Top 10 Office 365 best practices every admin should know
Table of contents
These best practices are primarily focused on SharePoint, OneDrive, Groups, and Microsoft Teams workloads, so they may differ if you are primarily using one of the other workloads in Office 365.
1. Enable Office 365 Multi-Factor Authentication (MFA)
This is a no-brainer for every install and is not turned on by default. Office 365 multi-factor authentication adds one additional layer of security as it is increasingly more difficult for an attacker to compromise multiple authentication factors.
In Office 365, you can enable and further enforce MFA for your users. There are multiple methods of how users can authenticate, including a mobile app, text messaging, or calling. For apps that do not support MFA, you can create app passwords. MFA works flawlessly with Microsoft Office and web browsers, and you can even use it when connecting to Office 365 from code or PowerShell.
To enable MFA, navigate to the Microsoft 365 Admin Center > Users > Active Users, click on one of the users, and click on “Manage multi-factor authentication” on the user properties screen.
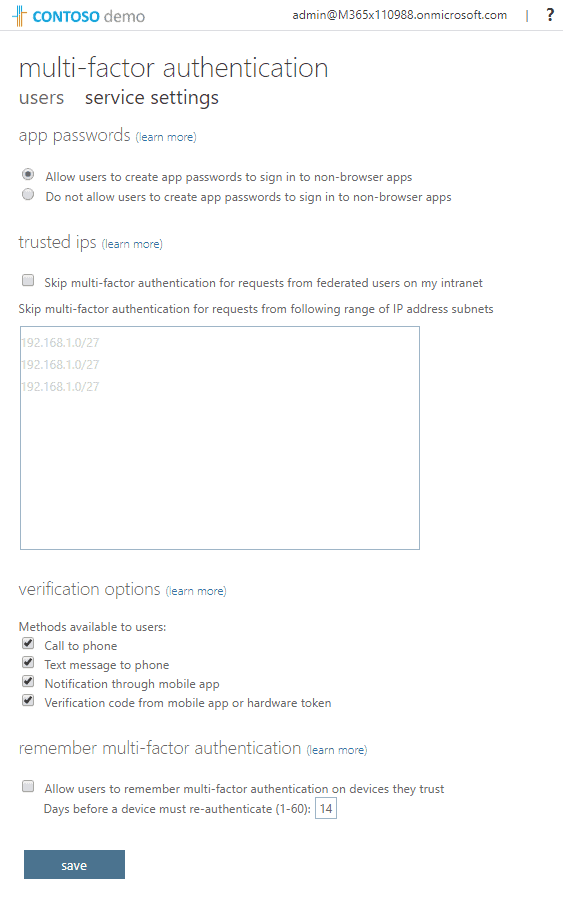
To learn more, navigate to How it works: Azure Multi-Factor Authentication.
There are a couple of things you should consider before enabling MFA. There have been a number of disruptions in the last 12 months, so you need to monitor the status of Office 365 services closely to ensure the system is up and running.
The best practice is to ensure all your privileged users have MFA enabled, including Global Admins. However, it would be best to consider having a break glass account that could still log in when MFA is down so you can temporarily disable the service.
2. Configure Office 365 company branding
Company branding allows you to customize the default Office 365 login pages with your company branding and images. One of the primary reasons is that your users will feel secure that they are on the right page where they are supposed to enter their credentials instead of some fake phishing page.
Branding can be configured from the Azure Active Directory Admin Center > Manage > Company branding. To learn more, navigate to: Add branding to your organization’s Azure Active Directory sign-in.
3. Redirect Windows common folders to OneDrive for Business
End Users love to store important documents in their Desktop or My Documents folder, and IT departments have struggled with this situation for a long time. Now, OneDrive for Business is an ideal solution for this problem. IT can enforce redirection of these folders to OneDrive using Group Policy. On the other hand, nothing changes for the end user. They can still use their folders exactly as they’re used to, while in the background, the OneDrive client will sync the files with the cloud.
To learn more, navigate to: Redirect and move Windows known folders to OneDrive.
4. Enable mobile application management for OneDrive and SharePoint
If your organization is using Intune, you can further manage content users are syncing to their phones. Let’s face it, it’s great that we can have our files on the go, but controlling that can be a pain. With these mobile device management policies, you can control how files are synced to your mobile apps.
Learn more in the OneDrive Admin Center > Device Access.
To learn more, navigate to Control access to features in the OneDrive and SharePoint mobile apps.
5. Understand, configure, and manage external sharing for OneDrive and SharePoint
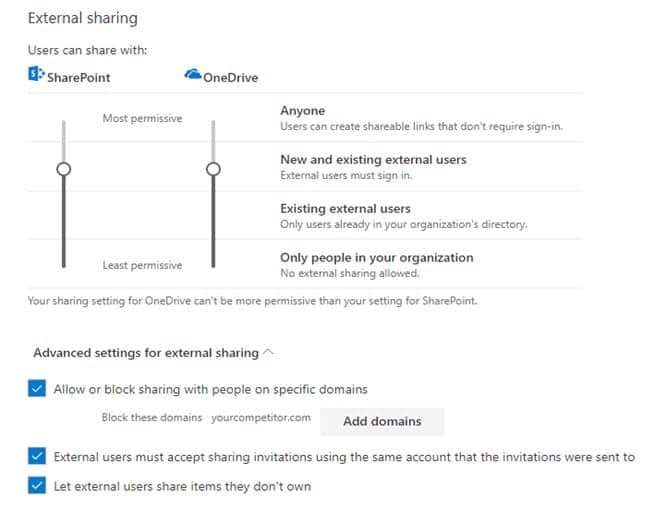
Both OneDrive and SharePoint include a handy feature that allows end-users to easily share documents with a user not part of your organization and, if permitted, even with fully anonymous users. While this feature is probably great for many organizations, it is still advisable you spend some time thinking about and configuring External Sharing settings for Office 365 workloads. E.g., While anonymous sharing links might be okay for some organizations, this could spell disaster for others. Jump into the OneDrive or SharePoint Admin Center to adjust settings for your tenant. Learn more in our External Sharing blog post or the official documentation. Manage sharing in OneDrive and SharePoint. It is the best practice to regularly review these settings and adjust them to your company policies and new features released by Microsoft.
6. Configure Office 365 Auditing
As soon as you have your tenant up and ready, you should jump into the Office 365 Security & Compliance Admin Center > Search > Audit log search to ensure that auditing has been enabled for your organization. To learn more, navigate to Search the audit log in the Security & Compliance Center. It might take up to a couple of days until the logs start appearing in the UI, so make sure you have done this way before there is a business request to look into some logs. These logs are comprehensive and cover various workloads, including but not limited to Exchange, SharePoint, and OneDrive activities.
Learn more about how Syskit Point enhances Office 365 auditing functionalities.
7. Review Secure Scores
In the last couple of years, Microsoft invested heavily into a couple of dashboards that check your tenant configuration against the latest best practices. For some metrics, you will get an immediate fix; for others, you will get a detailed checklist on how to remedy this potential problem. As these are continuously evolving, it is advisable to review them regularly. The Microsoft Secure Score is in the Office 365 Security Admin Center.
8. Check access to critical admin sections
Office 365 administrators should periodically check the users with privileged access to the Office 365 system. This includes members of the Global Administrators role, but also specific workloads administrators like Exchange administrators, SharePoint administrators, and User management administrators. For SharePoint, you should also periodically check who owns a particular site collection, and for Office 365 Groups and Teams, who are the owners of these groups?
Try Syskit Point for easy-to-read reports that help check access to critical admin sections.
9. Phishing Check
Email phishing attacks are causing billions of dollars in lost revenue for companies each year. Office 365 has a number of tools in place to prevent these emails from ever getting to your end users, and you should make sure that these are enabled and configured for your tenancy. Recently, I have found one “small tool” very useful in measuring your organization’s and its users’ maturity. The tool is called Attack Simulator in Office 365, and it allows you to start a fake phishing attack on your users. With its built-in reports, you will be able to pinpoint users more vulnerable to real phishing attacks and further educate and secure them.
10. Preventing Office 365 Groups and Teams from going stale
Allowing everyone to create as many groups as they want will soon become unmanageable chaos, and it takes so little to prevent it. Here are some simple best practices to avoid this mess:
- Define a subset of users who are allowed to create groups
- Define expiration policies for groups
- Check groups for activities to detect potentially stale ones
- Make sure groups have more than one owner


