Office 365 guest users cleanup
Table of contents
External collaboration is an integral part of our everyday work, yet it may bring many challenges, especially when it comes to ensuring it remains secure for both parties.
Collaborating with vendors, partners or customers frequently requires you to share your company data with someone outside your organizational domain. There are multiple and quite easy ways to add or create a guest user in your environment using Azure Active Directory, Microsoft Teams, and Microsoft 365 Groups, as well as SharePoint Online.
One such way is to do it through Syskit Point‘s Security and Compliance Checks dashboard, which lets you see a list of all users that have not been active for a period of time defined by you.
The Inactive Guest Users screen opens, showing a list of all users that have not been active for a defined period of time.
To ensure a high level of security, you must educate your users and ensure that guests and external users have access only to the necessary data. Also, you should build a proper mechanism to regularly review them and restrain their access from your tenant.
History of Office 365 guest users
Before we continue, one thing worth emphasizing is that Microsoft uses the terms guest user and external user interchangeably, which may create confusion. External user is an older term from back when all “guests” in the directory authenticated outside of the home tenant.
When they added support for managed guest users (i.e. the user that authenticates inside the home tenant), the “external” part stopped making sense, and “guest user” was born. As with many situations, Microsoft ended up using both names to refer to the same set of features.
Office 365 guest users and ad hoc external users
To get us started, let’s first revisit that there is one more type of external collaboration – ad hoc external access in Office 365. Guests and ad-hoc external users are both users outside your domain, but their settings provide different functionalities and restrictions for a person who is getting access to your environment.
- Guests – a person added to your organizational Azure Active Directory who needs to authenticate to access teams/groups and data. They can be added to a team or a group, and in that case, they can chat, meet, call, and share and collaborate on files like any other native member of the team.
- Ad hoc external users – a person who is not registered in your Azure Active Directory and is from another domain. They log in using time-sensitive one-use codes to gain access to your organization’s assets. This person cannot see any other file except the one that has been directly shared with them. This user cannot become a team member but can still be added to 1:1 meetings and chats.
You can check the full list of differences. There has also been a change in default Microsoft Teams settings regarding guest access, so make sure to revisit how your organizational setting is currently configured.
Managing and detecting Office 365 guest users access
Accumulating guest/external users in your environment presents a security concern that we must be aware of. Any unattended account may result in a breach, so it is important to always keep an eye on who is invited to your tenant, renew their access if needed, or remove if this collaboration has ended.
It would help if you kept an eye on ad-hoc sharing because these users can access your data, and are not registered in your AAD, making them much harder to track.
So, what is the easiest way to detect and manage all guest users in your environment?
Detect and remove Office 365 guest users using the admin center
- Navigate to https://admin.microsoft.com/
- Open users –Guest Users dashboard
You will get a complete list of all registered Office 365 guest users in your tenant. You can also easily add new Office 365 guest users and remove guest user accounts directly from here.
Detect and remove Office 365 guest users using the Azure portal
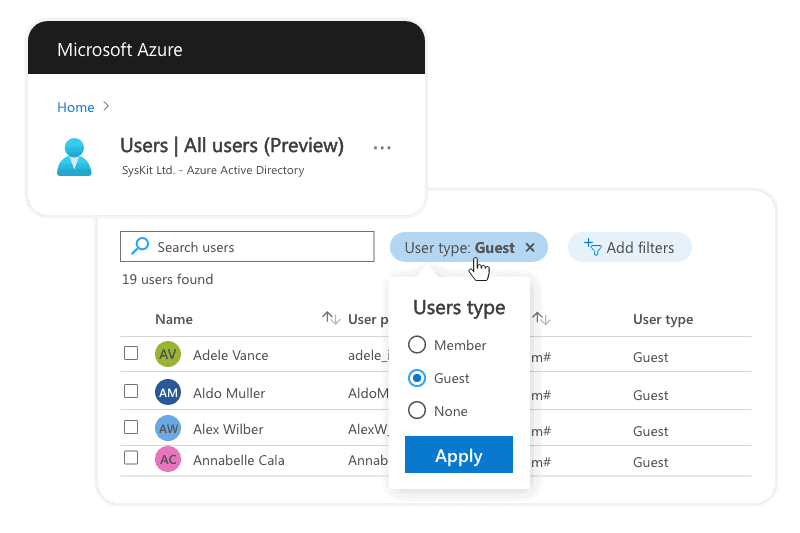
- Go to Azure portal
- Open Users Dashboard
- Create a User type Filter and select Guest as filter value:
- And you will see your Guest users as it is shown in the next picture.
- On this screen, you can manage and delete Guest users.
Detect and remove Office 365 guest users using PowerShell
We can distinguish guest accounts from normal tenant accounts in a few different ways. First, guests have a User Principal Name constructed from the email address in the form:
username_domain#EXT#@tenantname.onmicrosoft.com
For example:
Megan_microsoft.com#EXT#@contoso.onmicrosoft.com
Second, the account type is “Guest,” which means that we can filter guests from other accounts with PowerShell as follows:
First, check your Gest Users using the following script:
Get-AzureADUser -Filter "UserType eq 'Guest'" -All $true| Format-Table Displayname, MailYou can delete multiple Office 365 guest users using this script, and applying some filter, in example we will filter by domain, we want to remove all guest users from contoso.com domain:
$Users = (Get-AzureADUser -Filter "UserType eq 'Guest'" -All $True| Select DisplayName, UserPrincipalName, ObjectId) >> ForEach ($U in $Users){ If ($U.UserPrincipalName -Like "*contoso.com*") {Write-Host 'Removing'$U.DisplayName Remove-AzureADUser -ObjectId $U.ObjectId }}Detect and remove using Microsoft Graph API
To detect Office 365 guest users:
- Navigate to the Microsoft Graph Explorer using ms/ge
- Then login to the tool using the button called Sign in with Microsoft.
- Select GET operation.
- Select any version v1.0 or beta from the Request dropdown
- Enter the below Microsoft Graph API endpoint:
https://graph.microsoft.com/v1.0/users?$filter=userType eq ‘Guest’ - Make sure you consent to the requested permission scope:
ReadBasic.All, User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All, Directory.AccessAsUser.All - Click the Run Query button.
- Under the Response Preview, we can see all the Office 365 guest users added to your tenant.
- Copy any of the User Ids from the response. We must use that ID to remove it from the list.
Now when we know who our guest users are, we can also delete them if necessary, using Graph Explorer:
- Select DELETE operation from the operation dropdown,
- Select any version v1.0 or beta from the Request dropdown
- Enter the below Microsoft Graph API endpoint and replace <userId> with the real userId you got from the previous request. https://graph.microsoft.com/v1.0/users/<userId>
- Ensure the below permission scope is consented to,
AccessAsUser.All - Click the Run Query button. Now the requested guest user is removed from the tenant.
Configure regular Azure AD access reviews
Use the Microsoft guest access reviews feature to regularly remove inactive and no longer needed Office 365 guest users from your tenant. Once you configure it, reviewers will receive email tasks directly to their inbox to review if a guest user is still needed or not.
- Sign in to Azure Portal as a Global administrator or User administrator.
- Open Identity Governance –> Access reviews -> New access review.
- Select Teams + Groups to review user memberships to Teams and Groups.
- Choose “All Microsoft 365 groups with guest users “. You can also exclude some groups that you do not wish to have reviewed.
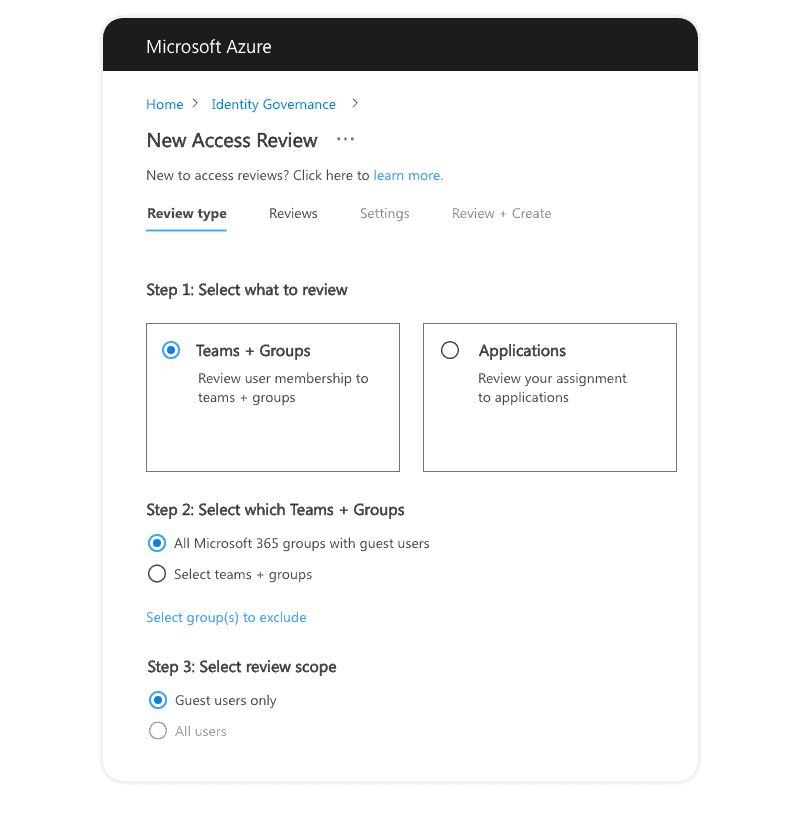
- Select who the Reviewers are – group owners or selected users (guests themselves, managers, or some third person).
- You can also easily configure the frequency and start date.
- There is an option to specify automated action after the review period has passed and the designated reviewer hasn’t performed his task. The system provides some recommendations as well and suggests which users to remove, which should stay.
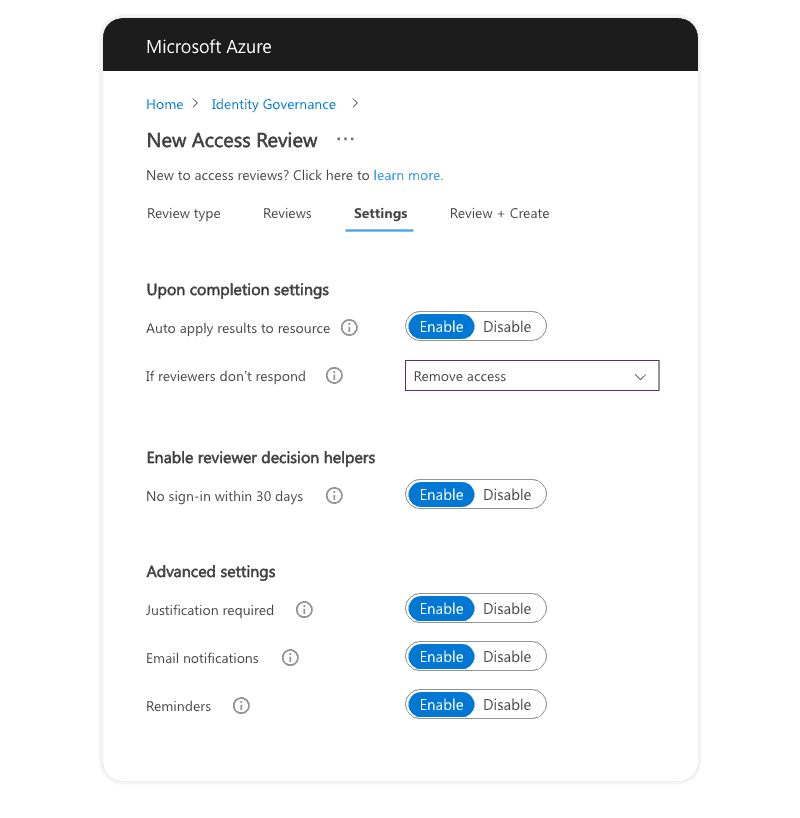
- After you click Create, you await review tasks on the date that you specified.
Things to have in mind:
- For this feature to work, you will need Azure AD P2 or EMS E5 license for every reviewer included in this process. In most cases, this will include all group and team owners, which can be a substantial number. Read more details on licensing requirements.
- This does not detect users outside your domain that have gained access through external ad hoc sharing. This happens when you share only individual files/folders and not the entire site/group/team, and they are not registered in your Azure AD.
- Emails are not customizable, and you cannot add your company branding or additional info for your reviewers.
- This covers only group and team guest users. Your SharePoint Online sites and OneDrive are still unguarded, and guest access will not be regularly reviewed.
Detecting ad-hoc sharing
There is no out-of-the-box reporting to help you gain better visibility of ad-hoc sharing. You can detect that only by revisiting access to each file.
The best prevention method is limiting external sharing settings allowed on your sites, teams, and groups to Existing guests and by limiting which domains can access your environment.
Automate guest management with Syskit Point
Syskit Point is an Office 365 governance solution that helps you gain visibility and control over your teams, groups, OneDrive, and users. It automates reporting and most important governance processes and provides detailed inventory. It is created for admins and business owners
Detailed yet simple user reporting displays a complete inventory of all Office 365 guest users and ad-hoc external sharing in two quick clicks.
External Users
This Syskit Point report gives you a complete list of all guests and ad-hoc external users who have access to your Microsoft Teams, groups, and sites. Apart from bulk remove action, if you select any of the Office 365 guest users Point will provide you with additional information such as who added this user and when.
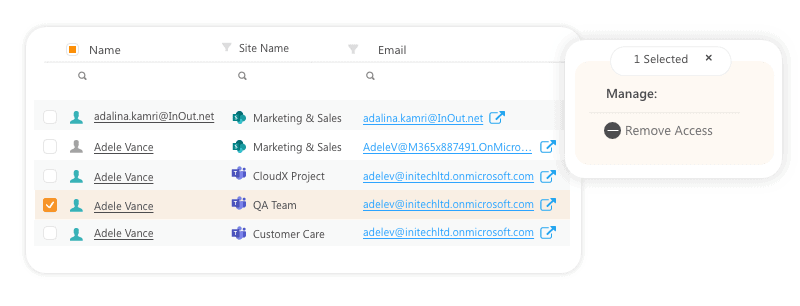
Using the User Activity report, you get a detailed audit log of all actions performed by this user in your environment for more than 90 days.
If you wish to see more details on where this user has access to, especially for those ad-hoc sharings, use the User Access report and detect all shared sites, teams, and groups down to a document level.
External Sharing
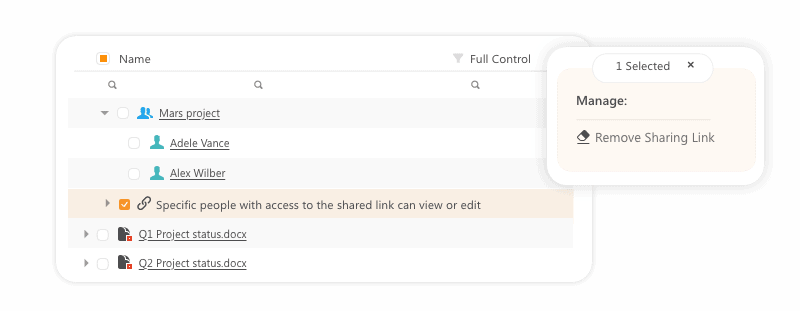
Use this report to detect all externally shared company content and manage external access in real-time directly from the Point interface. The report is highly visual and can be easily shared with data owners as well.
Manage guests’ permissions or remove sharing links that are no longer needed in a matter of seconds.
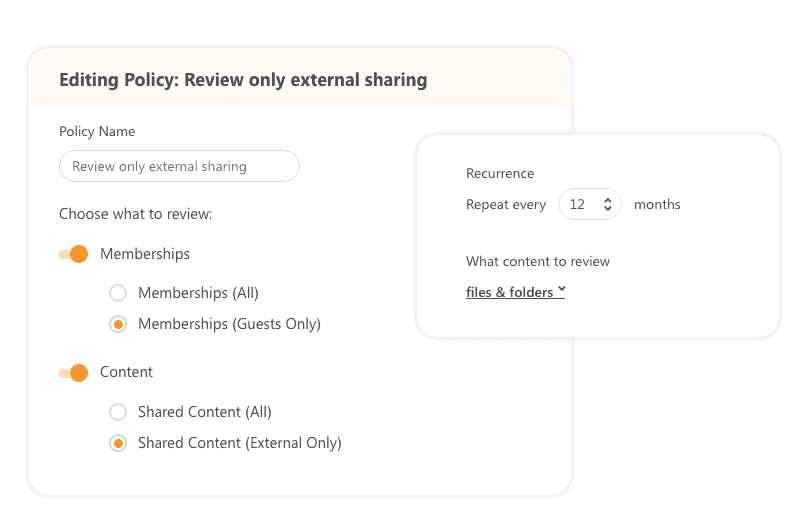
Syskit Point Access Reviews
With this feature, you can schedule periodical reviews of all external sharing in your company. Using Syskit Point, you can choose two review options. The first one is to recertify only group/team memberships – owners, members, and guests added through AAD. Second one is to audit all external sharing, including ad-hoc users who are not registered in your Azure Active Directory.
This feature is available for Microsoft Teams, Office 365 Groups, SharePoint Online, and even OneDrive sites.
We also enable you to customize and add company branding to those emails, making them more user-friendly and reliable for your end-users. A simple wizard guides them through the process and helps them become a vital part of your company governance compliance.
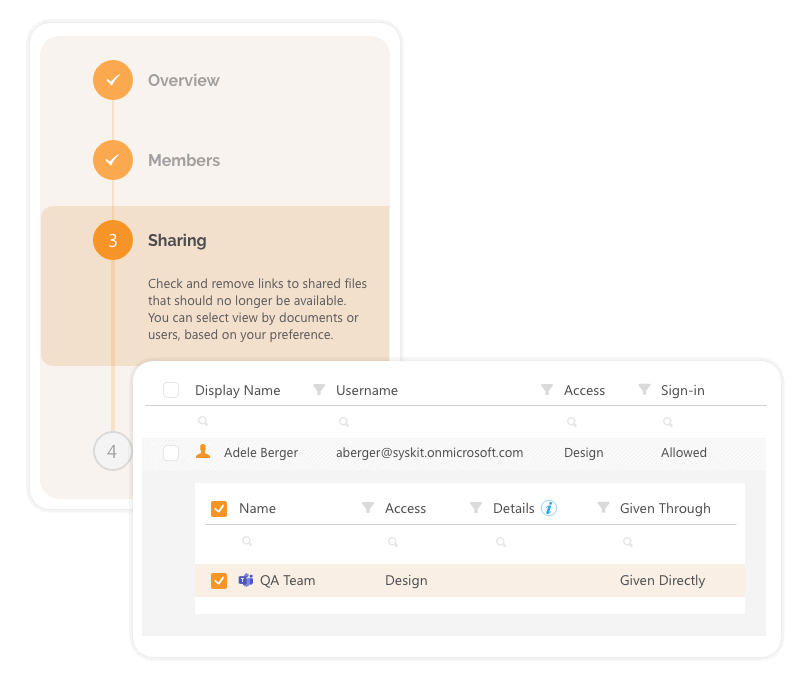
Guest Governance Policies
Our development teams are already working on delivering additional options to keep control over guests and external sharing. With Syskit Point’s new external expiration policies, you can define the external user inactivity after a specified number of days. After a user becomes inactive, Point will regularly check for all inactive external users and offer cleanup actions. You choose the reviewers, and in case that no one takes responsibility for these users, Syskit Point can automatically remove them for you.
How Syskit Point helps you with inactive Office 365 guest users?
As we mentioned, inactive guest users can present a security risk. It’s a best practice to remove them once collaboration with them is finished to prevent risk, reduce clutter, and simplify user management. This is why we’ve added the ability to automate guest user recertification to keep your environment clean, secure, and manageable.
It is accessibly through the Security & Compliance Dashboard, along with other handy features.


