Microsoft Teams governance guide to lifecycle management and data security
Table of contents
Key takeaways:
- Strong governance is about balance – enabling users while controlling sprawl, risk, and redundant workspaces.
- Regular reviews and clear ownership ensure Teams stay current, secure, and aligned with business goals.
- Lifecycle policies and naming conventions stop chaos before it starts, reducing both IT headaches and user confusion.
- Proactive governance evolves as your Teams environment grows, so adapting policies is key to long-term success.
- When complexity outpaces manual tools, platforms like Syskit Point give IT teams the automation and visibility needed for true oversight.
Adopting Microsoft Teams without a plan of action can quickly bring chaos, with admins trying to manage inactive teams, duplicate channels, and forgotten files. Across more than 360 million monthly users worldwide, Teams is an excellent tool for modern collaboration, but a lack of proper governance turns it into digital clutter.
This clutter isn’t just annoying for your IT people. The rise of AI tools like Microsoft Copilot adds further complications, leading to more oversights and business compliance risks. Governance is actually the rulebook that restores order and clarity – allowing you to gain all the benefits of Teams and avoid any heartache.
This guide offers a practical, two-phase plan, starting with native controls, then scaling securely with automation and Syskit Point’s Teams app.
What is Microsoft Teams governance and why does it matter now?
Microsoft Teams governance is a set of policies, roles, and structured processes that gives IT control over how Teams are created, named, accessed, and decommissioned.
For admins, governance is about moving from chaos to clarity. It prevents the classic scenario where anyone can create a Team for anything, resulting in a confusing jungle of duplicates, half-completed projects, and forgotten chats. Sprawl – the uncontrolled spread of abandoned or duplicate Teams – makes it hard for users to find what they need, wastes IT time, and increases security risks.
Well-designed governance puts practical controls in place. It keeps outsiders from wandering into sensitive workspaces by managing guest access and ensures data doesn’t leak beyond its intended recipients. Policies clarify who can access what, reducing security headaches and making compliance reviews less stressful. Governance also stops Teams from becoming ‘ownerless’ when people leave, so every group always has somebody responsible for managing it.
A predictable Teams layout, guided by naming conventions and standard templates, means users spend less time searching and more time collaborating. A clean structure raises user adoption and drives better business outcomes.
It’s important to know that every Team in Microsoft Teams is ‘backed’ by a Microsoft 365 Group, which comes with a SharePoint site for files, a team calendar, shared mailbox, and more. Governance policies, such as naming or expiration rules, are usually set at this Group level, meaning a decision here shapes everything attached – channels, files, and permissions alike.
Your foundational governance phased plan
Rolling out strong governance is easier when you have a checklist. A phased plan starts with Microsoft’s built-in controls, then scales with automation when things grow complex. Think of it as your blueprint for a secure, well-organized Teams environment that keeps users productive and IT stress low.
Phase 1: Establishing foundational control
Take the time to get the basics right – after all, you’re building a foundation for the future.
Define key roles and responsibilities
Assign clear roles for accountability. The M365/Teams Administrator creates and enforces governance policies. Team Owners manage team membership, guest invites, daily moderation, and renew teams when prompted. Team Members collaborate within established guidelines. This separation ensures ownership of day‑to‑day actions and keeps Teams manageable as your environment grows.
Control who can create new teams
Letting anyone create teams fuels growth, but also triggers duplication and sprawl. But restricting team creation too much creates workarounds.
The solution is to use Microsoft Entra ID to limit team creation rights to a dedicated security group (managers, project leads, or M365 Team Creators). This keeps a balance between flexibility and order, directly supporting both adoption and control.
Implement a team naming convention
Consistent naming keeps Teams easy to find and avoids duplication. For best practice, use a template like:
Team_[Department][ProjectName][Region], for example, Team_Finance_Q4Budget_US.
Enforce this with Microsoft Entra ID P1 naming policies. These ensure every team name follows the standard and adds meaning.
Remember, the Team display name is easy to update, but underlying elements like the SharePoint site URL and group email stick forever, so avoid future confusion by getting names right upfront. A good naming policy for Microsoft Teams includes prefixes (HR, FIN, IT), project identifiers, and region codes to boost clarity and searchability.
Set your guest access policy without blocking collaboration
Guest access is a critical security lever. Control it globally using the Teams Admin Center, and enable or disable guest access for your tenant. Once enabled, Team Owners can add guests unless sensitivity labels or other rules apply.
“It’s recommended to keep global access enabled, but give Team Owners responsibility for reviewing and removing guests regularly. This balance keeps collaboration open but protects sensitive data from external leaks. Document your guest access policy, educate users about their responsibilities, and schedule periodic access reviews to keep things in check.”
Danijel Cizek, Product Manager Team Lead at Syskit
Deploy teams templates to prevent governance debt
Manual team creation invites risk – unstructured workspaces, missing security settings, and rogue apps. For a native solution, you can configure standardized templates in the Teams Admin Center for common scenarios. Here are three templates to start with:
- Project: Includes channels for Planning, Resources, Deliverables, built-in Planner tab, 6‑month expiration.
- Department: Channels for Announcements, Resources, Internal sensitivity label, no guest access.
- External collaboration: Guest access allowed, limited app permissions, 90‑day access review cycle.
While expiration and access review policies are configured separately in Microsoft Entra ID, you can build a business process where all teams created from a specific template are then manually or automatically added to the corresponding Entra policy.
While native templates provide a good starting point for standardization, many organizations find they need more control. For more flexibility, customizability, and a user-friendly experience, use Syskit Point to organize requests, assign templates, and automate policies, giving admins more control and reducing operational headaches.
Phase 2: Managing lifecycle and data security
Once foundational governance is in place, the next step is lifecycle management – the process of keeping Teams current, compliant, and secure as they evolve.
This phase focuses on automation – cleaning unused workspaces, preserving business records, and applying consistent security rules so Teams don’t quietly drift into risk territory over time.
Automate cleanup with expiration policies
Inactive Teams quickly become digital clutter. In Microsoft Entra ID, use Microsoft 365 Group expiration policies to automatically prompt owners to renew Teams or let them expire after a set period (for example, after 180 days).
Active Teams renew automatically, while unrenewed ones are deleted, but restorations remain possible for 30 days. This saves storage and licensing overhead, though automatic deletion can remove key project history. Auto‑archiving, while safer for records, adds cost and compliance complexities.
Use retention policies for compliance
Retention policies keep your Teams data aligned with legal, regulatory, or audit obligations, such as keeping financial records for seven years.
In the Microsoft Purview compliance portal, you can retain, delete, or both retain then delete channel messages and files after specific durations. This ensures users can’t manually delete content before policies apply, supporting GDPR, SOX, or internal rules while controlling storage growth and protecting auditability across files, chats, and meeting transcripts.
Classify data with sensitivity labels
Sensitivity labels apply automated data protection to each Team’s lifecycle. Use labels like General, Confidential, and Highly Confidential to match business security levels.
When a user selects Highly Confidential during Team creation, it can automatically restrict guest access, disable external sharing on the linked SharePoint site, and apply encryption.
Keep things simple. Labels are meant to define privacy and sharing behavior, not to create complex hierarchies.
For an end‑to‑end labeling strategy, see Syskit’s Sensitivity Labels Framework. This offers structured guidance for admins building compliant yet practical classifications. And for guidance on retention policies for compliance and sensitivity labels, see our article on Automating Microsoft Teams Governance.
Download your governance quick-start checklistProactive governance: Health checks and access reviews
“Proactive Teams governance means shifting from a set-and-forget approach to ongoing management. This means catching risks and inefficiencies before they become major headaches. Regular health checks help stop forgotten files, ownerless teams, and lurking permissions issues that jeopardize both security and productivity.”
Danijel Cizek, Product Manager Team Lead at Syskit
Ownership attestation is a must-have. Schedule quarterly ownership verification, so every Team Owner affirms the team’s continued relevance, reviews its members, and removes stale guests/inactive accounts. This keeps your environment clean and ensures someone is always responsible for each workspace.

Formal access reviews take this further. In the Microsoft Entra ID portal, configure periodic access reviews for sensitive teams. Owners are prompted to approve or deny access for each member and guest. This cycle automatically tracks who should stay, who should go, and generates compliance-ready records for audits. New AI-driven agents now help surface smart recommendations, but every access review still benefits from oversight.
Ownerless Teams are a real risk. Prevent them by enforcing a policy that every team has at least two owners. For detection, schedule PowerShell reports to query Teams without owners. Here’s a simple PowerShell example to find ownerless Teams and export the info to a CSV:
$MinOwners = 1
$out = "Teams_Owner_Audit_$(Get-Date -Format 'yyyyMMdd_HHmmss').csv"
Connect-MicrosoftTeams
$teams = Get-Team
$result = foreach ($t in $teams) {
$owners = Get-TeamUser -GroupId $t.GroupId -Role Owner
$ownerUpns = ($owners | ForEach-Object User | Where-Object { $_ }) | Select-Object -Unique
if ($ownerUpns.Count -lt $MinOwners) {
[PSCustomObject]@{
TeamDisplayName = $t.DisplayName
GroupId = $t.GroupId
TeamVisibility = $t.Visibility
TeamArchived = $t.Archived
OwnerCount = $ownerUpns.Count
Owners = ($ownerUpns -join '; ')
}
}
}
if ($result) {
$result | Sort-Object OwnerCount, TeamDisplayName | Export-Csv -Path $out -NoTypeInformation -Encoding UTF8
$result
}
Disconnect-MicrosoftTeams
After identifying ownerless teams, IT must manually contact department heads and assign owners. Microsoft’s policy now prompts active members to step up, but admins still need to validate these transitions for security and accountability.
To show the value of proactive governance, report on outcomes rather than just numbers. Highlight reductions in support tickets for lost data, a rising percentage of teams with multiple owners, and clean records in the latest security audit. Track ownership attestation completion rates and the percentage of teams passing access reviews.
Managing these checks across 100+ workspaces is labor-intensive. Tools like Syskit Point centralize reviews, automate attestation tracking, and let admins manage ownership assignments from a single dashboard. Time is saved, risks are reduced, and IT resources are freed up for more strategic tasks – it’s a win-win across your organization.
The scaling challenge: When native tools aren’t enough
As organizations grow, native Microsoft tools start to show their limits. Visibility becomes scattered, as IT teams have to toggle between Entra ID, the Teams Admin Center, SharePoint, and Purview to manage permissions, guests, and data classification.

There’s no unified dashboard, making it nearly impossible to see who has access, which teams are inactive, or where external sharing is unmonitored.
Automation, another critical need at scale, is also restricted. Policies can enforce some controls, but tasks like identifying ownerless teams, running recurring access reviews, or exporting all externally shared files still demand PowerShell scripting or cumbersome manual workflows. This complexity causes gaps in compliance and puts a heavy load on already stretched IT resources.
For enterprise IT teams, the manual burden mounts quickly. Admins spend far too much time deleting abandoned teams, chasing down proper ownership, and fixing permission errors. Team owners, meanwhile, are assigned manual access reviews they may skip, creating risks for data leaks and audit failures when no one responds.
All these operational frictions erode the value of otherwise sound governance plans, and can ultimately lead to security incidents, clutter, or regulatory fines. When you’re responsible for hundreds or thousands of workspaces, these gaps can become unmanageable.
Native tools lay a solid foundation, but large organizations can quickly outpace them. Centralization, automation, and total visibility are needed to truly stay on top of governance.
The solution: Centralized Microsoft Teams governance
Syskit Point is a centralized platform designed to take the complexity out of Microsoft Teams and Microsoft 365 governance for large organizations. It bridges the gaps that native tools leave behind by providing complete, real-time visibility across Teams, Groups, SharePoint, and more. And this all happens from a single dashboard!
With Syskit Point, you can instantly generate reports on permissions, guest users, ownerless groups, and inactive workspaces. There’s no need to jump across multiple admin centers or use PowerShell scripts, as everything you need is in one place.
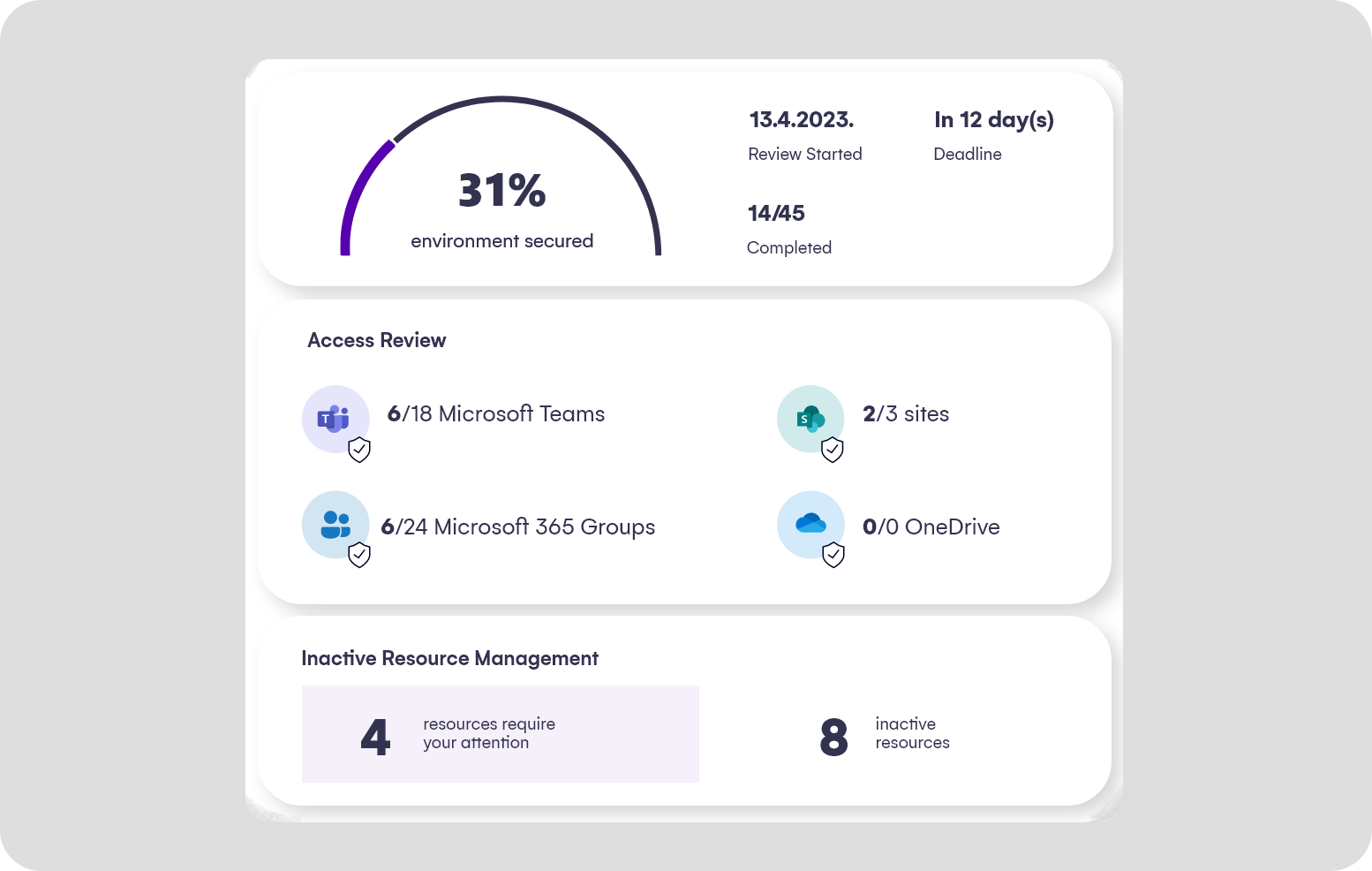
Syskit Point automates access reviews, sending reminders to owners if no action is taken. It makes cleaning up inactive or ownerless teams easy. Additionally, it standardizes workspace provisioning with templates and multistep approvals, ensuring every team follows company policy from the start., while significantly reducing the number of IT tickets.
The platform provides granular control over who has access to what and how content is shared, so you can quickly identify and fix risky sharing or misconfigurations. It provides you with the ability to easily track guests and external users, and take cleanup action immediately, if necessary.
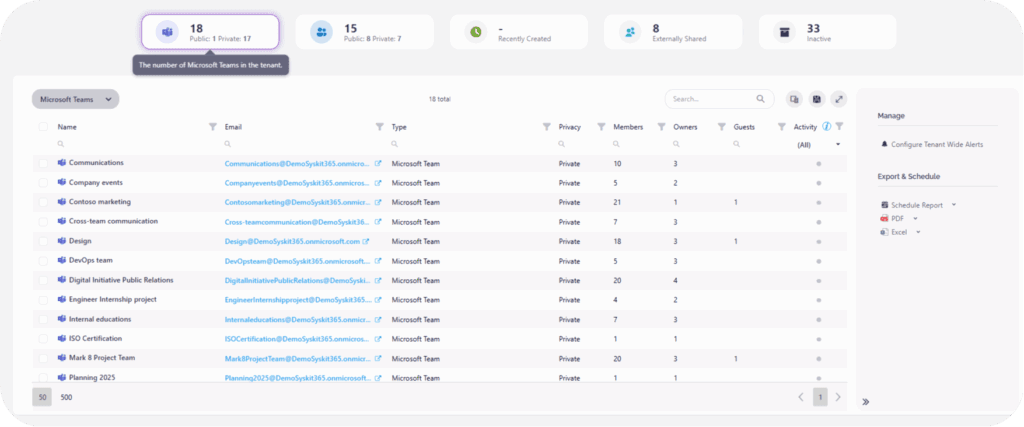
Built for practitioners, Syskit Point focuses on usability and rapid results. Onboarding is typically finished within minutes, and we’ve designed the whole platform to solve real governance pain points, helping admins reduce manual work, keep environments secure, and demonstrate measurable ROI to leadership.
Syskit Point’s value extends even further with its dedicated Teams App, which allows end-users to get a complete workspace inventory or easily request new workspaces, directly within the native Microsoft Teams interface. This user-friendly application is available as part of Syskit Point’s Governance and higher-tier plans, and can be deployed by a Teams Administrator for native integration.
While the core Syskit Point platform provides centralized and automated governance, reporting, and policy enforcement for admins, the Teams App simplifies the end-user experience. Users gain additional options for improved user adoption, decentralized provisioning, and more accessible workspace requests without sacrificing compliance or oversight.
Your governance roadmap powered by Syskit Point
Governance in Microsoft Teams should be an ongoing discipline that evolves as your organization grows. Start by using the foundational native controls outlined in this guide to achieve quick wins in structure, security, and compliance.
As Teams usage scales, you’ll notice signs of strain – fragmented visibility, growing manual workloads, and inconsistent ownership. That’s your cue to move from reactive management to proactive control with a solution built for scale.
Syskit Point consolidates oversight, automates reviews, and reports across the entire Microsoft 365 ecosystem. Beyond efficiency, the real value of governance lies in enabling secure, effortless collaboration – or teamwork that’s easy to manage and hard to misuse. With the right governance roadmap, it’s easy to control all aspects of Teams and do away with any chaos!
Explore how Syskit Point can turn your governance strategy into a practical, automated system that keeps Microsoft 365 secure and future‑ready.


