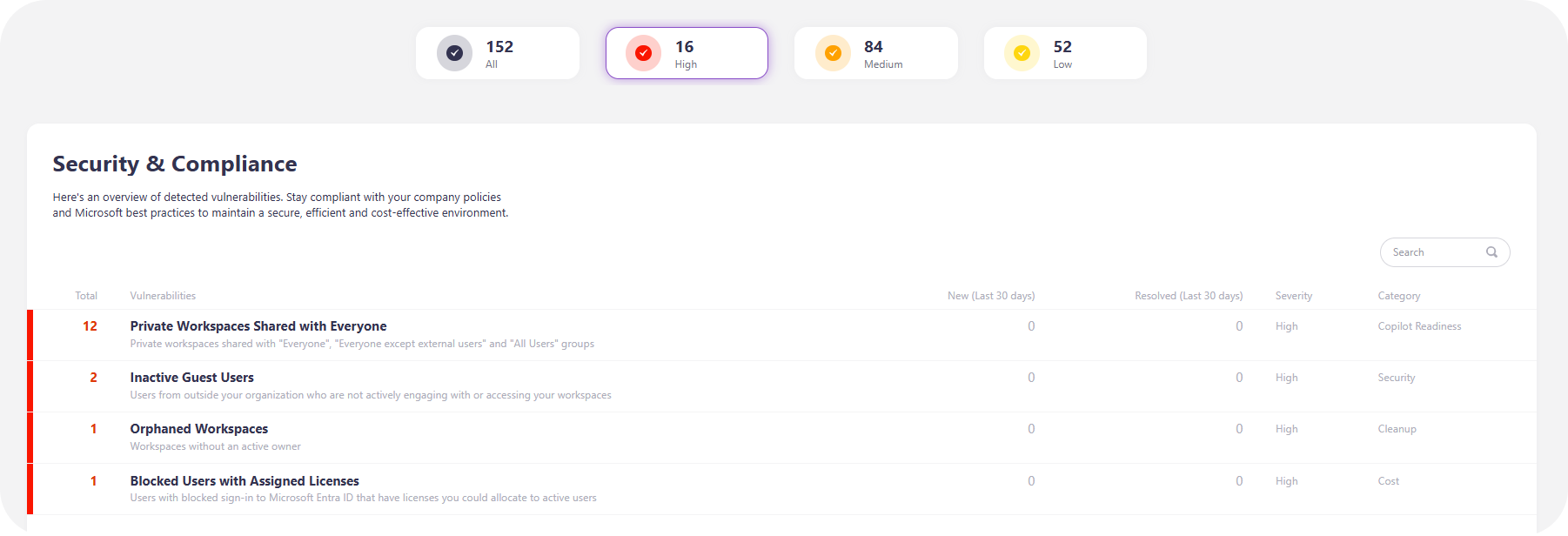
Most importantly, Syskit Point turns your governance program into proof. All activities – access reviews, policy enforcement, lifecycle events – are recorded, timestamped, and exportable. For every audit or executive review, you now have centralized evidence, and no need for manual monitoring. For further info, browse through our Microsoft 365 Governance Handbook.
Move to continuous compliance and governance you can prove
Effective M365 governance is a system with clear phases and repeatable actions. Although governance differs from one user’s needs to the next, a proper checklist transforms the theory into a workable process, replacing guesswork with confidence. But even the best manual plan still leaves too much to chance and consumes far too many hours.
Automation is the secret sauce. It shifts governance from periodic chores to continuous, provable compliance, where every protective control generates its own evidence. Users gain efficient, auditable, and secure operations all year round.
If you’re ready to turn your governance checklist into an automated compliance machine, see how Syskit Point can help you secure your M365 environment and simplify your next audit.